Professional Documents
Culture Documents
The Best Security Defense? A Good Offense
Uploaded by
IDG_WorldCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
The Best Security Defense? A Good Offense
Uploaded by
IDG_WorldCopyright:
Available Formats
The Best Security Defense?
A Good Offense
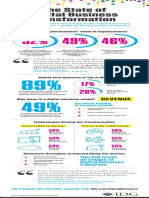
Organizations Are Constantly Playing Defense
Security
incidents
are on
the
rise
8,640
9,156
SMB
<1,000
employees
Enterprise
3,577
1,000+
employees
2014
Mobile
2015
693
2014
2015
But only
23%
is a leading
cause of
security
incidents.
1.
Top 3
causes of
security
incidents
say securing
mobile devices is a top
priority in the next year.
Mobile
device
exploitation
2.
Embedded
system
exploitation
3.
Consumer
technology
exploitation
Business Execs Finally Come Off the Sidelines
73%
of orgs have senior execs
who proactively communicate
the importance of InfoSec
to the entire organization
49%
54%
36%
have a CSO
in charge of the
security program
have a CISO
in charge of the
security program
of CSOs/CISOs
report directly
to the CEO
The Security Playbook: Frameworks
81%
Most common frameworks
for the Enterprise
1
follow a risk-based
framework/support
structure or guide
ISO 27001
2 NIST Cybersecurity Framework
3 SANs Critical Controls
49%
47%
Adopting
frameworks
has allowed
for better
identification
and prioritizing
of security risks.
Are better able
to quickly detect
and mitigate
security incidents
after adopting
a risk-based
framework.
Calling an Audible: New Technologies
Leveraged in Cybersecurity Strategies
Cloud
Internet of Things
70%
45%
of organizations
use cloud-based security services
to help ensure data security/privacy.
are implementing or plan
to implement a security
strategy for securing IoT
in the next 12 months.
36%
59%
currently have
a security
strategy for
IoT in place.
of enterprise organizations use
cloud-based security for real-time
time monitoring and analytics.
Big Data
65%
of enterprises leverage
big data analytics to
improve cybersecurity
1/
3
1/
3
23%
51%
have in
place
14%
in place, but
outsourced
of those received advanced
warning of cyber incidents
as a result of big data-driven
security capabilities.
of those prevented security
incidents as a result of having
big data-driven security capabilities.
of enterprises say employing big data analytics
to model for and identify information security
incidents is a top priority in the next 12 months.
Whats the biggest
challenge to implementing
big data intiatives?
Too much data
(38% of respondents agree)
Advanced Authentication:
Passcode
the next 12 months
Advanced
Authentication
technologies are
expected to grow,
especially for
mobile devices.
44%
multifactor
authentication
41%
say its a
priority
50%
plan to
implement
smartphone
tokens.
already have
smartphone tokens
Its a Team Effort: Organizations Go on Offense
65%
of organizations
are collaborating with
others in their industry
to improve security.
45%
of boards participate in the
overall security strategy.
In 2015, information
security budgets
were boosted by
24%
Source: The 2016 Global State of Information Security Survey, in partnership with PwC, CIO, and CSO, October 2015
For more information visit
idgenterprise.com/contact-us
IDGenterprise.com/resource-type/research
You might also like
- 2018 State of The Network InfographicDocument1 page2018 State of The Network InfographicIDG_WorldNo ratings yet
- 2018 IDG Security Priorities SurveyDocument9 pages2018 IDG Security Priorities SurveyIDG_WorldNo ratings yet
- 2018 IDG Security Priorities InfographicDocument1 page2018 IDG Security Priorities InfographicIDG_WorldNo ratings yet
- 2018 U.S. State of Cybercrime SurveyDocument9 pages2018 U.S. State of Cybercrime SurveyIDG_WorldNo ratings yet
- CIOs Are Driving Digital Transformation InfographicDocument1 pageCIOs Are Driving Digital Transformation InfographicIDG_WorldNo ratings yet
- 2018 CIO Tech Poll: Economic OutlookDocument8 pages2018 CIO Tech Poll: Economic OutlookIDG_World100% (1)
- IDG 2018 Cloud Computing ResearchDocument8 pagesIDG 2018 Cloud Computing ResearchIDG_World100% (4)
- State of The Network 2018Document10 pagesState of The Network 2018IDG_WorldNo ratings yet
- 2018 IDG Cloud Computing InfographicDocument1 page2018 IDG Cloud Computing InfographicIDG_WorldNo ratings yet
- CIO Tech Poll: Tech Priorities 2018Document7 pagesCIO Tech Poll: Tech Priorities 2018IDG_WorldNo ratings yet
- A Guide To Understanding How Organizations Are Evolving To A Digital-First Business ModelDocument1 pageA Guide To Understanding How Organizations Are Evolving To A Digital-First Business ModelIDG_WorldNo ratings yet
- 2018 CIO Tech Poll: Economic Outlook InfographicDocument1 page2018 CIO Tech Poll: Economic Outlook InfographicIDG_WorldNo ratings yet
- Digital Disruption & The NetworkDocument1 pageDigital Disruption & The NetworkIDG_WorldNo ratings yet
- State of The CIO 2018Document9 pagesState of The CIO 2018IDG_WorldNo ratings yet
- 2018 Global State of Information Security SurveyDocument9 pages2018 Global State of Information Security SurveyIDG_WorldNo ratings yet
- IDG 2017 Security Priorities StudyDocument8 pagesIDG 2017 Security Priorities StudyIDG_WorldNo ratings yet
- 2018 IDG Digital Business SurveyDocument9 pages2018 IDG Digital Business SurveyIDG_World100% (3)
- 2017 CIO Tech Poll: Economic OutlookDocument6 pages2017 CIO Tech Poll: Economic OutlookIDG_WorldNo ratings yet
- 2017 U.S. State of Cybercrime SurveyDocument8 pages2017 U.S. State of Cybercrime SurveyIDG_WorldNo ratings yet
- 2017 IDG Customer Engagement ExcerptDocument8 pages2017 IDG Customer Engagement ExcerptIDG_WorldNo ratings yet
- CSO 2016 SIEM Vendor Scorecard ResearchDocument7 pagesCSO 2016 SIEM Vendor Scorecard ResearchIDG_WorldNo ratings yet
- 2017 Customer Engagment Sample SlidesDocument8 pages2017 Customer Engagment Sample SlidesIDG_WorldNo ratings yet
- State of The Network 2017Document8 pagesState of The Network 2017IDG_WorldNo ratings yet
- CW Forecast 2017 SampleDocument8 pagesCW Forecast 2017 SampleIDG_World100% (1)
- Demand GenerationDocument9 pagesDemand GenerationIDG_World100% (1)
- 2017 Global State of Information Security SurveyDocument7 pages2017 Global State of Information Security SurveyIDG_World100% (1)
- Tech Priorities 2017 SampleDocument7 pagesTech Priorities 2017 SampleIDG_WorldNo ratings yet
- State of The CIO 2017Document9 pagesState of The CIO 2017IDG_World100% (1)
- The Connection Between Security and Data & AnalyticsDocument1 pageThe Connection Between Security and Data & AnalyticsIDG_World100% (1)
- Today's Cloud Focus & MotivatorsDocument1 pageToday's Cloud Focus & MotivatorsIDG_World100% (2)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5782)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (890)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (537)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (265)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (399)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (838)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (587)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (72)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (344)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2219)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (119)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (821)
- HG Las Q1 W2 Hawking RamosDocument3 pagesHG Las Q1 W2 Hawking RamosSecond Subscriber100% (1)
- Common Mistakes That Singles Make: EncounterDocument33 pagesCommon Mistakes That Singles Make: EncounterMadeleine BayaniNo ratings yet
- 2020-07-01consumer Reports - July 2020 (USA)Document81 pages2020-07-01consumer Reports - July 2020 (USA)enock-readersNo ratings yet
- Chartist Movement of BritainDocument6 pagesChartist Movement of BritainAbhishek Kumar100% (1)
- Types of Grading SchemesDocument11 pagesTypes of Grading SchemesGrenalyn De la Mar100% (1)
- 1-Day Val D'orcia & Tuscany Ferrari Tour: A New Travel ConceptDocument4 pages1-Day Val D'orcia & Tuscany Ferrari Tour: A New Travel ConceptEla2305No ratings yet
- Ramadan by Ahmad JibrilDocument26 pagesRamadan by Ahmad JibrilSharifNo ratings yet
- Peugeot Landtrek Pen Malaysia Price List 200323Document2 pagesPeugeot Landtrek Pen Malaysia Price List 200323Azly M SabinNo ratings yet
- Sustainable Expatriate ManagementDocument12 pagesSustainable Expatriate ManagementLee JordanNo ratings yet
- Project ProposalDocument2 pagesProject ProposalsandraNo ratings yet
- KANVA MART SWOT AnalysisDocument15 pagesKANVA MART SWOT AnalysisSanthosh 8055No ratings yet
- It Didn't Start ....Document16 pagesIt Didn't Start ....tigerlo7513% (53)
- 2017 Bradley Ledford Deposition AND MORE Madison David Cawthorn Vs Auto Owners Insurance Company 11-2017 PDFDocument446 pages2017 Bradley Ledford Deposition AND MORE Madison David Cawthorn Vs Auto Owners Insurance Company 11-2017 PDFClub4GrowthActionPACK100% (2)
- Emilio Gentile. Political Religion - A Concept and Its Critics - A Critical SurveyDocument15 pagesEmilio Gentile. Political Religion - A Concept and Its Critics - A Critical SurveyDeznan Bogdan100% (1)
- Distilleries & BaveriesDocument8 pagesDistilleries & Baveriespreyog Equipments100% (1)
- Arguments over caring and authenticity erupt at gatheringDocument4 pagesArguments over caring and authenticity erupt at gatheringAngieNo ratings yet
- The Essentials Off Procure-To-Pay: EbookDocument10 pagesThe Essentials Off Procure-To-Pay: EbookSurendra PNo ratings yet
- Johns Hopkins Safety Manual: HSE 028 Emergency Response at JHHDocument10 pagesJohns Hopkins Safety Manual: HSE 028 Emergency Response at JHHmuthuswamy77No ratings yet
- Care for Your Circulatory and Respiratory HealthDocument2 pagesCare for Your Circulatory and Respiratory HealthJamila ManonggiringNo ratings yet
- Lesson Plan BALLB Law of EvidenceDocument15 pagesLesson Plan BALLB Law of EvidenceNiti KaushikNo ratings yet
- Bilbao Attacking PhaseDocument169 pagesBilbao Attacking PhaseMiguel Angel Carreño Martinez100% (3)
- 1.SPA SSS Death BenefitsDocument1 page1.SPA SSS Death BenefitsTroy Suello0% (1)
- Introduction To The Boston MatrixDocument2 pagesIntroduction To The Boston MatrixAshokkumar JoshiNo ratings yet
- Boris v. Thomson Healthcare Inc. - Document No. 5Document4 pagesBoris v. Thomson Healthcare Inc. - Document No. 5Justia.comNo ratings yet
- Insights into InsightDocument4 pagesInsights into InsightSantoz MilanistiNo ratings yet
- 80-100Tph Tin Stone Crushing LineDocument3 pages80-100Tph Tin Stone Crushing LineМаксим СтратилаNo ratings yet
- 12 - Fulton Iron Works Vs China BankingDocument6 pages12 - Fulton Iron Works Vs China BankingRaiden DalusagNo ratings yet
- General Education 2008 With AnswersDocument19 pagesGeneral Education 2008 With AnswersjenniferespanolNo ratings yet
- Take A Multicultural Metropolis Like LondonDocument11 pagesTake A Multicultural Metropolis Like LondonSerife MazlumNo ratings yet
- INDUS WATERS TREATY KEY TO PAK-INDIA WATER SHARINGDocument21 pagesINDUS WATERS TREATY KEY TO PAK-INDIA WATER SHARINGAzhar AhmadNo ratings yet