Professional Documents
Culture Documents
Jntu Online Examinations (Mid 2 - MC)
Uploaded by
Sai Sadiq0 ratings0% found this document useful (0 votes)
14 views20 pagesBlue tooth device can form a network with a devices within a distance of a about 10 m a.Pico net b.Nano net c.Micro net d.Internet d.Intranet. Bluetooth is a.Connectionless protocol b.Connected oriented protocol c.Security protocol d.internet protocol 11.
Original Description:
Original Title
mc2midUandiStar
Copyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentBlue tooth device can form a network with a devices within a distance of a about 10 m a.Pico net b.Nano net c.Micro net d.Internet d.Intranet. Bluetooth is a.Connectionless protocol b.Connected oriented protocol c.Security protocol d.internet protocol 11.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
14 views20 pagesJntu Online Examinations (Mid 2 - MC)
Uploaded by
Sai SadiqBlue tooth device can form a network with a devices within a distance of a about 10 m a.Pico net b.Nano net c.Micro net d.Internet d.Intranet. Bluetooth is a.Connectionless protocol b.Connected oriented protocol c.Security protocol d.internet protocol 11.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
You are on page 1of 20
JNTU ONLINE EXAMINATIONS [Mid 2 - MC]
1. The following sequence defines one channel
a.Hopping
b.Linear
c.Fibonacci
d.Conditional move
2. The following synchronizes all active devices
a.Master
b.Slave
c.Sibling
d.Child
3. The device which first establishes a Pico net becomes
a.Master
b.Slave
c.Sibling
d.Child
4. The device which discovers the master becomes
a.Master
b.Slave
c.Sibling
d.Child
5. The clock of master functions is reference for synchronization in
a.Master
b.Slave
c.Sibling
d.Child
6. Blue tooth device can form a network with a devices within a distance of a about
10 m
a.Pico net
b.Nano net
c.Micro net
d.Internet
7. Various Pico nets form an Adhoc network called
a.Scatter net
b.Pico net
c.Internet
d.Intranet
8. Protocol for transport layer in Bluetooth is
a.MESI
b.OBEX
c.TORA
d.TCP
9. OBEX stands for
a.Bluetooth object exchange
b.Object expertise
c.Object extension
d.Object extent
10. Bluetooth is
a.Connectionless protocol
b.Connection oriented protocol
c.Security protocol
d.Internet protocol
11. Downlink is from
www.studentshangout.com
www.studentshangout.com
a.Devices to server
b.Server to devices
c.Any direction
d.Between satellites only
12. Bandwidth in downstream is the following to upstream
a.Smaller
b.Larger
c.Equal
d.No way related with bandwidth
13. In the following connection is asymmetric
a.I mode
b.WAP
c.Blue tooth
d.Hyperlan
14. Mobile communication between mobile device and static computer system is
a.Symmetric
b.Asymmetric
c.Fast
d.Clear
15. Communication from server to device is
a.Uplink
b.Downlink
c.Caching
d.Dissemination
16. The following is the transmission of data packets in a computer network such
that a single destination receives the packets
a.Unicast
b.Multicast
c.Broadcast
d.Dual cast
17. Mobile TV is an example for
a.Unicast
b.Multicast
c.Broadcast
d.Dual cast
18. The mobile device is allocated
a.Limited bandwidth
b.Unlimited bandwidth
c.Limited time
d.Unlimited time
19. Bandwidth in downstream from server to device is
a.
b.
c.
d.
20. GSM
Much larger than the one in upstream from the device
Much smaller than the one in upstream from the device
Almost equal to upstream from the device
No way concerned with the upstream
is used only for
a.Voice communication
b.Multimedia
c.Internet
d.i mode
21. The following context defined the interrelation between time and the occurrence
of an event or action
a.
b.
c.
Physical
Computing
User
www.studentshangout.com
www.studentshangout.com
d.Temporal
22. Context of VUI defines the following context
a.Physical
b.Computing
c.User
d.Temporal
23. During daytime the display brightness is increased is of the following context
a.Physical
b.Computing
c.User
d.Temporal
24. The following computing is defined by inter relationships and conditions oc
network connectivity protocol
a.Physical
b.Computing
c.User
d.Temporal
25. The following context is defines user location, user profile
a.Physical
b.Computing
c.User
d.Temporal
26. Power resources at mobile devices are
a.Limited
b.Unlimited
c.Unmanageable
d.Vast
27. The following reduces the power requirements as it reduces the number of
packets or packets for transmission
a.Aggregation
b.Allocation
c.Availability
d.Association
28. The following takes independent world view and does not require components to
have global view of the system
a.Implicit context
b.Explicit context
c.Power computing
d.Web data consistency
29. The following computing leads to application aware computing
a.Power aware
b.Context aware
c.Client server
d.Web
30. Context helps in
a.Reducing ambiguity in actions
b.Increasing ambiguity in actions
c.Reducing unambiguity in actions
d.Independent actions
31. The copies cached at the devices are equivalent to the following at the
processors in a multiprocessor system with a shared memory
a.
b.
c.
d.
main memory'
Cache memory
Secondary memory
Semaphore
www.studentshangout.com
www.studentshangout.com
32. Server load is reduced by
a.
b.
c.
d.
33. Cost
Prefetching
Profiling
Dissemination
Recovery
based data replacement method is
a.Caching
b.Prefetching
c.Profiling
d.Dissemination
34. Through the following cost of cache-misses can be reduced
a.
b.
c.
d.
35. Cost
a.
Caching
Prefetching
Profiling
Dissemination
of cache-misses refers to
Time taken in accessing record at server in case that the record is not
found
b.Time taken in accessing record at server in case that the record is found
c.Time taken in caching
d.Time taken in recovery
36. Access probabilities of each record and its comparisons with probabilities of
other records are
a.Predictable in wireless environment
b.Unpredictable in wireless environment
c.Stable in wireless environment
d.Coherent in wireless environment
37. The following entails requesting for and pulling records that may be required
later
a.Caching
b.Perfecting
c.Processing
d.Profiling
38. The following can prefetch instead of caching from the pushed records keeping
future needs in view
a.Client device
b.Server
c.Base station
d.TORA
39. Caching of pushed data leads to
a.Reduced access interval
b.Increased access interval
c.No way related with access interval
d.Increases the dependence on pushing procedure at the server
40. The hot records are
a.
b.
c.
d.
41. QNX
Empty records
Most needed database records at client device
Rarely used database records at client device
Null records
is
AN RTOS based on UNIX
UNIX OS only
Runtime stack
Microcontroller
supports
a.
b.
c.
d.
42. DB2e
www.studentshangout.com
www.studentshangout.com
a.
b.
c.
d.
43. DB2e
Only mobile device OS
Only handheld OS
Both mobile device and hand held OS
Servers only
supports databases of size up to
a.64 KB
b.256 KB
c.120 MB
d.1 GB
44. If the data record is modified at the server then the copy of that record at client
device also changes accordingly .This phenomenon is
a.Concurrency
b.Synchronization
c.Parallel processing
d.Morphing
45. Symbian V6 is example for
a.Mobile device OS
b.Handheld computer OS
c.Mainframe OS
d.Linux OS
46. Database hoarding may be done
a.At the application tier itself
b.Any tier
c.Server only
d.Base station only
47. Downloading ring tone is example of database stored in the following
architecture
a.
b.
c.
d.
48. DB2e
a.
b.
c.
d.
49. DB2e
1-tier
2- tier
3-tier
n-tier
is
Relational database engine
Data maintenance engine
Query processor
Recovery manager
stands for
a.IBM DB2 every day
b.IBM DB2 every place
c.Apple DB2 every click
d.Apple DB2 event object
50. The following has been designed to reside at the device
a.IBM DB2 every day
b.IBM DB2 every place
c.Apple DB2 every click
d.Apple DB2 event object
51. Ending of a tagged data record is specified by
a.Tag
b.Record
c.Query
d.Recovery
52. The following is a tag with a slash sign before the tag
a.
b.
c.
Tag
Record
Query
www.studentshangout.com
www.studentshangout.com
d.Recovery
53. XML databases incorporate the following business logic
a.Implicit
b.Explicit
c.external
d.Dummy
54. The key used to search for a record is the following in XML database
a.Tag
b.Record
c.Query
d.Recovery
55. The following is present between the tag and the end tag in XML
a.Tag
b.Record
c.Query
d.Recovery
56. The logic of transactions is among the following when comes from within the
database
a.Implicit
b.Explicit
c.external
d.Dummy
57. The following requires no external definition for the business logic to function
a.Implicit
b.Explicit
c.external
d.Dummy
58. The data stored in database follows
a.Logic
b.Order
c.Table
d.Sets
59. Stored queries and procedures define business logic
a.Implicit
b.Explicit
c.external
d.Dummy
60. The transaction between the API and the database uses an explicitly defined
a.Query
b.Algorithm
c.Procedure
d.Sorting method
61. The following mechanism provides for adaptively to pull in case of an urgent
need
a.Push based
b.Pull based
c.Hybrid
d.Query based
62. The following mechanism provides for adaptation to pull in case when a data
record pushed from server is missed
a.Push based
b.Pull based
c.Hybrid
d.Query based
63. In advertising and selling music albums the advertisements are
www.studentshangout.com
www.studentshangout.com
a.Pushed
b.Pulled
c.On demanded
d.Time constrained
64. In the following hardware is shared and adapted between the two channels
a.Push based
b.Pull based
c.Hybrid
d.Query based
65. Pushed records are chopped adaptively if the number of pull requests is
a.Increased
b.Decreased
c.Nullifies
d.Equalized
66. In the following mechanism there are two channels
a.Push based
b.Pull based
c.Hybrid
d.Query based
67. The following mechanism integrates pushes and pull
a.Push based
b.Pull based
c.Hybrid
d.Query based
68. The following mechanism is also known as IPP mechanism
a.Push based
b.Pull based
c.Hybrid
d.Query based
69. The back channel in IPP mechanism is used to send the following for records
a.Pull requests
b.Pushed data
c.Algorithms for broadcast disks
d.Publish subscribed data
70. Example of hybrid mechanism in distributed computing system is
a.Weather reports
b.Ring tone servers
c.Advertising and setting music albums
d.Stock quotes
71. Indexing increases
a.Time taken for tuning
b.Access latency
c.Power consumption
d.Data consistency
72. Increased access latency is due to
a.More pushed items
b.Less pushed items
c.No way related with the pushed items
d.Power resources
73. Broadcast cycle is extended in the following method
a.
b.
c.
d.
Directory method
Hash based method
Index based method
Distributed based method
www.studentshangout.com
www.studentshangout.com
74. During the time intervals in which unsolicited data is being broadcasted, the
device remains
a.Idle
b.Active
c.Power on mode
d.Toggle state
75. The following reduces the time taken for tuning by client devices
a.Indexing
b.Prefetching
c.Hashing
d.Profiling
76. The following temporally maps the location of buckets
a.Indexes
b.Keys
c.Hash
d.Directory
77. The value to be used by the device along with present location and calculate the
period of or tuning to next bucket
a.Offset
b.Base
c.Register
d.Indexed value
78. All buckets have the following to the beginning of the next indexed bucket
a.Offset
b.Base
c.Register
d.Indexed value
79. The following is a technique in which each data bucket is assigned an index at
the previous data bucket to enable the device to tune and cache the bucket after
the wait as per the offset value
a.
b.
c.
d.
80. taccess
a.
b.
c.
d.
81. Train
Indexing
Prefetching
Hashing
Profiling
is increased in the following method
Directory method
Hash based method
Index based method
Distributed based method
schedules in a railway time table is an example for
a.Data caching
b.Data entropy
c.Data mining
d.Data delivery
82. Retrieving required data from the database server during each computation is
a.Practically very easy
b.Impractical
c.Efficient
d.Faster
83. The following entails saving a copy of select data or part of database from the
connected system with a large database
a.
b.
c.
d.
Servers
Networks
Remote computing systems
Mobile devices
www.studentshangout.com
www.studentshangout.com
84. In mobile device database the cached data is
a.Hoarded
b.Triggered
c.Toggled
d.Trembled
85. The following of the cached data in the database ensuring that even when the
device is in disconnected mode, the data required from the database is available
for computing
a.Hoarded
b.Triggered
c.Toggled
d.Trembled
86. A mobile device cannot store a large database due to
a.Memory constraints
b.Small size
c.Pocket size
d.Handy size
87. A mobile device is the following to server
a.Always connected
b.Not always connected
c.Always coupled
d.Not always visible
88. In mobile computing large databases are not available on
a.Servers
b.Networks
c.Remote computing systems
d.Mobile devices
89. The following caches some specific data, which may be required for further
computations
a.Servers
b.Networks
c.Remote computing systems
d.Mobile devices
90. The following takes place during the interval in which the device is connected to
the server or network
a.Caching
b.Dissemination
c.Quality of service
d.Query processing
91. The device cache or server has rewritten a database recor5d which can be
shared and used for computations comes under the following state
a.Exclusive
b.Shared
c.Modified
d.Invalidation
92. A mechanism to ensure that a database record is identical at the server as well
as at the device cache and that only cache records are used for computations in
a.
b.
c.
d.
93. Each
a.
b.
c.
Cache inconsistency
Cache coherence
Cache concurrency
Cache invalidation
record in cache is called
cache-line
cache-record
cache-file
www.studentshangout.com
www.studentshangout.com
d.cache-layout
94. Cache invalidation mechanism follows the following protocol
a.Cache access protocol
b.MESI
c.DSR
d.DVR
95. The server data base no longer has a copy of the record which can be shared and
used for computation earlier comes under the following state
a.Exclusive
b.Shared
c.Modified
d.Invalidation
96. The following at the client device may be invalidated
a.Cache record
b.Shared memory
c.Semaphore
d.Application
97. The following may be due to expiry or modification of record at the database
server
a.Validation
b.Invalidation
c.Prefetching
d.Caching
98. The following is a process by which a cached data item or record becomes
invalid
a.Cache validation
b.Cache invalidation
c.Prefetching
d.Profiling
99. Invalidation means
a.Unusable
b.Reusable
c.Usable
d.Reentrant
100.The following mechanism is means by which the server conveys invalid
information to client devices
a.
b.
c.
d.
101.
a.
b.
c.
d.
102.
a.
b.
c.
d.
103.
a.
b.
c.
d.
Cache validation
Cache invalidation
Prefetching
Profiling
MANETS are
Supervised
Self organized
Self inhibited
Self multiplied
In MANETS the number of routers may
Increase only
Decrease only
Increase or decrease
No routers at all
MANETS stands for
Multiple accesses net
Mobile Adhoc net
Mobile access net
Multiple Adhoc net
www.studentshangout.com
www.studentshangout.com
104.
a.
b.
c.
d.
105.
The following network is not usable in operations like disaster relief
Fixed infrastructure
MANETS
VANETS
Adhoc nets
The following networks are self organized
a.Fixed infrastructure
b.LAN
c.Mobile Adhoc networks
d.WAN
106.The following network has access points, base stations or gateways
networked together using switches, hubs or routers
a.
b.
c.
d.
107.
a.
b.
c.
d.
108.
Fixed infrastructure
MANETS
VANETS
Adhoc nets
Example for fixed infrastructure network is
Cellular network
Bluetooth
Wi-fi
MANETS
The location of switches, hubs or router is mobile in
a.Fixed infrastructure
b.LAN
c.Mobile Adhoc networks
d.WAN
109.The number of routers available at any instant can increase or decrease in
the following network
a.
b.
c.
d.
110.
a.
b.
c.
d.
111.
copy
a.
b.
c.
d.
112.
Fixed infrastructure
LAN
Mobile Adhoc networks
WAN
The available routing path may change in the following network
Fixed infrastructure
LAN
Mobile Adhoc networks
WAN
Client devices presume that as long as there is no invalidation report, the
is valid for use in computations in the following approach
Stateless
Stateful
Synchronous
Asynchronous
Asynchronous mechanism has
a.More band width
b.Less band width
c.Frequent unnecessary data report transfers
d.No way related with the bandwidth
113.No frequent unnecessary transfers of data reports are present in the
following approach
a.
b.
c.
d.
114.
Stateless
Stateful
Synchronous
Asynchronous
The following makes more bandwidth efficient
www.studentshangout.com
www.studentshangout.com
a.Stateless
b.Stateful
c.Synchronous
d.Asynchronous
115.Whether the client requires invalidation report or not but every client
device gets an invalidation report under the following approach
a.
b.
c.
d.
116.
to all
Stateless
Stateful
Synchronous
Asynchronous
The following mechanism entails broadcasting of the invalidation of cache
the clients of server
a.Stateless
b.Stateful
c.Synchronous
d.Asynchronous
117.The following mechanism entails cache invalidation reports are sent only
to the affected client devices and not broadcasted to all
a.Stateless
b.Stateful
c.Synchronous
d.Asynchronous
118.In the following mechanism the server doesn t keep track of the records
stored at the device caches
a.Stateless Asynchronous
b.Stateless synchronous
c.Stateful Asynchronous
d.Stateful synchronous
119.The following indicates that the invalidation information for an item is sent
as soon as its value changes
a.
b.
c.
d.
120.
a.
b.
c.
d.
121.
a.
b.
c.
d.
122.
a.
b.
c.
d.
123.
a.
b.
c.
d.
124.
Stateless
Stateful
Synchronous
Asynchronous
The server advertises the following
Invalidation information
Modifies the cache records
Memory capacity
Time speed
Classical internet IPV4 addresses are made up of
32 bits
64 bits
128 bits
256 bits
IPV6 addresses are of
32 bits
64 bits
128 bits
256 bits
Access point is not required in
Fixed infrastructure
LAN
Mobile Adhoc networks
WAN
IPV6 is used for
www.studentshangout.com
www.studentshangout.com
a.
b.
c.
d.
125.
a.
b.
c.
d.
126.
than
a.
b.
c.
d.
127.
a.
b.
c.
d.
128.
a.
b.
c.
d.
129.
a.
b.
c.
d.
130.
a.
b.
c.
d.
131.
Internet radio over the internet
Real time video over the internet only
Both internet radio and real time video over the internet only
Movie making
Examples of integration of mobile phones with IPv4 and IPV6
CDMA handsets and Apple iphone
Nokia and Samsung
Sony Ericson
China mobile phones
The following mode has much smaller frequency spectrum requirements
that for a node in fixed infrastructure network
Fixed infrastructure
LAN
Mobile Adhoc networks
WAN
VANETs stand for
Vehicular Adhoc network
Vertical Adhoc network
Verbal Adhoc network
Virtual Adhoc network
The following network enables fast establishment of networks
Fixed infrastructure
LAN
Mobile Adhoc networks
WAN
The following nodes have peer to peer connectivity among themselves
Fixed infrastructure
LAN
Mobile Adhoc networks
WAN
The wireless connectivity range in MANETS include
Only nearest node connectivity
Only largest node connectivity
To some specified range
No limit to connectivity
Score of world cup football match is
a.Hot records
b.Temporal
c.Context
d.Power computing
132.In the following mechanism the number of server interruptions may
increase
a.Push based
b.Pull based
c.Hybrid
d.Query based
133.When the server has very little contention the following mechanism is
better
a.Push based
b.Pull based
c.Hybrid
d.Query based
134.If the server respond to many device requests within expected time
interval the following mechanism is better
a. Push based
www.studentshangout.com
www.studentshangout.com
b.
c.
d.
135.
Pull based
Hybrid
Query based
Records changing with time are called as
a.Hot records
b.Temporal
c.Context
d.Power computing
136.The following pulls the data records from service provider's application
databases server in a pull based mechanism
a.User device
b.Server
c.Base station
d.Gateway
137.Records are pulled by the mobile devices on demand in the following
mechanism
a.
b.
c.
d.
138.
a.
b.
c.
d.
139.
Push based
Pull based
Hybrid
Query based
The following mode is also known as on-demand mode
push based
Pull based
Hybrid
Query based
Number of server interruptions can be controlled by
a.Pull threshold
b.Time
c.Speed
d.Vacancy
140.No unsolicited or irrelevant data arrives at the device in the following
mechanism
a.
b.
c.
d.
141.
Push based
Pull based
Hybrid
Query based
Pushing the data only once
a.Saves bandwidth
b.Ensures guarantee of data even disconnected at the time of pushing
c.Saves burden of selection
d.Can be performed
142.The following mechanism is best option for the server as they present
server overload
a.Push based
b.Pull based
c.Hybrid
d.Query based
143.The following is not example of distributed computing system in push
based mechanism
a.Generators of traffic congestion
b.Weather reports
c.Stock quotes
d.Ring tones server
144.In the following data records are pushed to mobile devices by
broadcasting
www.studentshangout.com
www.studentshangout.com
a.Push based
b.Pull based
c.Hybrid
d.Query based
145.In push based data is pushed at selected time intervals using the following
algorithm
a.
b.
c.
d.
146.
a.
b.
c.
d.
147.
MESI
Adaptive
TORA
ELIZA
Push based data delivery mechanism can also be called as
Publish subscribe mode
On demand
Hybrid
Power based
On demand mode is done in the following mechanism
a.Push based
b.Pull based
c.Hybrid
d.Query based
148.Publish subscribe mode delivery mechanism is done in the following data
delivery mechanism
a.Push based
b.Pull based
c.Hybrid
d.Query based
149.Advertisers is example for the following mechanism in distributed
computing systems
a.Push based
b.Pull based
c.Hybrid
d.Query based
150.The data is pushed as per the subscription for push service by a user in the
following mechanism
a.
b.
c.
d.
151.
Push based
Pull based
Hybrid
Query based
When the process starts, initially the following is given in header
a.Source address
b.Destination address
c.care of address
d.Home agent
152.The following is generated when a disconnection occurs during
transmission from a node to its neighbor
a.
b.
c.
d.
153.
a.
b.
c.
d.
154.
Route error packet
Route request
Route acknowledgement
Route initialization
Routing packets to a single destinated address is
Unicasting
Broadcasting
Bidirectional
Multicasting
The deletion of link shown in a table or cache is called
www.studentshangout.com
www.studentshangout.com
a.
b.
c.
d.
155.
a.
b.
c.
d.
156.
a.
b.
c.
d.
157.
a.
b.
c.
d.
158.
a.
b.
c.
d.
159.
only
a.
b.
c.
d.
160.
Link traversal
Link reversal
Link approval
Link enhancement
DSR uses
Flooding
Flowing
Spooling
Spoofing
The following protocol deploys source routing
DSR
AODV
CGSR
TORA
Each data packet includes the routing node address in
Source routing
Distance routing
On demand routing
Link routing
DSR is
Reactive
Proactive
Hierarchical
Inactive
The following protocol reacts to the changes and dynamically maintains
the routing addresses from source to destination in
DSR
AODV
CGSR
TORA
DSR performs
a.Unicasing
b.Broadcasting
c.Bidirectional
d.Multicasting
161.In the following method broadcasting contain a fewer bits compared to
key and record separately
a.
b.
c.
d.
162.
a.
b.
c.
d.
163.
Directory method
Hash based method
Index based method
Distributed based method
In the hash based method hash is broadcasted from
server
Client
Mobile device
Foreign agent
Time taken by the device for selection of record is
a.Tuning time
b.Access time
c.Latency time
d.Sorting time
164.Cache miss occurs if the following time is longer than the time period
between two instants of repeating the directory before the broadcasts of records
a.
b.
Tuning time
Access time
www.studentshangout.com
www.studentshangout.com
c.
d.
165.
Latency time
Sorting time
The following is the result of operations on pair of key and record
a.Hash
b.Array
c.Function
d.Structure
166.The following is a process by which client device selects only the required
pushed buckets, tunes to them and caches them
a.
b.
c.
d.
167.
a.
b.
c.
d.
168.
a.
b.
c.
d.
169.
Selective tuning
Indexing
Sorting
Highlighting
Getting ready for caching when selected record of interest broadcasts is
Tuning
Indexing
Profiling
Perfecting
The following has a structure and overhead
Broad cast data
Hot record
Query
File
The data broadcasted from the following is interleaved
a.server
b.Mobile device
c.Application program
d.Base station
170.The following method involves broadcasting a directory as over at the
beginning of each broadcast cycle
a.Directory method
b.Hash based method
c.Index based method
d.Distributed based method
171.The following doesnot exchange hello message periodically to listen to
disconnected links
a.DSR
b.AODV
c.CGSR
d.TORA
172.The following does exchange hello message periodically to listen to
disconnected links
a.
b.
c.
d.
173.
a.
b.
c.
d.
174.
a.
b.
c.
DSR
AODV
CGSR
TORA
The following guarantees hopfree routes
DSR
AODV
CGSR
TORA
TORA supports
unidirectional links
bidirectional links
dummy links
www.studentshangout.com
www.studentshangout.com
d.
175.
a.
b.
c.
d.
176.
Adhoc links
TORA provides
only provides one path
multiple routing paths
distance vector paths
spanning paths
TORA is
a.reactive
b.proactive
c.hierarchial
d.inactive
177.The following is employed for highly dynamic MANETS and provides an
improved partial link reversal process
a.DSR
b.AODV
c.CGSR
d.TORA
178.The following routing algorithm has the feature of stopping the non-
productive link reversals in a given portion of the network
a.
b.
c.
d.
179.
DSR
AODV
CGSR
TORA
Graph having one input path and one outgoing path is
a.acrylic
b.Euler
c.Hamiltanean
d.planar
180.The following posses network capacity such that many nodes can send
packets to a given destination
a.
b.
c.
d.
181.
a.
b.
c.
d.
182.
DSR
AODV
CGSR
TORA
The following transactions are caused due to network failure
Aborted
Ignoring
Retrying
Escape
In query processing the symbol represents
a.Projection
b.Selection
c.Alteration
d.Modification
183.In the following two transactions are carried out simultaneously there
should not be any interference between the two
a.Atomicity
b.Consistency
c.Isolation
d.Durability
184.The read operation of a new state starts only after the write operation of
previous state is completed in
a.
b.
c.
Atomicity
Consistency
Serializable Isolation
www.studentshangout.com
www.studentshangout.com
d.Durability
185.In the following after a transaction is completed, the transaction must
persist and can t be aborted or discarded
a.Atomicity
b.Consistency
c.Serializable Isolation
d.Durability
186.The execution of interrelated instructions in a sequence for a specific
operation on a database is
a.
b.
c.
d.
187.
Transaction
Query
Recovery
Data maintenance
Data base transaction model enforce the following rules
a.ACID
b.MESI
c.TORA
d.CODD
188.All operations must be complete comes under the following rule in the
transaction model
a.
b.
c.
d.
189.
Atomicity
Consistency
Isolation
Durability
If the transaction cannot be completed then it must be
a.Quitted
b.Rolled back
c.Submitted
d.Committed
190.The data is not in a contradictory state after the transaction comes under
the following rule
a.
b.
c.
d.
191.
a.
b.
c.
d.
192.
layer
a.
b.
c.
d.
193.
WAP
a.
b.
c.
d.
194.
a.
b.
Atomicity
Consistency
Isolation
Durability
The following code binds with WSP for connectivity to the internet
SyncML
MMS
Gateway
View port
Synchronization is through the following binding over the WAP application
client or server
SyncML
MMS
Gateway
View port
The following architecture doesn t provide HTTP-TLS-TCP-IP layers at the
client for interacting with the WAP gateway
WAP 0.2
WAP 1.1
WAP 2.0
WAP 5.0
TLS is
Service protocol
Security protocol
www.studentshangout.com
www.studentshangout.com
c.Data link layer protocol
d.Physical layer protocol
195.WSP layer in WAP 2.0 acts as the following protocol when connecting to
internet on the wireless network
a.
b.
c.
d.
196.
a.
b.
c.
d.
197.
a.
b.
c.
d.
198.
a.
b.
c.
d.
199.
Service protocol
Security protocol
Data link layer protocol
Application layer
HTTP stands for
Hypertext transfer protocol
head tail transfer protocol
Hyper text transport protocol
Head tail transport protocol
WAP 2.0 is
Internet protocol
Wireless protocol
TCP/IP protocol
MESI protocol
The following connects WAP client to HTTP servers
WAP gate way
MMS
SyncML synchronization
Linker
The following serves the websites on the internet
a.Database server
b.Web server
c.Application server
d.Java server
200.HTTP layer in TCP/IP protocol suite acts as the following protocol when
connecting to internet in wired internet
a.
b.
c.
d.
Physical layer
Application layer
Data link layer
Transport layer
www.studentshangout.com
www.studentshangout.com
www.uandiMp3.blogspot.com
for all types of Music
You might also like
- JNTU Online Examinations MC QuestionsDocument18 pagesJNTU Online Examinations MC QuestionsvemurirajaNo ratings yet
- L IV 2013 ExamDocument12 pagesL IV 2013 ExamAbebe Gosu100% (4)
- A. Dispatcher: One Three FourDocument6 pagesA. Dispatcher: One Three FourmeymunaNo ratings yet
- B. Coaxial CableDocument6 pagesB. Coaxial Cablemeymuna100% (1)
- 4th Quarterly Test Grade 9 AnsweredDocument2 pages4th Quarterly Test Grade 9 AnsweredHei Dee60% (5)
- Iot MCQDocument18 pagesIot MCQShweta kumbharNo ratings yet
- Iot MCQDocument10 pagesIot MCQRui ManjrekarNo ratings yet
- MCQDocument5 pagesMCQsubhasisdattaNo ratings yet
- KRISHNENDU GUIN - Assignment 2Document20 pagesKRISHNENDU GUIN - Assignment 2Krishnendu GuinNo ratings yet
- HNS L3 Coc Exam 2013 With Answer Part1Document8 pagesHNS L3 Coc Exam 2013 With Answer Part1Destu Happy DestaNo ratings yet
- Answer 2Document5 pagesAnswer 2Yohannes bekeleNo ratings yet
- Coc 33Document5 pagesCoc 33wesen destaNo ratings yet
- Computer Fundamentals MCQDocument8 pagesComputer Fundamentals MCQangelo_lopez1993No ratings yet
- Distributed Systems Fundamentals QuizDocument55 pagesDistributed Systems Fundamentals QuizAmit PatilNo ratings yet
- Aca Mid-1 Obj With AnsDocument9 pagesAca Mid-1 Obj With AnsHanisha BavanaNo ratings yet
- Computer literacy vital for successDocument22 pagesComputer literacy vital for successRiza ArceñoNo ratings yet
- Multiple Choice QuestionsDocument6 pagesMultiple Choice QuestionsSravanthi Gelley0% (1)
- Computer Networks MCQ Bank and Free Study Material PDFDocument220 pagesComputer Networks MCQ Bank and Free Study Material PDFVikasSainiNo ratings yet
- New Level 4 Doc 2Document10 pagesNew Level 4 Doc 2Gebrehana Alemaw100% (4)
- Coc Best Level 4-1-1Document21 pagesCoc Best Level 4-1-1sflayNo ratings yet
- Computer NetworksDocument24 pagesComputer NetworksAnsar iqbalNo ratings yet
- IT QuizDocument16 pagesIT QuizVishal KanojiyaNo ratings yet
- Distributed System MCQ 2018Document25 pagesDistributed System MCQ 2018Padma Pradhan60% (73)
- CLOUD COMPUTING REVIEWDocument17 pagesCLOUD COMPUTING REVIEWMeena DhangarNo ratings yet
- Computer Networks MCQsDocument42 pagesComputer Networks MCQsWaqas Javed50% (4)
- Os Ca MCQ'SDocument5 pagesOs Ca MCQ'Ssk khuddusNo ratings yet
- MIS MCQ'sDocument14 pagesMIS MCQ'sumaimaNo ratings yet
- C. Wireless LANDocument16 pagesC. Wireless LANEnyew100% (2)
- OS Objective TypeDocument16 pagesOS Objective TypesoniamimitNo ratings yet
- Multiple Choice Questions (MCQ) of Computer Communication NetworkDocument3 pagesMultiple Choice Questions (MCQ) of Computer Communication NetworkhariprasadnrNo ratings yet
- MCQs For SComputerDocument15 pagesMCQs For SComputerzawiyartariqNo ratings yet
- computer-networks [set 1]Document21 pagescomputer-networks [set 1]ali abbasNo ratings yet
- CA. 7.1 Cloud Computing (17-18)Document16 pagesCA. 7.1 Cloud Computing (17-18)Kaushal KapureNo ratings yet
- ICT1 SA3 Revision QuestionsDocument28 pagesICT1 SA3 Revision Questionsdog dog100% (1)
- Hardware and Network Servicing Level III Knowledge TestDocument8 pagesHardware and Network Servicing Level III Knowledge TestAlem Girma100% (1)
- CSEC Multiple Choice 1Document10 pagesCSEC Multiple Choice 1Brian PowellNo ratings yet
- MUF0051 ICT Unit 1 Revision Questions and SolutionsDocument25 pagesMUF0051 ICT Unit 1 Revision Questions and Solutionsdog dogNo ratings yet
- DC Mcqs: Distributed Computing Multiple Choice QuestionsDocument10 pagesDC Mcqs: Distributed Computing Multiple Choice QuestionsncgNo ratings yet
- Computer Applications in ManagementDocument29 pagesComputer Applications in ManagementDarshitNo ratings yet
- Electronics Sample Problems 05Document6 pagesElectronics Sample Problems 05Genesis PinedaNo ratings yet
- 2nd Sem FINAL EXAMDocument4 pages2nd Sem FINAL EXAMMark Joseph BernalNo ratings yet
- HNS Level 4 Basic COC QueationDocument17 pagesHNS Level 4 Basic COC QueationMohammed Jemal90% (10)
- Level 4 2013.doc..bakDocument12 pagesLevel 4 2013.doc..bakkurib38No ratings yet
- 391 - Information Technology Concepts (Open) - R - 2018Document12 pages391 - Information Technology Concepts (Open) - R - 2018avfg gfavdNo ratings yet
- All Networking MultichoiceDocument160 pagesAll Networking MultichoicesauravnarukaNo ratings yet
- Mis 8th Edition Bidgoli Test BankDocument18 pagesMis 8th Edition Bidgoli Test Bankgestantasbesti.nevd100% (26)
- Mis 8Th Edition Bidgoli Test Bank Full Chapter PDFDocument39 pagesMis 8Th Edition Bidgoli Test Bank Full Chapter PDFJamesScottnbgp100% (7)
- QUESTIONDocument31 pagesQUESTIONTazkia EshanaNo ratings yet
- CA&ODocument12 pagesCA&OMohammad AhmedNo ratings yet
- 2nd Periodic Test CSS 12Document3 pages2nd Periodic Test CSS 12Kathrine Jane LunaNo ratings yet
- CompTIA A+ Certification All-in-One Exam Questions Prep (220-701 & 220-702)From EverandCompTIA A+ Certification All-in-One Exam Questions Prep (220-701 & 220-702)Rating: 2.5 out of 5 stars2.5/5 (6)
- CCNA Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesFrom EverandCCNA Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesNo ratings yet
- Programming Massively Parallel Processors: A Hands-on ApproachFrom EverandProgramming Massively Parallel Processors: A Hands-on ApproachNo ratings yet
- Chapters 8 OscillatorDocument134 pagesChapters 8 OscillatorTspi RitzelNo ratings yet
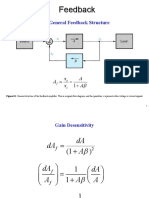
- FeedbackDocument68 pagesFeedbackchibssa alemayehuNo ratings yet
- From Unimap, Malaysia Louisiana State U HK City U Eastern Washington UDocument59 pagesFrom Unimap, Malaysia Louisiana State U HK City U Eastern Washington USai SadiqNo ratings yet
- 1.circuits and Simulation Integrated LaboratoryDocument46 pages1.circuits and Simulation Integrated LaboratoryYokesvaran KNo ratings yet
- 1.circuits and Simulation Integrated LaboratoryDocument46 pages1.circuits and Simulation Integrated LaboratoryYokesvaran KNo ratings yet
- EE100B p05Document12 pagesEE100B p05Sai SadiqNo ratings yet
- Electronic Circuits LatestDocument69 pagesElectronic Circuits LatestSai SadiqNo ratings yet
- Ac Unit IDocument36 pagesAc Unit ISai SadiqNo ratings yet
- Rectification of TransformerDocument11 pagesRectification of TransformerLuís Ki-llahNo ratings yet
- Introduction To FET's: ELEC 121 Author UnknownDocument36 pagesIntroduction To FET's: ELEC 121 Author UnknownNaseeb AghaNo ratings yet
- FourierDocument9 pagesFourierSai SadiqNo ratings yet
- Pspice Simulation of Single-Phase Full Converter With Rle Load and Single-Phase Ac Voltage Controller Using Rle LoadsDocument3 pagesPspice Simulation of Single-Phase Full Converter With Rle Load and Single-Phase Ac Voltage Controller Using Rle LoadsSai Sadiq100% (1)
- Techno CrosswordDocument1 pageTechno CrosswordSai SadiqNo ratings yet
- AC 4unit PDFDocument18 pagesAC 4unit PDFSai SadiqNo ratings yet
- TRANSISTOR - Introduction: Bipolar Junction Transistor (BJT)Document23 pagesTRANSISTOR - Introduction: Bipolar Junction Transistor (BJT)Hemant SinghNo ratings yet
- Lecture 11Document27 pagesLecture 11Sai SadiqNo ratings yet
- Multistage AmplifierDocument18 pagesMultistage AmplifierSai SadiqNo ratings yet
- Lecture 11Document27 pagesLecture 11Sai SadiqNo ratings yet
- B-Stad CH 05Document46 pagesB-Stad CH 05Sai SadiqNo ratings yet
- Special Types of DiodesDocument19 pagesSpecial Types of DiodesKirstine CamachoNo ratings yet
- DiodeDocument16 pagesDiodeSai SadiqNo ratings yet
- 320 Lecture 22Document12 pages320 Lecture 22Sai SadiqNo ratings yet
- 91567-00 TransistorFeedbackCircuits SW ED4 PR2 WebDocument46 pages91567-00 TransistorFeedbackCircuits SW ED4 PR2 WebSai Sadiq50% (2)
- JJ Oc Unit IiiDocument11 pagesJJ Oc Unit IiiSai SadiqNo ratings yet
- Introduction to High Frequency Hybrid Pi Model BJTDocument2 pagesIntroduction to High Frequency Hybrid Pi Model BJTSai Sadiq100% (1)
- Electronic Circuits IDocument36 pagesElectronic Circuits ISai SadiqNo ratings yet
- 91567-00 TransistorFeedbackCircuits SW ED4 PR2 WebDocument46 pages91567-00 TransistorFeedbackCircuits SW ED4 PR2 WebSai Sadiq50% (2)
- CPLD FpgaDocument21 pagesCPLD FpgaAaqib IhrazNo ratings yet
- 320 Lecture 22Document12 pages320 Lecture 22Sai SadiqNo ratings yet
- PCS-9641 X Instruction Manual en Customized ECKF162195 R101Document244 pagesPCS-9641 X Instruction Manual en Customized ECKF162195 R101Bayu Dwi AsmaraNo ratings yet
- Tenaris Case Study en 0618 PDFDocument4 pagesTenaris Case Study en 0618 PDFAmmarGhazaliNo ratings yet
- Guimn - E-Surpass Hit 7070 3.2Document666 pagesGuimn - E-Surpass Hit 7070 3.2Anonymous Cx5zpf8100% (3)
- Quick Operation Manual HX-CCD20Document11 pagesQuick Operation Manual HX-CCD20Mafosk8No ratings yet
- 70 341 PDFDocument38 pages70 341 PDFsmart EntryNo ratings yet
- Administering Avaya Aura® Communication ManagerDocument894 pagesAdministering Avaya Aura® Communication ManagernaptunNo ratings yet
- USB AttackDocument26 pagesUSB AttackRahib RahmanNo ratings yet
- Qdoc - Tips PHP and Mysql Project On Car Rental System ProjectDocument65 pagesQdoc - Tips PHP and Mysql Project On Car Rental System Project1dt19cs056 Hemanth100% (1)
- ETE423 EEE423 - Lecture 6 - Multipleaxing SONETDocument54 pagesETE423 EEE423 - Lecture 6 - Multipleaxing SONETShadman Rahman 1815396660No ratings yet
- Call Letter 1Document9 pagesCall Letter 1sharma_anshu_b_techNo ratings yet
- Earth and ScienceDocument8 pagesEarth and ScienceAj LarayaNo ratings yet
- Assignment 1 Tutorial - Various Types of DevicesDocument2 pagesAssignment 1 Tutorial - Various Types of DevicesPulkit GuptaNo ratings yet
- ppt-3 Fundnamental Technologies and ServicesDocument99 pagesppt-3 Fundnamental Technologies and ServicesshaliniNo ratings yet
- MPLS Applications Configuration GuideDocument68 pagesMPLS Applications Configuration GuideElis1234567100% (1)
- Wodaplug Cortina EPON OLT - New WEB Configuration GuideDocument35 pagesWodaplug Cortina EPON OLT - New WEB Configuration GuideSergio Denis UCNo ratings yet
- PUB00123R0 Common Industrial Protocol and Family of CIP NetwDocument92 pagesPUB00123R0 Common Industrial Protocol and Family of CIP NetwPaBenavidesNo ratings yet
- PRACTICE TEST - AZURE Fundamentals (AZ-900) - PASS in FIRST AttemptDocument314 pagesPRACTICE TEST - AZURE Fundamentals (AZ-900) - PASS in FIRST AttemptMarco Encina G.50% (2)
- University of Science and Technology of Southern Philippines SyllabusDocument8 pagesUniversity of Science and Technology of Southern Philippines SyllabusChristine MadridNo ratings yet
- Wind River License Administrator Tools Guide 1.1Document134 pagesWind River License Administrator Tools Guide 1.1patopickNo ratings yet
- 19813rana Adeel Cover Letter & CVDocument10 pages19813rana Adeel Cover Letter & CVabdul waleedNo ratings yet
- Introduction To Information Storage and Management: © 2009 EMC Corporation. All Rights ReservedDocument21 pagesIntroduction To Information Storage and Management: © 2009 EMC Corporation. All Rights ReservedDeebika KaliyaperumalNo ratings yet
- Layers of The Osi Model Illustrated 818017Document18 pagesLayers of The Osi Model Illustrated 818017Sridhar PNo ratings yet
- How To Use Splunk For Automated Regulatory Compliance PDFDocument74 pagesHow To Use Splunk For Automated Regulatory Compliance PDFDennis DubeNo ratings yet
- AZ-104T00 Microsoft Azure Administrator: Course DescriptionDocument19 pagesAZ-104T00 Microsoft Azure Administrator: Course DescriptionsargaNo ratings yet
- Iph206-Iph206l User GuideDocument16 pagesIph206-Iph206l User Guideerkan. çelikNo ratings yet
- Rajiv Gandhi College Information Security SyllabusDocument3 pagesRajiv Gandhi College Information Security SyllabusShantha Jayakumar100% (1)
- Virtual Private NetworkDocument10 pagesVirtual Private NetworkHrishikesh JagdhaneNo ratings yet
- LANs and Network TopologiesDocument4 pagesLANs and Network TopologiesBowWowMXNo ratings yet
- Control Engineering MagazineDocument84 pagesControl Engineering MagazineAnonymous Uqrw8OwFWu100% (2)































![computer-networks [set 1]](https://imgv2-2-f.scribdassets.com/img/document/721359975/149x198/d7eeef8fbb/1712635462?v=1)