Professional Documents
Culture Documents
ISA Server 2004 - Configurar Una VPN
Uploaded by
Juan CarlosOriginal Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
ISA Server 2004 - Configurar Una VPN
Uploaded by
Juan CarlosCopyright:
Available Formats
Enable the VPN Server
By default, the VPN server component is disabled. The first step is to enable the VPN
server feature and configure the VPN server components.
Perform the following steps to enable and configure the IS Server !""# VPN Server$
%. &pen the Microsoft Internet Security and Acceleration Server 2004
management console and e'pand the server name. (lic) on the Virtual Private
Networks VPN! node.
!. (lic) on the "asks tab in the Tas) Pane. (lic) the Enable VPN #lient Access
lin).
3. Click Apply to save the changes and update the firewall policy.
4. Click OK in the Apply New Configuration dialog box.
5. Click the Configure VPN Client Access link.
6. On the General tab, change the value for the Maximum number of VPN clients
allowed fro 5 to !.
!. Click on the Groups tab. On the Groups tab, click the Add button.
". #n the "elect Groups dialog box, click the #ocations button. #n the #ocations dialog
box, click the msfirewall$org entry and click OK.
$. #n the "elect Group dialog box, enter %omain &sers in the 'nter t(e ob)ect names to
select text box. Click the C(ec* Names button. %he group nae will be underlined when
it is found in the &ctive 'irectory. %his value is used in the reote access policy anaged
by the #(& (erver )**4 firewall achine. +hen the user accounts are configured to use
reote access policy for dial,in access, then #(& (erver )**4 reote access policy will be
applied to the -./ client connections. Click OK.
10.Click the Protocols tab. On the Protocols tab, put a checkark in the 'nable
#+,P-.P"ec checkbox. /ote that you will have to issue a achine certificate to the #(&
(erver )**4 firewall0-./ server, and to the connecting -./ clients, before you can use
1)%.0#.(ec. &n alternative is to use a pre,shared key for the #.(ec security negotiations.
11.Click the &ser Mapping tab. .ut a checkark in the 'nable &ser Mapping checkbox.
.ut a checkark in the /(en username does not contain a domain0 use t(is
domain checkbox. 2nter msfirewall$org in the %omain Name text box. /ote that these
settings will only apply when using 3&'#4( authentication. %hese settings are ignored
when using +indows authentication 5such as when the #(& (erver )**4 firewall achine
belongs to the doain and the user explicitly enters doain credentials6. Click Apply and
then click OK$ 7ou ay see a Microsoft .nternet "ecurity and Acceleration "er1er
+!!2 dialog box inforing you that you need to restart the coputer for the settings to
take effect. #f so, click OK in the dialog box.
12.On the ,as*s tab, click the "elect Access Networ*s link.
83. #n the Virtual Pri1ate Networ*s 3VPN4 Properties dialog box, click the Access
Networ*s tab. /ote that the 'xternal checkbox is selected. %his indicates that the
external interface is listening for incoing -./ client connections. 7ou could choose other
interfaces, such as '9: or extranet interfaces, if you wish to provide dedicated -./
services to trusted hosts and networks. #;ll go over this type of configuration, as well as
how to configure additional interfaces for +1&/ access, in future articles here on the
www.isaserver.org +eb site and in our #(& (erver )**4 book.
84. Click the Address Assignment tab. (elect the internal interface fro the list in the &se
t(e following networ* to obtain %5CP0 %N" and /.N" ser1ices list box. %his is a
critical setting, as it defines the network on which access to the '<C. is ade. /ote that
in this exaple we are using a '<C. server on the internal network to assign addresses
to -./ clients. %he '<C. server will not assign '<C. options to the -./ clients unless
you install the '<C. 3elay &gent on the #(& (erver )**4 firewall0-./ server achine.
7ou have the option to create a static address pool of addresses to be assigned to the -./
clients. #f you choose to use a static address pool, you will not be able to assign '<C.
options to these hosts. &lso, if you choose to use a static address pool, you should use an
off,subnet network #'. .lease refer to (tefaan .ouseele;s article on off,subnet address
configuration over at
http=00isaserver.org0articles0<ow>to>#pleent>-./>Off(ubnet>#.>&ddresses.htl.
15.Click on the Aut(entication tab. /ote that the default setting is to enable only Microsoft
encrypted aut(entication 1ersion + 3M"6C5AP1+4. #n later docuents in this ."A
"er1er +!!2 VPN %eployment Kit we will enable the 2&. option so that high security
user certificates can be used to authenticate with the #(& (erver )**4 firewall -./ server.
/ote the Allow custom .P"ec policy for #+,P connection checkbox. #f you do not
want to create a public key infrastructure or in the process of creating one but have not
yet finished, then you can enable this checkbox and then enter a pre6s(ared key. %he
-./ clients will need to be configured to use the sae pre,shared key.
16.Click the 7A%.&" tab. <ere you can configure the #(& (erver )**4 firewall -./ server to
use 3&'#4( to authenticate the -./ users. %he advantage of 3&'#4( authentication is
that you can leverage the &ctive 'irectory 5and others6 user database to authenticate
users without needing to ?oin the &ctive 'irectory doain. +e;ll go over the deep details
of 3&'#4( configuration to support -./ connections in later docuents on the
www.isaserver.org +eb site and in our #(& (erver )**4 book.
8!. Click Apply in the Virtual Pri1ate Networ*s 3VPN4 Properties dialog box and then
click OK.
8". Click Apply to save the changes and update the firewall policy.
8$. Click OK in the Apply New Configuration dialog box.
)*. 3estart the #(& (erver )**4 firewall achine.
%he achine will obtain a block of #. addresses fro the '<C. (erver on the #nternal network
when it restarts. /ote that on a production network where the '<C. server is located on a
network segent reote fro the #(& (erver )**4 firewall, all interposed routers will need to
have @OO%. or '<C. relay enabled so that '<C. reAuests fro the firewall can reach the reote
'<C. servers.
#reate an Access $ule Allowin% VPN #lients Access to
the Internal Network
%he #(& (erver )**4 firewall will be able to accept incoing -./ connections after the restart.
<owever, the -./ clients cannot access any resources on the #nternal network because there are
no &ccess 3ules enabling this access. 7ou ust create an &ccess 3ule that allows ebers of the
-./ clients network access to the #nternal network. #n contrast to other cobined firewall -./
server solutions, the #(& (erver )**4 firewall -./ server applies access controls for network
access to -./ clients.
#n this exaple you will create an &ccess 3ule allowing all traffic to pass fro the -./ clients
network to the #nternal network. #n a production environent you would create ore restrictive
access rules so that users on the -./ clients network have access only to resource they reAuire.
#;ll show you how to create ore sophisticated user0group based access controls on -./ clients in
future articles on the www.isaserver.org site and in our #(& (erver )**4 firewall book.
.erfor the following steps to create an &ccess 3ule to allow -./ clients unrestricted access to the
#nternal network=
8. #n the Microsoft .nternet "ecurity and Acceleration "er1er +!!2 anageent
console, expand the server nae and click the 8irewall Policy node. 3ight click the
8irewall Policy node, point to New and click Access 7ule.
). #n the /elcome to t(e New Access 7ule /i9ard page, enter a nae for the rule in the
Access 7ule name text box. #n this exaple we will nae the rule VPN Client to
.nternal. Click Next.
3. On the 7ule Action page, select the Allow option and click Next.
4. On the Protocols page, select the All outbound protocols option in the ,(is rule
applies to list. Click Next.
fig8*
5. On the Access 7ule "ources page, click the Add button. On the Add Networ* 'ntities
dialog box, click the Networ*s folder and double click on VPN Clients. Click Close.
6. Click Next on the Access 7ule "ources page.
!. On the Access 7ule %estinations page, click the Add button. On the Add Networ*
'ntities dialog box, click the Networ*s folder and double click on .nternal. Click Close.
". On the &ser "ets page, accept the default setting, All &sers, and click Next.
$. Click 8inis( on the Completing t(e New Access 7ule /i9ard page.
8*. Click Apply to save the changes and update the firewall policy.
88. Click OK in the Apply New Configuration dialog box. %he -./ client policy is now the
top listed &ccess 3ule in the &ccess .olicy list.
Enable &ial'in Access for the Ad(inistrator Account
#n non,native ode &ctive 'irectory doains, all user accounts have dial,in access disabled by
default. 7ou ust enable dial,in access on a per account basis for these non,/ative ode &ctive
'irectory doains. #n contrast, native ode &ctive 'irectory doains have dial,in access
controlled by 3eote &ccess .olicy by default. +indows /% 4.* doains always have dial,in
access controlled on a per user account basis.
#n our current exaple, the &ctive 'irectory is in +indows (erver )**3 ixed ode, so we will
need to anually change the dial,in settings on the doain user account. # highly recoend
that if you do not have any +indows /% 4.* doain controllers on your network, that you elevate
your doain functionality level.
.erfor the following steps on the doain controller to enable 'ial,in access for the &dinistrator
account=
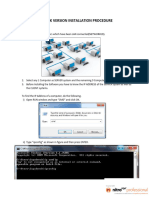
8. Click "tart and point to Administrati1e ,ools. Click Acti1e %irectory &sers and
Computers.
). #n the Acti1e %irectory &sers and Computers console, click on the &sers node in the
left pane. 'ouble click on the Administrator account in the right pane of the console.
3. Click on the %ial6in tab. #n the 7emote Access Permission 3%ial6in or VPN4 frae,
select the Allow access option. Click Apply and click OK.
f
4. Close the Acti1e %irectory &sers and Computers console.
"est the PP"P VPN #onnection
%he #(& (erver )**4 -./ server is now ready to accept -./ client connections.
.erfor the following steps to test the -./ (erver=
8. On the +indows )*** external client achine, right click the My Networ* Places icon on
the desktop and click Properties.
). 'ouble click the Ma*e New Connection icon in the Networ* and %ial6up Connections
window.
3. Click Next on the /elcome to t(e Networ* Connection /i9ard page.
4. On the Networ* Connection ,ype page, select the Connect to a pri1ate networ*
t(roug( t(e .nternet option and click Next.
5. On the %estination Address page, enter the #. address :+$;<$$=! in the 5ost
name or .P address text box. Click Next.
6. On the Connection A1ailability page, select the 8or all users option and click Next.
!. 9ake no changes on the .nternet Connection "(aring page and click Next.
". On the Completing t(e Networ* Connection /i9ard page, enter a nae for the -./
connection in the ,ype t(e name you want to use for t(is connection text box. #n
this exaple, we;ll nae the connection ."A VPN. Confir that there is a checkark in
the Add a s(ortcut to my des*top checkbox. Click 8inis(.
$. #n the Connect ."A VPN dialog box, enter the user nae M"8.7'/A##>administrator
and the password for the adinistrator user account. Click Connect.
fig85
8*. %he -./ client establishes a connection with the #(& (erver )**4 -./ server. Click OK in
the Connection Complete dialog box inforing that the connection is established.
88. 'ouble click on the connection icon in the syste tray and click the %etails tab. 7ou can
see that MPP' +< encryption is used to protect the data and the #. address assigned to
the -./ client.
8). Click "tart and then click the 7un coand. #n the 7un dialog box, enter
>>'?C5ANG'+!!@A' in the Open text box and click OK. %he shares on the doain
controller coputer appear. Close the windows displaying the doain controllers contents.
/ote that we were able to use a single label nae to connect to the doain controller
because the #(& (erver )**4 firewall -./ server assigned the -./ client a +#/( server
address.
83. 3ight click the connection icon in the syste tray and click %isconnect.
You might also like
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5783)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (838)
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (537)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (890)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (399)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (587)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (265)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (72)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (344)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2219)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (119)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (821)
- shk4000tl InstructivoDocument14 pagesshk4000tl InstructivoAgus Arevalo BaezNo ratings yet
- WCDMA OMC Operation GuideDocument220 pagesWCDMA OMC Operation Guidesukriti_ericsson50% (2)
- Qualcomm Snapdragon 662 Mobile Platform Product BriefDocument2 pagesQualcomm Snapdragon 662 Mobile Platform Product Briefichida_hiroshiNo ratings yet
- Datasheet Eprom ST 27C512Document19 pagesDatasheet Eprom ST 27C512Rafael SaranholiNo ratings yet
- Command Line and File EditingDocument24 pagesCommand Line and File EditingINVISIBLE - Abby HartadiNo ratings yet
- Ethernet Networking Tutorial PDFDocument2 pagesEthernet Networking Tutorial PDFKariNo ratings yet
- The Citizen's Portal - Seven Seas TechnologiesDocument11 pagesThe Citizen's Portal - Seven Seas TechnologiesICT AUTHORITYNo ratings yet
- Translate - Google SDocument1 pageTranslate - Google SJoan VeranoNo ratings yet
- Current LogDocument6 pagesCurrent LogMaria Luis FonsiNo ratings yet
- Corel DrawDocument23 pagesCorel DrawananthakrishnanNo ratings yet
- Client-Server Technology, Practices of The Practical LayerDocument4 pagesClient-Server Technology, Practices of The Practical LayerResearch ParkNo ratings yet
- Bit Twiddling HacksDocument30 pagesBit Twiddling Hacksİhsan TürkoğluNo ratings yet
- How To Create Signed Based Reclassification in Group ReportingDocument9 pagesHow To Create Signed Based Reclassification in Group ReportingJose EximenoNo ratings yet
- Old ResumeDocument4 pagesOld ResumeAbhijeet ShindeNo ratings yet
- Huawei HG8245H ONT DatasheetDocument4 pagesHuawei HG8245H ONT DatasheetAgus WahyuNo ratings yet
- Website Design For Wrist WatchesDocument14 pagesWebsite Design For Wrist WatchesPradeep RajNo ratings yet
- 2020 State of BPMDocument63 pages2020 State of BPMerikafvarcarNo ratings yet
- Embedded System1 - LabDocument23 pagesEmbedded System1 - LabsnehaNo ratings yet
- Abandoned Cart Emails: A Data-Driven Guide To Recovering Lost SalesDocument37 pagesAbandoned Cart Emails: A Data-Driven Guide To Recovering Lost SalesTochi Krishna AbhishekNo ratings yet
- CSP U7l02 Activity GuideDocument2 pagesCSP U7l02 Activity Guideapi-5241415840% (1)
- ACS ICT Proposal For Author's Solution Revision 3Document34 pagesACS ICT Proposal For Author's Solution Revision 3Ban Darl PonshiNo ratings yet
- Cnctrain Network - Installation ProcedureDocument8 pagesCnctrain Network - Installation Procedurepaijo klimpritNo ratings yet
- Atom Processor E3900 Series Product BriefDocument4 pagesAtom Processor E3900 Series Product BriefluluioNo ratings yet
- Intro To HTML 5Document24 pagesIntro To HTML 5Kawaii GlamourNo ratings yet
- GBSS14.0 Feature Activation Guide (06) (PDF) - enDocument1,015 pagesGBSS14.0 Feature Activation Guide (06) (PDF) - enpepilve100% (1)
- 1.13938525 24098318Document5 pages1.13938525 24098318Sam VuppalNo ratings yet
- Compare Samsung Tab A8 Wifi (X200) Vs Tab A8 LTE (X205)Document3 pagesCompare Samsung Tab A8 Wifi (X200) Vs Tab A8 LTE (X205)anikfajar136No ratings yet
- Join Seon-ho's Fan Cafe in 7 Easy StepsDocument33 pagesJoin Seon-ho's Fan Cafe in 7 Easy StepsTyas PuspitaningrumNo ratings yet
- STEP 7 Professional Programming and Configuring According To IEC 61131-3Document16 pagesSTEP 7 Professional Programming and Configuring According To IEC 61131-3scribd010% (1)
- GPAC DAMI Reference GuideDocument281 pagesGPAC DAMI Reference GuideMous100% (4)