Professional Documents
Culture Documents
Ace Exam
Uploaded by
Gabriel SimatupangCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Ace Exam
Uploaded by
Gabriel SimatupangCopyright:
Available Formats
Test - Accredited Configuration Engineer (ACE) Exam - PAN-OS 6.
0 Version
ACE Exam
Question 1 of 50.
Traffic going to a public IP address is being translated by your Palo Alto Networks firewall to your servers private IP address. Which IP address should the
Security Policy use as the "Destination IP" in order to allow traffic to the server?
The firewalls MGT IP
The firewalls gateway IP
The servers public IP
The servers private IP
Mark for follow up
Question 2 of 50.
Taking into account only the information in the screenshot above, answer the following question. An administrator is pinging 4.4.4.4 and fails to receive a
response. What is the most likely reason for the lack of response?
There is a Security Policy that prevents ping
There is no Management Profile
The interface is down
There is no route back to the machine originating the ping
Mark for follow up
Question 3 of 50.
Which of the Dynamic Updates listed below are issued on a daily basis?
Global Protect
URL Filtering
Antivirus
Applications and Threats
Mark for follow up
Question 4 of 50.
In a Destination NAT configuration, the Translated Address field may be populated with either an IP address or an Address object
True False
Mark for follow up
Question 5 of 50.
Empowering People: paloaltonetworks 7/2/2014
https://paloaltonetworks.csod.com/Evaluations/EvalLaunch.aspx?loid=e971abab-e169-4145-841e-7a72a409f724&evalLvl=5&redirect_url=%2fLMS%2fUserTranscript%2fMainView.aspx 1 / 9
Taking into account only the information in the screenshot above, answer the following question. An administrator is attempting to ping 2.2.2.1. and fails to
receive a response. What is the most likely reason for the lack of response?
The interface is down
There is a security policy that prevents ping
There is no management profile
There is no route back to the machine originating the ping
Mark for follow up
Question 6 of 50.
Select the implicit rules enforced on traffic failing to match any user defined Security Policies:
Intra-zone traffic is denied
Inter-zone traffic is denied
Intra-zone traffic is allowed
Inter-zone traffic is allowed
Mark for follow up
Question 7 of 50.
Palo Alto Networks firewalls support the use of both Dynamic (built-in user roles) and Role-Based (customized user roles)
True False
Mark for follow up
Question 8 of 50.
Which of the following interface types can have an IP address assigned to it?
Layer 3
Layer 2
Vwire
TAP
Mark for follow up
Question 9 of 50.
Subsequent to the installation of a new Application and Threat database, the firewall must be rebooted
True False
Mark for follow up
Question 10 of 50.
Subsequent to the installation of a new PAN-OS version, the firewall must be rebooted
True False
Mark for follow up
Question 11 of 50.
Which mode will allow a user to choose when they wish to connect to the Global Protect Network?
On Demand mode
Optional mode
Empowering People: paloaltonetworks 7/2/2014
https://paloaltonetworks.csod.com/Evaluations/EvalLaunch.aspx?loid=e971abab-e169-4145-841e-7a72a409f724&evalLvl=5&redirect_url=%2fLMS%2fUserTranscript%2fMainView.aspx 2 / 9
Single Sign-On mode
Always On mode
Mark for follow up
Question 12 of 50.
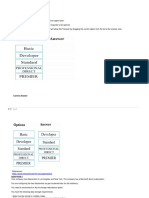
In PAN-OS 6.0, rule numbers were introduced. Rule Numbers are:
Dynamic numbers that refer to a security policys order and are especially useful when filtering security policies by tags
numbers referring to when the security policy was created and do not have a bearing on the order of policy enforcement
Static numbers that must be manually re-numbered whenever a new security policy is added.
Mark for follow up
Question 13 of 50.
When configuring Security Policies based on FQDN objects, which of the following statements are true?
The firewall resolves the FQDN first when the policy is committed, and is refreshed at TTL expiration.
In order to create FQDN-based objects, you need to manually define a list of associated IP addresses. Up to 10 IP addresses can be configured for each FQDN
entry
The firewall resolves the FQDN first when the policy is committed, and is refreshed each time Security profiles are evaluated
Mark for follow up
Question 14 of 50.
Which of the following is NOT a valid option for built-in CLI access roles?
read/write
superusers
vsysadmin
deviceadmin
Mark for follow up
Question 15 of 50.
When Network Address Translation has been performed on traffic, Destination Zones in Security Policies should be based on:
Post-NAT addresses
None of the above
Pre-NAT addresses
The same zones used in NAT rules
Mark for follow up
Question 16 of 50.
When troubleshooting Phase 1 of an IPSec VPN tunnel, which location will have the most informative logs?
Responding side, System Log
Initiating side, System log
Responding side, Traffic log
Initiating side, Traffic log
Mark for follow up
Question 17 of 50.
Which of the following options may be enabled to reduce system overhead when using Content-ID?
DSRI
RSTP
VRRP
STP
Mark for follow up
Empowering People: paloaltonetworks 7/2/2014
https://paloaltonetworks.csod.com/Evaluations/EvalLaunch.aspx?loid=e971abab-e169-4145-841e-7a72a409f724&evalLvl=5&redirect_url=%2fLMS%2fUserTranscript%2fMainView.aspx 3 / 9
Question 18 of 50.
What is the benefit realized when the "Enable Passive DNS Monitoring" checkbox is enabled on the firewall? Select all that apply
Improve PAN-DB malware detection
Improve DNS-based C&C signature
Improve malware detection in WildFire
Improve BrightCloud malware detection
Mark for follow up
Question 19 of 50.
Which of the following objects cannot use User-ID as a match criteria?
Security Policies
QoS
Policy Based Forwarding
DoS Protection
None of the above
Mark for follow up
Question 20 of 50.
Wildfire may be used for identifying which of the following types of traffic?
Malware
DNS
DHCP
URL Content
Mark for follow up
Question 21 of 50.
As the Palo Alto Networks Administrator responsible for User-ID, you need to enable mapping of network users that do not sign in via LDAP. Which information
source would allow for reliable User-ID mapping while requiring the least amount of configuration?
Exchange CAS Security logs
Active Directory Security Logs
WMI Query
Captive Portal
Mark for follow up
Question 22 of 50.
What are two sources of information for determining if the firewall has been successful in communicating with an external User-ID Agent?
System Logs and the indicator light under the User-ID Agent settings in the firewall
There's only one location - System Logs
There's only one location - Traffic Logs
System Logs and indicator light on the chassis
Mark for follow up
Question 23 of 50.
Which of the following statements about dynamic updates are correct?
Application and Antivirus updates are released weekly and Threat and Threat and URL filtering updates are released weekly
Application and Threat updates are released daily. Antivirus and URL filtering updates are released weekly.
Antivirus and URL Filtering updates are released daily. Application and Threat updates are released weekly
Threat and URL filtering updates are released daily and Application and Antivirus updates are released weekly
Mark for follow up
Empowering People: paloaltonetworks 7/2/2014
https://paloaltonetworks.csod.com/Evaluations/EvalLaunch.aspx?loid=e971abab-e169-4145-841e-7a72a409f724&evalLvl=5&redirect_url=%2fLMS%2fUserTranscript%2fMainView.aspx 4 / 9
Question 24 of 50.
Subsequent to the installation of new licenses, the firewall must be rebooted
True False
Mark for follow up
Question 25 of 50.
Which of the following most accurately describes Dynamic IP in a Source NAT configuration?
The next available address in the address range is used, and the source port number is changed
The same address is always used, and the port is unchanged
The next available address in the configured pool is used, but the port number is unchanged
None of the above
Mark for follow up
Question 26 of 50.
When an interface is in Tap mode and a policy action is set to block, the interface will send a TCP reset.
True False
Mark for follow up
Question 27 of 50.
The "Drive-By Download" protection feature, under File Blocking profiles in Content-ID, provides:
Password-protected access to specific file downloads, for authorized users
increased speed on the downloads of the allowed file types
Protection against unwanted downloads, by alerting the user with a response page indicating that s file is going to be downloaded
The Administrator the ability to leverage Authentication Profiles in order to protect against unwanted downloads
Mark for follow up
Question 28 of 50.
Which of the following would be a reason to use an XML API to communicate with a Palo Alto Networks firewall?
So that information can be pulled from other network resources for User-ID
To allow the firewall to push User-ID information to a NAC
To permit syslogging of User Identification events
Mark for follow up
Question 29 of 50.
Which link is used by an Active-Passive cluster to synchronize session information?
The Data Link
The Control Link
The Uplink
The Management Link
Mark for follow up
Question 30 of 50.
An interface in tap mode can transmit packets on the wire.
True False
Mark for follow up
Question 31 of 50.
Which of the following describes the sequence of the Global Protect agent connecting to a Gateway?
The Agent connects to the Portal obtains a list of Gateways, and connects to the Gateway with the fastest SSL response time
Empowering People: paloaltonetworks 7/2/2014
https://paloaltonetworks.csod.com/Evaluations/EvalLaunch.aspx?loid=e971abab-e169-4145-841e-7a72a409f724&evalLvl=5&redirect_url=%2fLMS%2fUserTranscript%2fMainView.aspx 5 / 9
The agent connects to the closest Gateway and sends the HIP report to the portal
The agent connects to the portal, obtains a list of gateways, and connects to the gateway with the fastest PING response time
The agent connects to the portal and randomly establishes a connection to the first available gateway
Mark for follow up
Question 32 of 50.
Taking into account only the information in the screenshot above, answer the following question. In order for ping traffic to traverse this device from e1/2 to e1/1,
what else needs to be configured? Select all that apply.
Security policy from trust zone to Internet zone that allows ping
Create the appropriate routes in the default virtual router
Security policy from Internet zone to trust zone that allows ping
Create a Management profile that allows ping. Assign that management profile to e1/1 and e1/2
Mark for follow up
Question 33 of 50.
What is the default DNS Sinkhole address used by Palo Alto Networks Firewall to cut off communication?
MGT interface address
Loopback interface address
Any one Layer 3 interface address
Localhost address
Mark for follow up
Question 34 of 50.
When configuring Admin Roles for Web UI access, what are the available access levels?
Enable and Disable only
None, Superuser, Device Administrator
Allow and Deny only
Enable, Read-Only and Disable
Mark for follow up
Question 35 of 50.
Which fields can be altered in the default Vulnerability Protection Profile?
Category
Severity
None
Mark for follow up
Question 36 of 50.
Which of the following interfaces types will have a MAC address?
Layer 3
Tap
Vwire
Layer 2
Empowering People: paloaltonetworks 7/2/2014
https://paloaltonetworks.csod.com/Evaluations/EvalLaunch.aspx?loid=e971abab-e169-4145-841e-7a72a409f724&evalLvl=5&redirect_url=%2fLMS%2fUserTranscript%2fMainView.aspx 6 / 9
Mark for follow up
Question 37 of 50.
When creating an Application filter, which of the following is true?
Excessive bandwidth may be used as a filter match criteria
they are called dynamic because they automatically adapt to new IP addresses
they are called dynamic because they will automatically include new applications from an application signature update if the new applications filter type is included
in the filter
they are used by malware
Mark for follow up
Question 38 of 50.
WildFire Analysis Reports are available for the following Operating Systems (select all that apply)
Windows XP
Windows 7
Windows 8
Mac OS-X
Mark for follow up
Question 39 of 50.
What will the user experience when browsing a Blocked hacking website such as www.2600.com via Google Translator?
The URL filtering policy to Block is enforced
It will be translated successfully
It will be redirected to www.2600.com
User will get "HTTP Error 503 - Service unavailable" message
Mark for follow up
Question 40 of 50.
What option should be configured when using User-ID
Enable User-ID per zone
Enable User-ID per interface
Enable User-ID per Security Policy
None of the above
Mark for follow up
Question 41 of 50.
What is the default setting for 'Action' in a Decryption Policy's rule?
no-decrypt
decrypt
any
none
Mark for follow up
Question 42 of 50.
When using remote authentication for users (LDAP, Radius, AD, etc),what must be done to allow a user to authenticate through multiple methods?
This can not be done. A single user can only use one authentication type
Create multiple authentication profiles for the same user.
Create an Authentication Sequence, dictating the order of authentication profiles
This can not be done. Although multiple authentication methods exist, a firewall must choose a single, global authentication type, and all users must use this
method
Mark for follow up
Empowering People: paloaltonetworks 7/2/2014
https://paloaltonetworks.csod.com/Evaluations/EvalLaunch.aspx?loid=e971abab-e169-4145-841e-7a72a409f724&evalLvl=5&redirect_url=%2fLMS%2fUserTranscript%2fMainView.aspx 7 / 9
Question 43 of 50.
Which of the following platforms supports the Decryption Port Mirror function?
PA-VM300
PA-4000
PA-3000
PA-2000
Mark for follow up
Question 44 of 50.
As the Palo Alto Networks Administrator you have enabled Application Block pages. Afterward, some users do not receive web-based feedback for all denied
applications. What is the cause?
Application Block Pages will only be displayed when users attempt to access a denied web-based application
Application Block Pages will only be displayed when Captive Portal is configured
Some users are accessing the Palo Alto Networks firewall through a virtual system that does not have Application Block Pages enabled
Some Application ID's are set with a Session Timeout value that is too low
Mark for follow up
Question 45 of 50.
With IKE, each device is identified to the other by a Peer ID. In most cases, this is just the public IP address of the device. In situations where the public ID is not
static, this value can be replaced with a domain name or other text value
True False
Mark for follow up
Question 46 of 50.
In PAN-OS, how is Wildfire enabled?
Via the "Forward" and "Continue and Forward" File-Blocking actions
Via the URL-Filtering "Continue" action
Wildfire is automatically enabled with a valid URL-Filtering license
A custom file blocking action must be enabled for all PDF and PE type files
Mark for follow up
Question 47 of 50.
How do you limit the amount of information recorded in the URL Content Filtering Logs?
Enable "Log container page only"
Disable URL packet captures
Enable URL log caching
Enable DSRI
Mark for follow up
Question 48 of 50.
In which of the following objects can User-ID be used to provide a match condition?
Security Policies
NAT Policies
Zone Protection Policies
Threat Profiles
Mark for follow up
Question 49 of 50.
When configuring a Decryption Policy, which of the following are available as matching criteria in a policy? (Choose 3)
Source Zone
Empowering People: paloaltonetworks 7/2/2014
https://paloaltonetworks.csod.com/Evaluations/EvalLaunch.aspx?loid=e971abab-e169-4145-841e-7a72a409f724&evalLvl=5&redirect_url=%2fLMS%2fUserTranscript%2fMainView.aspx 8 / 9
Source User
Service
URL-Category
Application
Mark for follow up
Question 50 of 50.
Which of the following are methods HA clusters use to identify network outages?
Path and Link Monitoring
VR and VSys Monitors
Heartbeat and Session Monitors
Link and Session Monitors
Mark for follow up
Save / Return Later Summary
Empowering People: paloaltonetworks 7/2/2014
https://paloaltonetworks.csod.com/Evaluations/EvalLaunch.aspx?loid=e971abab-e169-4145-841e-7a72a409f724&evalLvl=5&redirect_url=%2fLMS%2fUserTranscript%2fMainView.aspx 9 / 9
You might also like
- ACEDocument9 pagesACEJohn Sergio Mendoza MalaverNo ratings yet
- Empowering People: ACE Exam Review QuestionsDocument16 pagesEmpowering People: ACE Exam Review Questionscavoi1980No ratings yet
- Ace 7.0Document7 pagesAce 7.0Roy50% (6)
- Test - Accredited Configuration Engineer (ACE) Exam - PAN-OS 7.0 VersionDocument9 pagesTest - Accredited Configuration Engineer (ACE) Exam - PAN-OS 7.0 VersiongustavoNo ratings yet
- Test - Accredited Configuration Engineer (ACE) Exam - PAN-OS 7.0 VersionDocument13 pagesTest - Accredited Configuration Engineer (ACE) Exam - PAN-OS 7.0 VersiongustavoNo ratings yet
- ACE7 - Exam 1of5Document14 pagesACE7 - Exam 1of5Sanrioo JpNo ratings yet
- Test - Accredited Configuration Engineer (ACE) Exam - PAN-OS 7.0 VersionDocument13 pagesTest - Accredited Configuration Engineer (ACE) Exam - PAN-OS 7.0 VersiongustavoNo ratings yet
- Accredited Configuration Engineer (ACE) Exam - PAN-OS 6.0 VersionDocument18 pagesAccredited Configuration Engineer (ACE) Exam - PAN-OS 6.0 Versionvijoynew5233No ratings yet
- Palo AnswersDocument9 pagesPalo Answerseric0% (3)
- Test - Accredited Configuration Engineer (ACE) Exam - PAN-OS 7.0Document15 pagesTest - Accredited Configuration Engineer (ACE) Exam - PAN-OS 7.0Mauricio CamposNo ratings yet
- Test Palo Alto Ver 7 ACEDocument14 pagesTest Palo Alto Ver 7 ACEMulyana InfNo ratings yet
- PAN ACE7.0 100% PassDocument112 pagesPAN ACE7.0 100% PassRobert Martin87% (31)
- ACE Exam 6Document18 pagesACE Exam 6nickNo ratings yet
- Test Accredited Configuration Engineer (ACE) Exam PANOS 8.0 VersionDocument9 pagesTest Accredited Configuration Engineer (ACE) Exam PANOS 8.0 Versionba3157% (23)
- Accredited Configuration Engineer (ACE) Exam - PAN-OS 7.0 VersionDocument12 pagesAccredited Configuration Engineer (ACE) Exam - PAN-OS 7.0 VersionBillAlwaysNo ratings yet
- Test - Accredited Configuration Engineer (ACE) Exam - PAN-OS 5.0 VersionDocument20 pagesTest - Accredited Configuration Engineer (ACE) Exam - PAN-OS 5.0 Versioninvincible2k0% (1)
- Test Accredited Configuration Engineer (ACE) Exam: PANOS 8.0 VersionDocument9 pagesTest Accredited Configuration Engineer (ACE) Exam: PANOS 8.0 Versionba3150% (12)
- Examen ACE 84%Document2 pagesExamen ACE 84%Maria PastorNo ratings yet
- PCNSE Practice QuestionsDocument19 pagesPCNSE Practice QuestionsgurungeNo ratings yet
- Examen ACE 86%Document2 pagesExamen ACE 86%Maria PastorNo ratings yet
- Practice Question Palo AltoDocument20 pagesPractice Question Palo AltoCarlos Ivan Donoso Osorio0% (1)
- FortiGate 7.4 Operator Exam - Attempt Review 4Document14 pagesFortiGate 7.4 Operator Exam - Attempt Review 4Ibarra Carmona Emilio JesúsNo ratings yet
- Test Accredited Configuration Engineer ACE Exam PANOS 8 0 VersionDocument12 pagesTest Accredited Configuration Engineer ACE Exam PANOS 8 0 VersionMunfed Rana83% (23)
- CompTIA Security+ Exam SY0-601 Practice QuestionsDocument51 pagesCompTIA Security+ Exam SY0-601 Practice Questionswahyuningastuti_82No ratings yet
- Check Point Certified Security Administrator 156-215.80 (CCSA R80) 2017-12-08Document77 pagesCheck Point Certified Security Administrator 156-215.80 (CCSA R80) 2017-12-08awdNo ratings yet
- PCNSEDocument95 pagesPCNSEanon_721082701100% (1)
- Checkpoint R80Document122 pagesCheckpoint R80Çhipsis ChipereNo ratings yet
- Vendor: Palo Alto Networks Exam Code: PCNSE Exam Name: Palo Alto Networks Certified Security EngineerDocument113 pagesVendor: Palo Alto Networks Exam Code: PCNSE Exam Name: Palo Alto Networks Certified Security EngineerNour Ibba100% (2)
- NSE4 Dumps - 301 Q&As from CertleaderDocument14 pagesNSE4 Dumps - 301 Q&As from CertleaderAkram QasemNo ratings yet
- Checkpoint Certification Exam Questions 156-80 Enero 2020Document200 pagesCheckpoint Certification Exam Questions 156-80 Enero 2020rulohb83No ratings yet
- CompTIA PracticeTest SY0-401 v2016-08-12Document233 pagesCompTIA PracticeTest SY0-401 v2016-08-12Nikhil SharmaNo ratings yet
- NSE 4 Sample Exam 6Document22 pagesNSE 4 Sample Exam 6novalk23No ratings yet
- 00 CCSA TestDocument276 pages00 CCSA TestPedro CubillaNo ratings yet
- 8.checkpoint Firewall Interview QuestionsDocument7 pages8.checkpoint Firewall Interview Questionsnagendra_badam100% (1)
- Palo Alto Networks - Testking.PCNSE7.v2016-09-07.by - Pierre.51qDocument36 pagesPalo Alto Networks - Testking.PCNSE7.v2016-09-07.by - Pierre.51qCyrille IKOUMNo ratings yet
- Paloaltonetworks - Pcnse.V2022-01-18.Q127: Show AnswerDocument49 pagesPaloaltonetworks - Pcnse.V2022-01-18.Q127: Show AnswerMecachis PiachisNo ratings yet
- Ujian Associate 2Document11 pagesUjian Associate 2angga permana25% (4)
- PCNSE v9 (2020) PDFDocument77 pagesPCNSE v9 (2020) PDFKo HtetNo ratings yet
- Pse - 1Document9 pagesPse - 1Phước Nguyễn Hữu83% (6)
- NSE 4 7.0 Sample Questions - Attempt ReviewDocument15 pagesNSE 4 7.0 Sample Questions - Attempt ReviewEnzo MoralesNo ratings yet
- 156-215.80 ExamDocument227 pages156-215.80 ExamPt sinergi teknologi BersatuNo ratings yet
- Gotocert Latest NSE6 Dumps PDF Training Materials SharedDocument8 pagesGotocert Latest NSE6 Dumps PDF Training Materials SharedZachary K. MukaNo ratings yet
- 156-315 80Document63 pages156-315 80Djambo MatamorosNo ratings yet
- CompTIA Premium SY0-401 v2016-04-11 by VCEplus 200q1752qDocument150 pagesCompTIA Premium SY0-401 v2016-04-11 by VCEplus 200q1752qAkanksha VermaNo ratings yet
- CASP+ CompTIA Advanced Security Practitioner Study Guide: Exam CAS-004From EverandCASP+ CompTIA Advanced Security Practitioner Study Guide: Exam CAS-004No ratings yet
- SSL VPN : Understanding, evaluating and planning secure, web-based remote accessFrom EverandSSL VPN : Understanding, evaluating and planning secure, web-based remote accessNo ratings yet
- SSCP (ISC)2 Systems Security Certified Practitioner Official Study GuideFrom EverandSSCP (ISC)2 Systems Security Certified Practitioner Official Study GuideNo ratings yet
- Security Operations Center - Analyst Guide: SIEM Technology, Use Cases and PracticesFrom EverandSecurity Operations Center - Analyst Guide: SIEM Technology, Use Cases and PracticesRating: 4 out of 5 stars4/5 (1)
- WAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksFrom EverandWAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksNo ratings yet
- Plant Intelligent Automation and Digital Transformation: Volume I: Process and Factory AutomationFrom EverandPlant Intelligent Automation and Digital Transformation: Volume I: Process and Factory AutomationNo ratings yet
- Auditing Cloud Computing: A Security and Privacy GuideFrom EverandAuditing Cloud Computing: A Security and Privacy GuideRating: 3 out of 5 stars3/5 (2)
- CVD Getvpndesignguide Aug13Document40 pagesCVD Getvpndesignguide Aug13Gabriel SimatupangNo ratings yet
- Barracuda Email Security Service SB Office365 Exchange 2013 USDocument2 pagesBarracuda Email Security Service SB Office365 Exchange 2013 USGabriel SimatupangNo ratings yet
- Cisco Lan SwitchingDocument797 pagesCisco Lan SwitchingJoe KayNo ratings yet
- Perintah Lubuntu ServerDocument4 pagesPerintah Lubuntu ServerGabriel SimatupangNo ratings yet
- Cisco Switch Catos IOS Configuration CommandsDocument42 pagesCisco Switch Catos IOS Configuration Commandsshogun7333No ratings yet
- Perintah Lubuntu ServerDocument4 pagesPerintah Lubuntu ServerGabriel SimatupangNo ratings yet
- Video Streaming395Document12 pagesVideo Streaming395sanathdNo ratings yet
- Inter Mountain ElectricDocument2 pagesInter Mountain ElectricGabriel SimatupangNo ratings yet
- IP Address Guide: Types, Classes, Versions & MoreDocument18 pagesIP Address Guide: Types, Classes, Versions & MoreAnonymous cs4BLczENo ratings yet
- Project Manager in TelecommunicationsDocument2 pagesProject Manager in Telecommunicationsapi-79112020No ratings yet
- Embedded WiFi Kit Quick Guide PDFDocument8 pagesEmbedded WiFi Kit Quick Guide PDFJaviNo ratings yet
- UMTS and LTE Dynamic Power Sharing (SRAN17.1 - 01)Document44 pagesUMTS and LTE Dynamic Power Sharing (SRAN17.1 - 01)freveco111No ratings yet
- VIRDI AC5000 Installation GuideDocument20 pagesVIRDI AC5000 Installation Guidecarlos sousaNo ratings yet
- Chap 4 - Digital Communication System For Communication EngineeringDocument47 pagesChap 4 - Digital Communication System For Communication Engineeringmiz_student9067% (3)
- Communication Interface Technology PDFDocument2 pagesCommunication Interface Technology PDFDariusNo ratings yet
- Brksec 3697 PDFDocument292 pagesBrksec 3697 PDFprakashrjsekarNo ratings yet
- Satellite DishDocument1 pageSatellite DishPhilip NalanganNo ratings yet
- Ios LogsDocument24 pagesIos LogsmandeepmailsNo ratings yet
- 2.thiet bị RBS - 6201Document22 pages2.thiet bị RBS - 6201tamNo ratings yet
- 2.1.1.5 Packet Tracer - Create A Simple Network Using Packet Tracer PDFDocument15 pages2.1.1.5 Packet Tracer - Create A Simple Network Using Packet Tracer PDFTeixeira JorgeNo ratings yet
- NIS2 Versus ISO27001 - 2022 Versus CIS v8Document5 pagesNIS2 Versus ISO27001 - 2022 Versus CIS v8Vagabond PakistanNo ratings yet
- Nokia Digital Optical Network Unit (ONU) Mobile Application User GuideDocument38 pagesNokia Digital Optical Network Unit (ONU) Mobile Application User GuidercpawarNo ratings yet
- Network Training GuideDocument33 pagesNetwork Training Guidesunny5670jNo ratings yet
- WP Software Defined NetworkingDocument8 pagesWP Software Defined Networkingmore_nerdyNo ratings yet
- Ocb 283 - General Description-Bsnl TrainingDocument55 pagesOcb 283 - General Description-Bsnl Trainingsihabek83% (6)
- Subdomain EnumerationDocument7 pagesSubdomain EnumerationPortia SorianoNo ratings yet
- Gr1230 CoreDocument276 pagesGr1230 CoreSanjay YadavNo ratings yet
- 3G UL-DL Capacity Monitoring V1.0Document55 pages3G UL-DL Capacity Monitoring V1.0Denmark Wilson100% (1)
- ALA - SECURITEX - PARADOX - EVO192-Technical - BrochureDocument4 pagesALA - SECURITEX - PARADOX - EVO192-Technical - BrochureEliel LopesNo ratings yet
- Realtek: RTD 2271W / 2281W Family Dual-Input LCD Display Controller Brief SpecDocument14 pagesRealtek: RTD 2271W / 2281W Family Dual-Input LCD Display Controller Brief SpecAcronix SolucionesNo ratings yet
- Pay As You Go (Pay As You Go 1 Tariff) Airtime Agreement and Charges (From February 2021)Document11 pagesPay As You Go (Pay As You Go 1 Tariff) Airtime Agreement and Charges (From February 2021)jesiennyliscNo ratings yet
- GPS Ceramic Patch Antenna Data SheetDocument6 pagesGPS Ceramic Patch Antenna Data SheetPanagos PanagiotisNo ratings yet
- AZ-900 33 Additional Questions-Dec2021Document21 pagesAZ-900 33 Additional Questions-Dec2021Fernando GebhardtNo ratings yet
- Diplexor E11F02P02Document3 pagesDiplexor E11F02P02angicarNo ratings yet
- Cs-637 - Wireless CommunicationsDocument2 pagesCs-637 - Wireless CommunicationsBalaKrishna KesaniNo ratings yet
- Win Dump HwidDocument18 pagesWin Dump HwidWing Chung ChanNo ratings yet
- Hitachi CDH-LE40SMART06 SKYWORTH Chassis 6M82BDocument28 pagesHitachi CDH-LE40SMART06 SKYWORTH Chassis 6M82BOrlando Chanampa100% (1)
- Term Paper On GrameenphoneDocument4 pagesTerm Paper On Grameenphonec5p9zbep100% (1)