Professional Documents
Culture Documents
Lost Iphone? Lost Passwords!
Uploaded by
MaxVinicius0 ratings0% found this document useful (0 votes)
21 views7 pagesWritten by: Jens Heider, Matthias Boll (SIT)
Original Title
Lost iPhone? Lost Passwords!
Copyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentWritten by: Jens Heider, Matthias Boll (SIT)
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
21 views7 pagesLost Iphone? Lost Passwords!
Uploaded by
MaxViniciusWritten by: Jens Heider, Matthias Boll (SIT)
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
You are on page 1of 7
Lost iPhone? Lost Passwords!
Practical Consideration of iOS
Device Encryption Security
Jens Heider, Matthias Boll
Fraunhofer Institute for
Secure Information Technology (SIT)
February 9, 2011
See "iOS Keychain Weakness FAQ"
for updated information:
http://sit4.me/iphone-keychain-faq
Abstract
The paper highlights risks that accompany losing a locked iOS device regarding
condentiality of passwords stored in the keychain. It presents results of hands-
on tests that show the possibility for attackers to reveal some of the keychain
entries. For the described approach, the knowledge of the users secret pass-
code is not needed, as the protection provided by the passcode is bypassed.
1 Introduction
During many discussions about security of iOS devices (iPhone, iPad) we have
recognized that the public perception of protection strength provided by the
iOS device encryption does not reect all aspects of the security for stored
passwords, which we consider important. Therefore, this paper is intended to
point out related facts, which were elaborated by hands-on tests to clarify the
strength of the protection in a lost device scenario.
When an iOS device with hardware encryption capabilities is lost or stolen,
many users believe that there is no way for a new owner to access the stored
data at least if a strong passcode
1
is in place. This estimation is comprehen-
sible, since in theory the cryptographic strength of the AES-256 algorithm used
for iOS device encryption should prevent even well equipped attackers. How-
ever, it was already shown
2
that it is possible to access great portions of the
stored data without knowing the passcode. Tools are available for this tasks
that require only small effort. This is done by tricking the operating system to
decrypt the le system on behalf of the attacker. This decryption is possible,
since on current
3
iOS devices the required cryptographic key does not depend
on the users secret passcode. Instead the required key material is completely
created from data available within the device and therefore is also in the posses-
sion of a possible attacker.
Less considered is the aspect that, as an extension to the ability to decrypt the
le system, an attacker may aim at gaining access to stored secrets kept in the
keychain. Therefore, the impact of extending the known iOS weaknesses by
targeting the keychain security should be shown in this paper.
In current versions of iOS, the keychain contains user accounts including pass-
words such as email, groupware, VPN, WiFi, websites and often also passwords
and certicates used in 3rd party apps. As these secrets are stored encrypted in
the keychain, the questions is: Which key is used for the encryption and which
practical barrier does it create for an attacker with access to the device.
1 A user-dened secret that has to be entered to unlock the device
2 See e.g., http://www.zdziarski.com/blog/?p=516
3 As of this writing this refers to iOS rmware 4.2.1
Fraunhofer SIT
Lost iPhone? Lost Passwords!
3
2 Scenario Setup
For evaluating the practical strength of iOS device encryption security, we as-
sume an attacker with physical access to the device, e.g. accomplished by theft
or when nding a lost device. The assumed device is protected with a strong
passcode, which is unknown to the attacker. The complexity of the passcode
does not play a role for this evaluation, but is assumed to prevent an attacker
from gaining access by simply guessing. Also, it is assumed that the device has
not been jailbroken and so all original iOS protection mechanisms are in place.
When the device is found, it is assumed to be in the locked
4
state with acti-
vated data protection
5
. An unlocked device would provide the possibilities for
user space exploits and could reveal more secrets. However, this leakage could
not be accounted to the protection mechanism we wanted to evaluate.
The attackers PC used to gain access to passwords has not been synchronized
with the attacked device before. Therefore no secrets can be used by the at-
tacker that are created between the owners PC and his device.
In the described situation, device encryption commonly should provide protec-
tion against attacks from the outside. If the device is still turned on e.g., not
run out of battery meanwhile , we assume that no remote wipe
6
command
was received in the meantime (e.g, theft remained unnoticed, no network con-
nection, etc.). In any case, the attacker turns off the device and removes the
SIM card to prevent a further remote control.
In this described state, we have conducted our tests with iPhone 4 and iPad
Wi-Fi+3G hardware with the latest rmware 4.2.1.
3 Approach
We have conducted various hands-on tests to evaluate which secrets can be re-
vealed from the keychain and how much effort this might take an attacker. We
focused on gaining access to the key used for the keychain encryption without
having to open the device and without having to know the users passcode. As
we assumed that the operating system does have access to this key, we have
chosen to access the operating system via an alternative boot procedure.
4 The enter password dialog is shown when trying to wake or power up device.
5 A feature of iOS 4 to put an extra layer of security on some stored data. See http://su
pport.apple.com/kb/HT4175
6 A feature of iOS 4 to remotly remove the cryptographic key via MS Exchange or with the
service mobile me from a device. See http://manuals.info.apple.com/en_
US/Enterprise_Deployment_Guide.pdf
4
Fraunhofer SIT
Lost iPhone? Lost Passwords!
In the following, we describe the general approach we use to access the key-
chain. An additional video
7
illustrates the necessary interaction between PC and
iPhone. The intention is to provide enough insides to enable others to under-
stand and evaluate the impact of the observed security design. On the other
hand, we will not disclose the created script nor other details to prevent too
much benets for the wrong hands.
The general approach we take can be summarized in three steps:
1. Getting access to the le system.
2. Coping keychain access script to le system.
3. Execute script which reveals stored accounts and secrets
The rst step is needed to be able to access the keychain database. This step de-
pends on the devices iOS version and hardware but in general can be achieved
with a jailbreaking tool and by installing an SSH server on the device without
overwriting user data. Now software can be launched unrestricted on the de-
vice. This way the software can access all les including the keychain database.
Secrets in this database are encrypted with the devices key, which could not be
extracted from the device. However, the key can be used from software within
the device.
In the second step, we copy our keychain access script to the device via the SSH
connection. It uses system functions to access the keychain entries, which made
it not necessary to reverse engineer the encryption mechanism of the keychain
items.
The last step executes the script, which outputs the found accounts to the shell
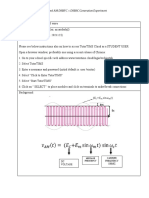
screen. A sample output of the script is shown in Figure 1. Secrets that can not
be decrypted by the system would be reported as (null).
4 Results
After using a jailbreaking tool, to get access to a command shell, we run a small
script to access and decrypt the passwords found in the keychain. The decryp-
tion is done with the help of functions provided by the operating system itself.
Our script reveals the always unencrypted settings (e.g., user name, server, etc.)
for all stored accounts. For the account types marked "w/o passcode" in Ta-
ble 1, also the accounts cleartext secrets are revealed. This indicates, that an at-
tacker would not need to know the users passcode nor does he would need to
exploit new vulnerabilities to reveal these secrets. The results were taken from
a passcode protected and locked iPhone 4 with current rmware 4.2.1. The
7 See http://www.sit.fraunhofer.de/forschungsbereiche/projekte/
Lost_iPhone.jsp
Fraunhofer SIT
Lost iPhone? Lost Passwords!
5
Figure 1:
Screenshot of Proof of Concept approach with truncated Output of revealed Passwords
overall approach takes six minutes, which might provide an additional opportu-
nity for an attacker to return the device to the owner to cover the revealing of
passwords.
Secrets within other protection classes, such as passwords for websites, could
not be revealed in our lost device scenario. In our proof of concept implemen-
tation, these secrets marked "protected" in Table 1 were available to the
script only after entering the passcode to unlock the device, which by assump-
tion should not be possible for an attacker. However, note that in many situa-
tions it is sufcient for an attacker to gain access to the users email account for
abusing the password recovery processes of many other accounts.
The accessibility of keychain secrets without requiring the passcode is consid-
ered a result of a trade-off between system security and usage convenience:
The passwords for network related services should be available directly from
device startup, without having to enter the passcode rst. In consequence the
knowledge of the users passcode is also not necessary for an attacker with ac-
cess to the le system.
Further considerations are needed for the revealed service passwords such as
Voicemail, iChat or Mobile me. The impact on these services and the possibili-
ties that can be gained by attackers will be addressed in future research.
5 Conclusion
The results show that a lost iOS device may endanger also the condentiality of
data that is not stored on the device, but which is accessible for an attacker via
the revealed stored secrets. This is not specically a problem only to iOS devices,
as other smartphone operating systems may also have circumventable password
6
Fraunhofer SIT
Lost iPhone? Lost Passwords!
Table 1: Test Results regarding Availability of Secrets to Attackers in the Lost Device Scenario
Tested Account Types Secret Type Accessibility
AOL Email Password protected
Apple Push Certicate + Token w/o passcode
Apps using keychain with default protection depends on App protected
Apple-token-sync (mobile me) Token w/o passcode
CalDav Password w/o passcode
Generic IMAP Password protected
Generic SMTP server Password protected
Google Mail Password protected
Google Mail as MS Exchange Account Password w/o passcode
iChat.VeniceRegistrationAgent Token w/o passcode
iOS Backup Password Password protected
LDAP Password w/o passcode
Lockdown Daemon Certicate w/o passcode
MS Exchange Password w/o passcode
Voicemail Password w/o passcode
VPN IPsec Shared Secret Password w/o passcode
VPN XAuth Password Password w/o passcode
VPN PPP Password Password w/o passcode
Website Account from Safari Password protected
WiFi (Company WPA with LEAP) Password w/o passcode
WiFi WPA Password w/o passcode
Yahoo Email Token + Cookie protected
protection mechanisms. However, iOS devices with device encryption may keep
users in false believe that these devices have in general a strong password pro-
tection in place.
Regrading the iOS compliance to individual enterprise security policies, espe-
cially the sometimes applied comparison to fully encrypted notebook harddisks
with pre-boot authenticaion is not valid, since these systems use the users se-
cret for the device encryption. Instead for iOS devices, the protection of vulnera-
ble account types listed in Table 1 and great portions of other stored data
are not bound to the knowledge of the users passcode.
We judge the effort for the shown attack method as low, since the used jail-
breaking tools are freely available and the additional steps to decrypt the key-
chain requires only moderate programming skills.
Owners of a lost or stolen iOS device should therefore instantly initiate a change
of all stored passwords. Additionally, this should be also done for accounts not
stored on the device but which might have equal or similar passwords, as an at-
tacker might try out revealed passwords against the full list of known accounts.
Enterprises should create efcient processes for lost device incidents to shorten
the time during which their accounts may be vulnerable. Especially the change
of group passwords like sometimes used for VPN and WiFi may require an addi-
tional effort but should be taken seriously.
Fraunhofer SIT
Lost iPhone? Lost Passwords!
7
You might also like
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (537)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (587)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (894)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (399)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (73)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5794)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (838)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1090)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2219)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (344)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (265)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (119)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (821)
- Datasheet 40-91025-2 en 120V 60HzDocument4 pagesDatasheet 40-91025-2 en 120V 60HzVulpe FlorianNo ratings yet
- Alsatom Su100m - Su100mb - Service ManualDocument13 pagesAlsatom Su100m - Su100mb - Service ManualEdithMardonesTroncoso100% (1)
- k-300 PDVSA INSTRUMENTATION INTRODUCTIONDocument10 pagesk-300 PDVSA INSTRUMENTATION INTRODUCTIONrodolforfNo ratings yet
- Topper 2 110 1 2 Chemistry Questions Up201506182029 1434639560 4018Document5 pagesTopper 2 110 1 2 Chemistry Questions Up201506182029 1434639560 4018Ananthakrishnan Tinneveli VNo ratings yet
- FXNQ-A 4PEN393318-1C Installation Manuals EnglishDocument16 pagesFXNQ-A 4PEN393318-1C Installation Manuals EnglishGeorge TziotisNo ratings yet
- Siemens Arcadis Avantic Installations LaserIIDocument22 pagesSiemens Arcadis Avantic Installations LaserIINelson AltuveNo ratings yet
- Pratt & Whitney Engine Services FAST Configuration for Cessna Grand Caravan EXDocument24 pagesPratt & Whitney Engine Services FAST Configuration for Cessna Grand Caravan EXatony357No ratings yet
- Installation Manual 3ats, 3adts, 3Nts, 3Ndts G-Design 1600-3200 A Transfer SwitchesDocument8 pagesInstallation Manual 3ats, 3adts, 3Nts, 3Ndts G-Design 1600-3200 A Transfer SwitchesMahmoud M.AbdelalimNo ratings yet
- Mikro Cat 2018Document76 pagesMikro Cat 2018Janitha Hettiarachchi0% (1)
- SR ml20 30 40a User Manual PDFDocument11 pagesSR ml20 30 40a User Manual PDFnick21070No ratings yet
- Experiment-1 Title: Diode As Clipper & Clamper Circuit ObjectivesDocument11 pagesExperiment-1 Title: Diode As Clipper & Clamper Circuit ObjectivesGPA Innovation LabNo ratings yet
- Java Fire Alarm SystemDocument3 pagesJava Fire Alarm SystemKomal KashyapNo ratings yet
- LM-380EZ Instruction ManualDocument61 pagesLM-380EZ Instruction ManualCongNo ratings yet
- Department of Electrical Engineering (New Campus) : LAB 5: JFET and MOSFET (DC Biasing Review)Document10 pagesDepartment of Electrical Engineering (New Campus) : LAB 5: JFET and MOSFET (DC Biasing Review)syed furqan javedNo ratings yet
- C100 Service Training Manual: 3.2L Engine Mechanical Participant HandbookDocument54 pagesC100 Service Training Manual: 3.2L Engine Mechanical Participant Handbooksertex_jo83% (6)
- Datasheet: Samsung Emmc Movinand Product FamilyDocument25 pagesDatasheet: Samsung Emmc Movinand Product FamilyFady AllDoikNo ratings yet
- Wireless Power Transmission Circuit and Its WorkingDocument12 pagesWireless Power Transmission Circuit and Its Workingfiledownload643No ratings yet
- 12Document16 pages12Idraki SariyanNo ratings yet
- Automotive Applications of EMPTDocument7 pagesAutomotive Applications of EMPTrovichmaNo ratings yet
- LG Case StudyDocument3 pagesLG Case Studygtdas24No ratings yet
- Sony kv2199m5j kv-j21mf2j Chassis bg-2sDocument36 pagesSony kv2199m5j kv-j21mf2j Chassis bg-2sBandula Senevirathna100% (1)
- Ds Parani Sd1000Document2 pagesDs Parani Sd1000crystalng5259No ratings yet
- Comparison Kodak Vs Sony IIMSDocument108 pagesComparison Kodak Vs Sony IIMSAshish BhallaNo ratings yet
- Embedded Systems Programming in C and ARM AssemblyDocument44 pagesEmbedded Systems Programming in C and ARM AssemblyNoura BaccarNo ratings yet
- SY-8100 Manual OperacionDocument36 pagesSY-8100 Manual OperacionJOse ArmentaNo ratings yet
- Information Coding Techniques Question BankDocument10 pagesInformation Coding Techniques Question BankManikandan ArunachalamNo ratings yet
- PSpice Simulation of Basic DC CircuitsDocument11 pagesPSpice Simulation of Basic DC CircuitsArifuzzamanFaisalNo ratings yet
- Simulation Activity 1 DSBFC and DSBSCDocument6 pagesSimulation Activity 1 DSBFC and DSBSCDennis ANo ratings yet
- Solve yarn breaks and maximize profits with Muratec's Pac21 winding systemDocument22 pagesSolve yarn breaks and maximize profits with Muratec's Pac21 winding systemShahjad Mansuri85% (26)
- A Study On Market Segmentation of Samsung Electronics Ltd. With Special References To Mobile PhonesDocument6 pagesA Study On Market Segmentation of Samsung Electronics Ltd. With Special References To Mobile PhonesAgus Ari SanjayaNo ratings yet