Professional Documents
Culture Documents
Josh Moulin - What Information Is in Your Digital Images?
Uploaded by
Josh MoulinOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Josh Moulin - What Information Is in Your Digital Images?
Uploaded by
Josh MoulinCopyright:
Available Formats
!"#$ &'()*+#$&)' &, &' -).* /&0&$#1 !"#$%&!
ulglLal plcLures and vldeo have Lransformed our llves. l have so many plcLures and vldeos of my
klds LhaL by Lhe Llme Lhey are ln college, l'll have 1erabyLes of daLa. lL ls so easy Lhese days Lo
capLure anyLhlng wlLh a dlglLal lmage. 1here ls no need Lo worry abouL havlng fllm developed,
or belng careful Lo only Lake good plcLures slnce you only have a llmlLed amounL of plcLures lefL
on Lhe roll ln your camera. now, we're only llmlLed by Lhe amounL of sLorage space our dlglLal
devlces have. As an example, Lhe MlcroSu card ln mosL of our smarLphones can conLaln over
18,000 plcLures.
MlcroSu cards now have a capaclLy of up Lo 64 C8
CfLen, dlglLal lmages are lnvolved ln crlmlnal lnvesLlgaLlons. lmaglne Lhe Lreasure-Lrove of
lnformaLlon LhaL can be obLalned from a cell phone, LableL, or dlglLal camera when lL ls selzed
from a suspecL. ln my experlence, Lhose lnvolved ln crlmlnal acLlvlLy [usL can'L help Lhemselves
when lL comes Lo documenLlng Lhelr crlmlnal acLlvlLy ln plcLures or vldeo. ln llLerally hundreds
of cases, l found suspecLs Laklng plcLures of Lhemselves uslng drugs, vandallzlng properLy,
commlLLlng arson, abuslng chlldren, and ln some cases, even murder.
Whlle havlng plcLure or vldeo evldence of a suspecL acLually commlLLlng a crlme ls Lhe Lype of
evldence LhaL makes a prosecuLor exclLed abouL a case, Lhe dlglLal lmage ls [usL Lhe beglnnlng of
Lhe sLory. lmaglne lf we could Lell whaL camera was used Lo Lake a cerLaln plcLure LhaL was
found on Lhe lnLerneL, or could llnk an lmage found on a suspecL's compuLer wlLh Lhelr personal
phone or dlglLal camera found aL Lhelr home? 1hls ls all posslble Lhanks Lo someLhlng called
meLadaLa.
MeLadaLa ls slmply exLra lnformaLlon abouL a flle, or some people refer Lo lL as daLa abouL
daLa". ?ou are probably famlllar wlLh meLadaLa buL maybe noL wlLh Lhe Lerm lLself. Pave you
ever rlghL-cllcked on a compuLer flle and seen Lhe properLles? uaLes, Llmes, who was Lhe
auLhor, when Lhe flle was lasL prlnLed, eLc., are all examples of meLadaLa. lor dlglLal plcLures
and vldeos Lhere ls a speclflc klnd of meLadaLa LhaL exlsLs known as Lxll (Lxchangeable lmage
llle lormaL) daLa. Lxll daLa ls lnformaLlon embedded ln Lhe lmage or vldeo LhaL can conLaln all
or some of Lhe lnformaLlon below (whaL ls acLually ln Lhe lmage depends on Lhe camera
manufacLurer):
Make of Lhe camera LhaL Look Lhe plcLure/vldeo
Model of Lhe camera
Serlal number of Lhe camera
uaLe / Llme Lhe lmage was Laken (accordlng Lo Lhe camera's clock)
lllename
llash seLLlngs
AperLure seLLlngs
lmage resoluLlon
SofLware
And more.
A forenslc compuLer examlner can examlne a plcLure or vldeo for evldence of Lxll daLa and use
speclal programs Lo lnLerpreL Lhe lnformaLlon. 1here are many free programs avallable on Lhe
lnLerneL Lo do Lhls and many phoLographers use Lxll daLa Lo lmprove Lhelr phoLographs. ln
facL, Lxll daLa was orlglnally creaLed for phoLographers so Lhey could look aL Lhelr camera
seLLlngs sLored wlLhln Lhe Lxll daLa Lo flnd ouL whaL seLLlngs worked or dldn'L work when
Laklng plcLures under dlfferenL condlLlons.
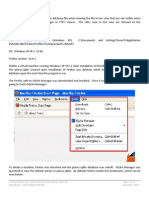
ScreenshoL from an Lxll daLa parslng Lool
1o lllusLraLe how Lxll daLa can be used Lo solve a crlme, lmaglne Lhls scenarlo. l was
lnvesLlgaLlng a case where an adulL male was suspecLed of havlng a sexually expllclL
conversaLlon wlLh a 14-year-old female vla Lhe lnLerneL. 1hls adulL male was sendlng expllclL
LexL messages and lL gradually escalaLed Lo hlm sendlng lmages of.well, you can lmage, Lo Lhe
vlcLlm. When Lhe vlcLlm reporLed Lhls Lo a Leacher aL school, our unlL became lnvolved and we
forenslcally analyzed Lhe vlcLlm's cell phone.
When revlewlng Lhe plcLures on Lhe vlcLlm's phone, we found Lhe plcLures of Lhe suspecL.
none of Lhe lmages showed hls face and all of Lhem were obvlously Laken from lnslde of a
resldence. Slnce he senL Lhe messages from hls cell phone, we were able Lo Lrace Lhe phone
number Lhey came from and ldenLlfy Lhe sender. When we revlewed Lhe plcLures senL from Lhe
suspecL, each lmage conLalned Lxll daLa. 1he Lxll daLa showed LhaL Lhe plcLures were all
Laken from a Samsung cellular phone and slnce he had hls geoLagglng feaLure enabled on Lhls
phone, each lmage conLalned Lhe laLlLude and longlLude of exacLly where Lhe phone was when
Lhe lmage was Laken. 1hls allowed me Lo creaLe a Coogle LarLh map, whlch happened Lo place
a blg red doL rlghL over Lhe suspecL's aparLmenL.
!usL from Lhe Lxll lnformaLlon we could prove LhaL Lhe parLlcular sexually expllclL lmage was
Laken by Lhe suspecL's phone, from Lhe suspecL's home, aL a cerLaln daLe/Llme (slnce phone's
clocks are generally seL by Lhe cell phone neLwork, Lhey are rellable). AnoLher crlLlcal elemenL
Lo prove ln a crlme ls LhaL of venue (provlng Lhe crlme happened wlLhln a cerLaln [urlsdlcLlon).
WlLh Lxll daLa, lL ls noL dlfflculL Lo prove Lhls aL all, slnce we know Lhe exacL CS coordlnaLes of
Lhe crlme scene.
Lxll daLa has also been used Lo locaLe vlcLlms or suspecLs of crlmes from lmages and vldeos
posLed on Lhe lnLerneL. lmaglne waLchlng a vldeo LhaL was uploaded Lo Lhe lnLerneL whlch
deplcLed Lhe raclally moLlvaLed assaulL of a person. lf Lhe camera used Lo creaLe Lhe vldeo ls
capable of embeddlng Lxll daLa and Lhe webslLe Lhe vldeo was uploaded Lo doesn'L remove
Lxll daLa, lnvesLlgaLors can download Lhe vldeo and examlne Lhe Lxll daLa Lo poLenLlally flnd
ouL more lnformaLlon Lo lead Lo a suspecL.
Whlle Lxll daLa has proven lLself Lo be an amazlng Lool for law enforcemenL, lL has also been
explolLed by crlmlnals. lf you have used any of Lhe geoLagglng feaLures of your favorlLe soclal
medla slLes (1wlLLer, Coogle+, ?ou1ube, lacebook, loursquare, eLc.) Lhen you are aware LhaL
you can share your locaLlon wlLh your posLs and plcLures. 1hls Lechnology ls slmllar Lo Lxll daLa
by uLlllzlng Lhe devlces lnLernal CS funcLlonallLy Lo embed your longlLude and laLlLude lnLo
your posL.
Crlmlnals have begun uslng Lhls Lechnology as anoLher Lool for cybersLalklng. 8y downloadlng
lmages and vldeos LhaL people posL Lo Lhelr personal webslLes or soclal medla slLes, Lech-savvy
crlmlnals can do Lhe same Lechnlque law enforcemenL employs Lo locaLe where someone was
aL when Lhey creaLed Lhe lmage. lf you are a vlcLlm of sLalklng or have been LhreaLened by
someone ln Lhe pasL and have gone Lo greaL lengLhs Lo hlde from Lhem, all lL would Lake ls Lhem
geLLlng ahold of one lmage placed on a soclal neLwork slLe Laken by your cell phone or hlgh-end
dlglLal camera wlLh bullL-ln CS. lf LhaL plcLure was Laken aL your home, work, chlld's school,
eLc. LhaL's all Lhey would need Lo flnd you. lL's a scary LhoughL and one LhaL people musL
conslder when uslng Lhls klnd of Lechnology LhaL ls generally Lurned on by defaulL.
!osh Moulln
!osh has a long hlsLory of publlc servlce, beglnnlng ln 1993 as a llreflghLer and LM1. AfLer elghL years of varlous
asslgnmenLs, !osh lefL Lhe flre servlce wlLh Lhe rank of LleuLenanL when he was hlred as a pollce offlcer.
!osh spenL Lhe nexL eleven years ln law enforcemenL worklng varlous asslgnmenLs. !osh worked as a paLrol offlcer,
fleld Lralnlng offlcer, arson lnvesLlgaLor, deLecLlve, forenslc compuLer examlner, sergeanL, lleuLenanL, and Lask
force commander.
1he lasL seven years of !osh's law enforcemenL career was spenL as Lhe commander of a reglonal, mulLl-
[urlsdlcLlonal, federal cyber crlme Lask force. !osh oversaw cyber crlme lnvesLlgaLlons and dlglLal forenslc
examlnaLlons for over 30 local, sLaLe, and federal law enforcemenL agencles. under !osh's leadershlp, Lhe forenslcs
lab was accredlLed by Lhe Amerlcan SocleLy of Crlme Lab ulrecLors / LaboraLory AccredlLaLlon 8oard (ASCLu/LA8)
ln 2009.
!osh has been recognlzed as a naLlonal experL ln Lhe fleld of dlglLal evldence and cyber crlme and frequenLly speaks
across Lhe naLlon on varlous Loplcs. Pe has LesLlfled as an experL wlLness ln dlglLal forenslcs and cyber crlme ln
boLh sLaLe and federal courL on several occaslons. Pe also holds a varleLy of dlglLal forenslc and law enforcemenL
cerLlflcaLlons, has an assoclaLe's degree and graduaLed summa cum laude wlLh hls bachelor's degree.
ln 2012 !osh lefL law enforcemenL Lo pursue a fullLlme career ln cyber securlLy, lncldenL response, and forenslcs
supporLlng a federal agency. !osh now leads Lhe MonlLor and ConLrol 1eam of a Cyber SecurlLy Cfflce and hls Leam
ls responslble for dally cyber securlLy operaLlons such as, lncldenL response, dlglLal forenslcs, neLwork monlLorlng,
log revlew, neLwork perlmeLer proLecLlon, and flrewall managemenL.
You might also like
- Disheveled Digital Forensics: The Impact of Inconsistent Standards, Certifications, and AccreditationDocument84 pagesDisheveled Digital Forensics: The Impact of Inconsistent Standards, Certifications, and AccreditationJosh MoulinNo ratings yet
- Information Security Basics For Businesses and IndividualsDocument17 pagesInformation Security Basics For Businesses and IndividualsJosh MoulinNo ratings yet
- Josh Moulin - Interviewed by GCN About Mobile ForensicsDocument4 pagesJosh Moulin - Interviewed by GCN About Mobile ForensicsJosh MoulinNo ratings yet
- Josh Moulin - How Your Computer Can Be A Threat To National SecurityDocument3 pagesJosh Moulin - How Your Computer Can Be A Threat To National SecurityJosh MoulinNo ratings yet
- Josh Moulin - Designing A Mobile Digital Forensic Lab On A BudgetDocument18 pagesJosh Moulin - Designing A Mobile Digital Forensic Lab On A BudgetJosh MoulinNo ratings yet
- Josh Moulin - Covert Entry TacticsDocument5 pagesJosh Moulin - Covert Entry TacticsJosh MoulinNo ratings yet
- Josh Moulin - Striking at The Heart of Internet VictimizationDocument3 pagesJosh Moulin - Striking at The Heart of Internet VictimizationJosh MoulinNo ratings yet
- Josh Mouiln - 2007 HOUSE JUDICIARY TestimonyDocument4 pagesJosh Mouiln - 2007 HOUSE JUDICIARY TestimonyJosh MoulinNo ratings yet
- Josh Moulin - Mozilla Firefox Deleted URLs in Places - SqliteDocument19 pagesJosh Moulin - Mozilla Firefox Deleted URLs in Places - SqliteJosh MoulinNo ratings yet
- Josh Moulin - Multidisciplinary Team Protocol For Child ExploitationDocument4 pagesJosh Moulin - Multidisciplinary Team Protocol For Child ExploitationJosh MoulinNo ratings yet
- Josh Moulin - What Every Prosecutor Should Know About Peer-To-Peer InvestigationsDocument2 pagesJosh Moulin - What Every Prosecutor Should Know About Peer-To-Peer InvestigationsJosh MoulinNo ratings yet
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (537)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5794)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (890)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (399)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (838)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (344)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (587)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (73)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (265)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1090)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2219)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (119)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (821)
- Uil Lincoln-Douglas Debate Research SeriesDocument45 pagesUil Lincoln-Douglas Debate Research SeriesAryan JasaniNo ratings yet
- U14 InclassDocument24 pagesU14 InclassImron MashuriNo ratings yet
- Vertical Crater Retreat Mining in The Sudbury Basin: Mining Science and TechnologyDocument13 pagesVertical Crater Retreat Mining in The Sudbury Basin: Mining Science and TechnologyStajic MilanNo ratings yet
- Digital Innovation and Transformation - An Institutional PerspectiveDocument10 pagesDigital Innovation and Transformation - An Institutional PerspectiveGabriele12No ratings yet
- Haivision Calypso Administration Guide v2.1Document142 pagesHaivision Calypso Administration Guide v2.1The Narcotic Dragon CafeNo ratings yet
- Microsoft Teams User Manual GuideDocument6 pagesMicrosoft Teams User Manual GuideArun HarpalaniNo ratings yet
- Dematic WMSDocument20 pagesDematic WMSkrystyinNo ratings yet
- Vidyashree B K: Career ObjectiveDocument2 pagesVidyashree B K: Career ObjectiveVidya K GowdaNo ratings yet
- ML-ProblemStatement Youtube Adview Prediction-1 Lyst8087Document2 pagesML-ProblemStatement Youtube Adview Prediction-1 Lyst8087Gattem Raghu RamNo ratings yet
- Cmu-4000 Og 5230790130Document74 pagesCmu-4000 Og 5230790130roshan mungurNo ratings yet
- RPL Engg Drawing NSQF-6Document9 pagesRPL Engg Drawing NSQF-6Safvan KhansahebNo ratings yet
- Cantor's Diagonal ArgumentDocument5 pagesCantor's Diagonal ArgumentLe Nguyen Thang LongNo ratings yet
- Pinsex Response BriefDocument22 pagesPinsex Response BriefMarcJohnRandazzaNo ratings yet
- Information Management - Module - Unit IIDocument20 pagesInformation Management - Module - Unit IICARISIOSA NOELLA MAYNo ratings yet
- Philips Azurion Bi Plane Specifications 7b20 12Document28 pagesPhilips Azurion Bi Plane Specifications 7b20 12service iyadMedicalNo ratings yet
- NN Bhargava Basic Electronics and Linear Circuits PDFDocument169 pagesNN Bhargava Basic Electronics and Linear Circuits PDFJovin Pallickal Thomas50% (2)
- ZAAA x32 Ironman SK (ZAA) & Captain SK (ZAAA) MB 6L E Version PDFDocument48 pagesZAAA x32 Ironman SK (ZAA) & Captain SK (ZAAA) MB 6L E Version PDFSebastian StanacheNo ratings yet
- Michael Nasol (April)Document10 pagesMichael Nasol (April)Anonymous CuIeVjHNo ratings yet
- IEC and ISO Standards: How To Best UseDocument12 pagesIEC and ISO Standards: How To Best UseNamiJen LobatoNo ratings yet
- MagicQ Remote App SetupDocument4 pagesMagicQ Remote App Setupderte linoNo ratings yet
- Digit Magazine (India) (May 2007)Document103 pagesDigit Magazine (India) (May 2007)duttasabyNo ratings yet
- Medical Report PDFDocument2 pagesMedical Report PDFVijjasena SugionoNo ratings yet
- CGR (22318) Chapter 1 NotesDocument10 pagesCGR (22318) Chapter 1 Notespdijgqam1nNo ratings yet
- Bbcode TS3 PDFDocument1 pageBbcode TS3 PDFRoberto MicroNo ratings yet
- A Study On Brand Awareness of Radhas Ayurvedic Soap ForRadhas Ayurvedic Soap WorksDocument2 pagesA Study On Brand Awareness of Radhas Ayurvedic Soap ForRadhas Ayurvedic Soap WorksnimishaNo ratings yet
- An Overview of The Electrical Validation of 10BASE-T 100BASE-TX and 1000BASE-T DevicesDocument14 pagesAn Overview of The Electrical Validation of 10BASE-T 100BASE-TX and 1000BASE-T DevicescolinyNo ratings yet
- Manual Técnico Micros ES Raa033benDocument264 pagesManual Técnico Micros ES Raa033benrafael amancioNo ratings yet
- Torrent Downloads - Download Free Torrents!Document1 pageTorrent Downloads - Download Free Torrents!André Brandão50% (2)
- Artificial Intelligent Application To Power System ProtectionDocument7 pagesArtificial Intelligent Application To Power System Protectionjijo123408No ratings yet
- AGLiS DMS For TNS - Customer Upload Template - TXTDocument2 pagesAGLiS DMS For TNS - Customer Upload Template - TXTfajar wahyudiNo ratings yet