Professional Documents
Culture Documents
Chapter 3 Lab A: Securing Administrative Access Using AAA and Radius
Uploaded by
fernaleo0 ratings0% found this document useful (0 votes)
39 views25 pagesOriginal Title
CCNASv1.1_Chp03_Lab-A_AAA-RADIUS_Student.doc
Copyright
© © All Rights Reserved
Available Formats
DOC, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
© All Rights Reserved
Available Formats
Download as DOC, PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
39 views25 pagesChapter 3 Lab A: Securing Administrative Access Using AAA and Radius
Uploaded by
fernaleoCopyright:
© All Rights Reserved
Available Formats
Download as DOC, PDF, TXT or read online from Scribd
You are on page 1of 25
CCNA Security
Chapter 3 Lab A: Securing Administrative Access Using AAA and
RADIUS
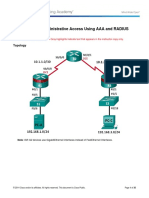
Topoogy
Note: ISR G2 devices have Gigabit Ethernet interfaces instead of Fast Ethernet Interfaces.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 1 of 2(
CCNA Security
I! Addressing Tabe
Device Inter"ace I! Address Subnet #as$ De"aut %ate&ay S&itch !ort
R1 FA")1 12.1*+.1.1 2((.2((.2((." ,)A S1 FA")(
S")")" -.CE/ 1".1.1.1 2((.2((.2((.2(2 ,)A ,)A
R2 S")")" 1".1.1.2 2((.2((.2((.2(2 ,)A ,)A
S")")1 -.CE/ 1".2.2.2 2((.2((.2((.2(2 ,)A ,)A
R0 FA")1 12.1*+.0.1 2((.2((.2((." ,)A S0 FA")(
S")")1 1".2.2.1 2((.2((.2((.2(2 ,)A ,)A
'C1A ,IC 12.1*+.1.0 2((.2((.2((." 12.1*+.1.1 S1 FA")*
'C1C ,IC 12.1*+.0.0 2((.2((.2((." 12.1*+.0.1 S0 FA")1+
'b(ectives
!art ): *asic Net&or$ Device Con"iguration
Config&re basic settings s&ch as host na#e$ interface I' addresses$ and access pass2ords.
Config&re static ro&ting.
!art +: Con"igure Loca Authentication
Config&re a local database &ser and local access for the console$ vty$ and a&3 lines.
%est the config&ration.
!art 3: Con"igure Loca Authentication Using AAA
Config&re the local &ser database &sing Cisco I4S.
Config&re AAA local a&thentication &sing Cisco I4S.
Config&re AAA local a&thentication &sing CC'.
%est the config&ration.
!art ,: Con"igure Centrai-ed Authentication Using AAA and RADIUS
Install a RA.I5S server on a co#p&ter.
Config&re &sers on the RA.I5S server.
5se Cisco I4S to config&re AAA services on a ro&ter to access the RA.I5S server for a&thentication.
5se CC' to config&re AAA services on a ro&ter to access the RA.I5S server for a&thentication.
%est the AAA RA.I5S config&ration.
*ac$ground
%he #ost basic for# of ro&ter access sec&rity is to create pass2ords for the console$ vty$ and a&3 lines. A
&ser is pro#pted for only a pass2ord 2hen accessing the ro&ter. Config&ring a privileged E6EC #ode enable
secret pass2ord f&rther i#proves sec&rity$ b&t still only a basic pass2ord is re7&ired for each #ode of access.
In addition to basic pass2ords$ specific &serna#es or acco&nts 2ith varying privilege levels can be defined in
the local ro&ter database that can apply to the ro&ter as a 2hole. 8hen the console$ vty$ or a&3 lines are
config&red to refer to this local database$ the &ser is pro#pted for a &serna#e and a pass2ord 2hen &sing
any of these lines to access the ro&ter.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 2 of 2(
CCNA Security
Additional control over the login process can be achieved &sing a&thentication$ a&thori9ation$ and acco&nting
-AAA/. For basic a&thentication$ AAA can be config&red to access the local database for &ser logins$ and
fallbac: proced&res can also be defined. ;o2ever$ this approach is not very scalable beca&se it #&st be
config&red on every ro&ter. %o ta:e f&ll advantage of AAA and achieve #a3i#&# scalability$ AAA is &sed in
con<&nction 2ith an e3ternal %ACACS= or RA.I5S server database. 8hen a &ser atte#pts to log in$ the
ro&ter references the e3ternal server database to verify that the &ser is logging in 2ith a valid &serna#e and
pass2ord.
In this lab$ yo& b&ild a #<i1ro&ter net2or: and config&re the ro&ters and hosts. >o& 2ill then &se C?I
co##ands and CC' tools to config&re ro&ters 2ith basic local a&thentication by #eans of AAA. >o& 2ill
install RA.I5S soft2are on an e3ternal co#p&ter and &se AAA to a&thenticate &sers 2ith the RA.I5S server.
Note: %he ro&ter co##ands and o&tp&t in this lab are fro# a Cisco 1+@1 2ith Cisco I4S Release 12.@-2"/%
-Advance I' i#age/. 4ther ro&ters and Cisco I4S versions can be &sed. See the Ro&ter Interface S&##ary
table at the end of the lab to deter#ine 2hich interface identifiers to &se based on the e7&ip#ent in the lab.
.epending on the ro&ter #odel and Cisco I4S version$ the co##ands available and o&tp&t prod&ced #ight
vary fro# 2hat is sho2n in this lab.
Note: Aa:e s&re that the ro&ters and s2itches have been erased and have no start&p config&rations.
Re.uired Resources
0 ro&ters -Cisco 1+@1 2ith Cisco I4S Release 12.@-2"/%1 or co#parable/
2 s2itches -Cisco 2*" or co#parable/
'C1AB 8indo2s 6'$ Cista or 8indo2s D 2ith CC' 2.( E RA.I5S server soft2are available
'C1CB 8indo2s 6'$ Cista or 8indo2s D 2ith CC' 2.(
Serial and Ethernet cables as sho2n in the topology
Rollover cables to config&re the ro&ters via the console
CC! Notes:
Refer to Chp "" ?ab A for instr&ctions on ho2 to install and r&n CC'. ;ard2are)soft2are
reco##endations for CC' incl&de 8indo2s 6'$ Cista$ or 8indo2s D 2ith Fava version 1.*."G11 &p to
1.*."G21$ Internet E3plorer *." or above and Flash 'layer Cersion 1".".12.0* and later.
If the 'C on 2hich CC' is installed is r&nning 8indo2s Cista or 8indo2s D$ it #ay be necessary to
right1clic: on the CC' icon or #en& ite#$ and choose Run as administrator.
In order to r&n CC'$ it #ay be necessary to te#porarily disable antivir&s progra#s and 4)S fire2alls.
Aa:e s&re that all pop1&p bloc:ers are t&rned off in the bro2ser.
!art ): *asic Net&or$ Device Con"iguration
In 'art 1 of this lab$ yo& set &p the net2or: topology and config&re basic settings$ s&ch as the interface I'
addresses$ static ro&ting$ device access$ and pass2ords.
All steps sho&ld be perfor#ed on ro&ters R1 and R0. 4nly steps 1$ 2$ 0 and * need to be perfor#ed on R2.
%he proced&re for R1 is sho2n here as an e3a#ple.
Step ): Cabe the net&or$ as sho&n in the topoogy/
Attach the devices sho2n in the topology diagra#$ and cable as necessary.
Step +: Con"igure basic settings "or each router/
Config&re host na#es as sho2n in the topology.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 0 of 2(
CCNA Security
Config&re the interface I' addresses as sho2n in the I' addressing table.
Config&re a cloc: rate for the ro&ters 2ith a .CE serial cable attached to their serial interface.
R1(config)# interface S0/0/0
R1(config-if)# clock rate 64000
%o prevent the ro&ter fro# atte#pting to translate incorrectly entered co##ands as tho&gh they 2ere host na#es$
disable .,S loo:&p.
R1(config)# no ip domain-lookup
Step 3: Con"igure static routing on the routers/
a. Config&re a static defa< ro&te fro# R1 to R2 and fro# R0 to R2.
Config&re a static ro&te fro# R2 to the R1 ?A, and fro# R2 to the R0 ?A,.
Step ,: Con"igure !C host I! settings/
Config&re a static I' address$ s&bnet #as:$ and defa< gate2ay for 'C1A and 'C1C$ as sho2n in the I'
addressing table.
Step 0: 1eri"y connectivity bet&een !C2A and R3/
a. 'ing fro# R1 to R0.
8ere the ping res<s s&ccessf&lH GGGGG
If the pings are not s&ccessf&l$ tro&bleshoot the basic device config&rations before contin&ing.
b. 'ing fro# 'C1A on the R1 ?A, to 'C1C on the R0 ?A,.
8ere the ping res<s s&ccessf&lH GGGGG
If the pings are not s&ccessf&l$ tro&bleshoot the basic device config&rations before contin&ing.
Note: If yo& can ping fro# 'C1A to 'C1C$ yo& have de#onstrated that static ro&ting is config&red and
f&nctioning correctly. If yo& cannot ping b&t the device interfaces are &p and I' addresses are correct$ &se
the show run and show ip route co##ands to help identify ro&ting protocol1related proble#s.
Step 3: Save the basic running con"iguration "or each router/
5se the Trans"er 4 Capture te5t option in ;yper%er#inal or so#e other #ethod to capt&re the r&nning
configs for each ro&ter. Save the three files so that they can be &sed to restore configs later in the lab.
Step 6: Con"igure and encrypt pass&ords on R) and R3/
Note: 'ass2ords in this tas: are set to a #ini#&# of 1" characters b&t are relatively si#ple for the
benefit of perfor#ing the lab. Aore co#ple3 pass2ords are reco##ended in a prod&ction net2or:.
For this step$ config&re the sa#e settings for R1 and R0. Ro&ter R1 is sho2n here as an e3a#ple.
a. Config&re a #ini#&# pass2ord length.
5se the security passwords co##and to set a #ini#&# pass2ord length of 1" characters.
R1(config)# security passwords min-length 10
b. Config&re the enable secret pass2ord on both ro&ters.
R1(config)# enable secret cisco1234
c. Config&re the basic console$ a&3iliary port$ and vty lines.
d. Config&re a console pass2ord and enable login for ro&ter R1. For additional sec&rity$ the e!ec-
timeout co##and ca&ses the line to log o&t after ( #in&tes of inactivity. %he logging
synchronous co##and prevents console #essages fro# interr&pting co##and entry.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age @ of 2(
CCNA Security
Note: %o avoid repetitive logins d&ring this lab$ the e3ec ti#eo&t can be set to " "$ 2hich prevents it
fro# e3piring. ;o2ever$ this is not considered a good sec&rity practice.
R1(config)# line console 0
R1(config-line)# password ciscoconpass
R1(config-line)# e!ec-timeout 0
R1(config-line)# login
R1(config-line)# logging synchronous
e. Config&re a pass2ord for the a&3 port for ro&ter R1.
R1(config)# line au! 0
R1(config-line)# password ciscoau!pass
R1(config-line)# e!ec-timeout 0
R1(config-line)# login
f. Config&re the pass2ord on the vty lines for ro&ter R1.
R1(config)# line "ty 0 4
R1(config-line)# password cisco"typass
R1(config-line)# e!ec-timeout 0
R1(config-line)# login
g. Encrypt the console$ a&3$ and vty pass2ords.
R1(config)# ser"ice password-encryption
h. Iss&e the show run co##and. Can yo& read the console$ a&3$ and vty pass2ordsH 8hy or 2hy
notH GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
Step 7: Con"igure a ogin &arning banner on routers R) and R3/
a. Config&re a 2arning to &na&thori9ed &sers &sing a #essage1of1the1day -A4%./ banner 2ith the
banner motd co##and. 8hen a &ser connects to the ro&ter$ the A4%. banner appears before the
login pro#pt. In this e3a#ple$ the dollar sign -I/ is &sed to start and end the #essage.
R1(config)# banner motd #$nauthori%ed access strictly prohibited and
prosecuted to the full e!tent of the law#
R1(config)# e!it
b. Iss&e the show run co##and. 8hat does the I convert to in the o&tp&tH
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
c. E3it privileged E6EC #ode by &sing the disable or e!it co##and and press 8nter to get started.
.oes the A4%. banner loo: li:e 2hat yo& e3pectedH GGGGGG
Note: If it does not$ <&st re1create it &sing the banner motd co##and.
Step 9: Save the basic con"igurations/
Save the r&nning config&ration to the start&p config&ration fro# the privileged E6EC pro#pt.
R1# copy running-config startup-config
!art +: Con"igure Loca Authentication
In 'art 2 of this lab$ yo& config&re a local &serna#e and pass2ord and change the access for the console$ a&3$
and vty lines to reference the ro&terJs local database for valid &serna#es and pass2ords. 'erfor# all steps on R1
and R0. %he proced&re for R1 is sho2n here.
Step ): Con"igure the oca user database/
a. Create a local &ser acco&nt 2ith A.( hashing to encrypt the pass2ord.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age ( of 2(
CCNA Security
R1(config)# username user01 secret user01pass
b. E3it global config&ration #ode and display the r&nning config&ration. Can yo& read the &serJs
pass2ordH GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
Step +: Con"igure oca authentication "or the consoe ine and ogin/
a. Set the console line to &se the locally defined login &serna#es and pass2ords.
R1(config)# line console 0
R1(config-line)# login local
b. E3it to the initial ro&ter screen that displaysB
&1 con0 is now a"ailable' (ress &)*$&+ to get started.
c. ?og in &sing the &ser"1 acco&nt and pass2ord previo&sly defined.
d. 8hat is the difference bet2een logging in at the console no2 and previo&slyH
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
e. After logging in$ iss&e the show run co##and. 8ere yo& able to iss&e the co##andH 8hy or 2hy
notH GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
f. Enter privileged E6EC #ode &sing the enable co##and. 8ere yo& pro#pted for a pass2ordH 8hy
or 2hy notH GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
Step 3: Test the ne& account by ogging in "rom a Tenet session/
a. Fro# 'C1A$ establish a %elnet session 2ith R1.
PC-A> telnet 1,2'16-'1'1
b. 8ere yo& pro#pted for a &ser acco&ntH 8hy or 2hy notH
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
c. 8hat pass2ord did yo& &se to loginH GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
d. Set the vty lines to &se the locally defined login acco&nts.
R1(config)# line "ty 0 4
R1(config-line)# login local
e. Fro# 'C1A$ telnet R1 to R1 again.
PC-A> telnet 1,2'16-'1'1
f. 8ere yo& pro#pted for a &ser acco&ntH 8hy or 2hy notH GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
g. ?og in as user:) 2ith a pass2ord of user:)pass.
h. 8hile connected to R1 via %elnet$ access privileged E6EC #ode 2ith the enable co##and.
i. 8hat pass2ord did yo& &seH GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
<. For added sec&rity$ set the a&3 port to &se the locally defined login acco&nts.
R1(config)# line au! 0
R1(config-line)# login local
:. End the %elnet session 2ith the e!it co##and.
Step ,: Save the con"iguration on R)/
a. Save the r&nning config&ration to the start&p config&ration fro# the privileged E6EC pro#pt.
R1# copy running-config startup-config
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age * of 2(
CCNA Security
b. 5se ;yper%er#inal or another #eans to save the R1 r&nning config&ration fro# 'arts 1 and 2 of this
lab and edit it so that it can be &sed to restore the R1 config later in the lab.
Note: Re#ove all occ&rrences of K1 1 Aore 1 1.L Re#ove any co##ands that are not related to the ite#s
yo& config&red in 'arts 1 and 2 of the lab$ s&ch as the Cisco I4S version n&#ber$ no service pad$ and so
on. Aany co##ands are entered a&to#atically by the Cisco I4S soft2are. Also replace the encrypted
pass2ords 2ith the correct ones specified previo&sly.
Step 0: !er"orm steps ) through , on R3 and save the con"iguration/
a. Save the r&nning config&ration to the start&p config&ration fro# the privileged E6EC pro#pt.
R3# copy running-config startup-config
b. 5se ;yper%er#inal or another #eans to save the R0 r&nning config&ration fro# 'arts 1 and 2 of this
lab and edit it so that it can be &sed to restore the R0 config later in the lab.
!art 3: Con"igure Loca Authentication Using AAA on R3
Tas$ ): Con"igure the Loca User Database Using Cisco I'S
Note: %o config&re AAA &sing CC'$ s:ip to %as: 0.
Step ): Con"igure the oca user database/
a. Create a local &ser acco&nt 2ith A.( hashing to encrypt the pass2ord.
R3(config)# username .dmin01 pri"ilege 1 secret .dmin01pass
b. E3it global config&ration #ode and display the r&nning config&ration. Can yo& read the &serJs
pass2ordH GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
Tas$ +: Con"igure AAA Loca Authentication Using Cisco I'S
Step ): 8nabe AAA services/
a. 4n R0$ enable services 2ith the global config&ration co##and aaa new-model. Meca&se yo& are
i#ple#enting local a&thentication$ &se local a&thentication as the first #ethod$ and no a&thentication
as the secondary #ethod.
If yo& 2ere &sing an a&thentication #ethod 2ith a re#ote server$ s&ch as %ACACS= or RA.I5S$ yo&
2o&ld config&re a secondary a&thentication #ethod for fallbac: if the server is &nreachable. ,or#ally$
the secondary #ethod is the local database. In this case$ if no &serna#es are config&red in the local
database$ the ro&ter allo2s all &sers login access to the device.
b. Enable AAA services.
R3(config)# aaa new-model
Step +: Impement AAA services "or consoe access using the oca database/
a. Create the defa< login a&thentication list by iss&ing the aaa authentication login default
method1[method2][method3] co##and 2ith a #ethod list &sing the local and none :ey2ords.
R3(config)# aaa authentication login default local none
Note: If yo& do not set &p a defa< login a&thentication list$ yo& co&ld get loc:ed o&t of the ro&ter and
be forced to &se the pass2ord recovery proced&re for yo&r specific ro&ter.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age D of 2(
CCNA Security
b. E3it to the initial ro&ter screen that displaysB R3 con: is no& avaiabe; !ress R8TURN to get
started.
c. ?og in to the console as Admin:) 2ith a pass2ord of Admin:)pass. Re#e#ber that pass2ords are
case1sensitive. 8ere yo& able to log inH 8hy or 2hy notH
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
Note: If yo&r session 2ith the console port of the ro&ter ti#es o&t$ yo& #ight have to log in &sing the
defa< a&thentication list.
d. E3it to the initial ro&ter screen that displaysB &3 con0 is now a"ailable/ (ress &)*$&+ to
get started.
e. Atte#pt to log in to the console as baduser 2ith any pass2ord. 8ere yo& able to log inH 8hy or 2hy
notH GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
f. If no &ser acco&nts are config&red in the local database$ 2hich &sers are per#itted to access the
deviceH GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
Step 3: Create a AAA authentication pro"ie "or Tenet using the oca database/
a. Create a &ni7&e a&thentication list for %elnet access to the ro&ter. %his does not have the fallbac: of
no a&thentication$ so if there are no &serna#es in the local database$ %elnet access is disabled. %o
create an a&thentication profile that is not the defa<$ specify a list na#e of %E?,E%G?I,ES and
apply it to the vty lines.
R3(config)# aaa authentication login *)0+)*102+)S local
R3(config)# line "ty 0 4
R3(config-line)# login authentication *)0+)*102+)S
b. Cerify that this a&thentication profile is &sed by opening a %elnet session fro# 'C1C to R0.
PC-C> telnet 1,2'16-'3'1
Trying 192.168.3.1 ... Open
c. ?og in as Admin:) 2ith a pass2ord of Admin:)pass. 8ere yo& able to loginH 8hy or 2hy notH
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
d. E3it the %elnet session 2ith the e!it co##and$ and %elnet to R0 again.
e. Atte#pt to log in as baduser 2ith any pass2ord. 8ere yo& able to loginH 8hy or 2hy notH
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
Tas$ 3: <'ptiona= Con"igure AAA Loca Authentication Using Cisco CC!
>o& can also &se CC' to config&re the ro&ter to s&pport AAA.
Note: If yo& config&red R0 AAA a&thentication &sing Cisco I4S co##ands in %as:s 1 and 2$ yo& can s:ip this
tas:. If yo& perfor#ed %as:s 1 and 2 and yo& 2ant to perfor# this tas:$ yo& sho&ld restore R0 to its basic
config&ration. See 'art @$ Step 1 for the proced&re to restore R0 to its basic config&ration.
Even if yo& do not perfor# this tas:$ read thro&gh the steps to beco#e fa#iliar 2ith the CC' process.
Step ): Impement AAA services and >TT! router access prior to starting CC!/
a. Fro# the C?I global config #ode$ enable a ne2 AAA #odel.
R3(config)# aaa new-model
b. Enable the ;%%' server on R0 for CC' access.
R3(config)# ip http ser"er
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age + of 2(
CCNA Security
Note: For #a3i#&# sec&rity$ enable sec&re http server by &sing the ip http secure-ser"er
co##and.
c. Add a &ser na#ed admin to the local database.
R3(config)# username admin pri"ilege 1 secret cisco1234
d. ;ave CC' &se the local database to a&thenticate 2eb sessions.
R3(config)# ip http authentication local
Step +: Access CC! and discover R3/
a. Start CC' on 'C1C. In the Aanage .evices 2indo2$ add R0 I' address 12.1*+.0.1 in the first I'
address field. Enter admin in the 5serna#e field$ and cisco)+3,0 in the 'ass2ord field.
b. At the CC' .ashboard$ clic: the Discover b&tton to discover and connect to R0. If discovery fails$
clic: the Discovery Detais b&tton to deter#ine the proble#.
Step 3: Use CC! to create an administrative user/
a. Clic: the Con"igure b&tton at the top of the screen.
b. Choose Router 4 Router Access 4 User Accounts?1ie&.
c. In the 5ser Acco&nts)Cie2 2indo2$ clic: Add.
d. In the Add an Acco&nt 2indo2$ enter Admin:) in the 5serna#e field.
e. Enter the pass2ord Admin:)pass in the ,e2 'ass2ord and Confir# ,e2 'ass2ord fields.
-Re#e#ber$ pass2ords are case1sensitive./
f. Confir# that the 8ncrypt pass&ord using #D0 hash agorithm chec: bo3 is chec:ed.
g. Select )0 fro# the 'rivilege ?evel drop1do2n list and clic: '@.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age of 2(
CCNA Security
h. In the .eliver Config&ration to Ro&ter 2indo2$ #a:e s&re that the Save R&nning Config to Ro&terJs
Start&p Config chec: bo3 is chec:ed$ and clic: Deiver.
i. In the Co##ands .elivery Stat&s 2indo2$ clic: '@.
Step ,: Create AAA method ist "or ogin/
a. Clic: the Con"igure b&tton at the top of the screen.
b. Choose Router 4 AAA 4 Authentication !oicies 4 Login.
c. In the A&thentication ?ogin 2indo2$ clic: Add.
d. In the Add a Aethod ?ist for A&thentication ?ogin 2indo2$ verify that De"aut is in the ,a#e field.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 1" of 2(
CCNA Security
e. Clic: Add in the Aethods section.
f. In the Select Aethod ?ist-s/ for A&thentication ?ogin 2indo2$ choose oca and clic: '@. %a:e note of
the other #ethods listed$ 2hich incl&de RA.I5S -gro&p radi&s/ and %ACACS= -gro&p tacacs=/.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 11 of 2(
CCNA Security
g. Clic: '@ to close the 2indo2.
h. Repeat steps @f and @g. Choose none as a second a&thentication #ethod and clic: the '@ b&tton
2hen done.
i. In the .eliver Config&ration to Ro&ter 2indo2$ #a:e s&re that the Save R&nning Config to Ro&terNs
Start&p Config chec:bo3 is chec:ed$ and clic: Deiver. In the Co##ands .elivery Stat&s 2indo2$
clic: '@.
<. 8hat co##and 2as delivered to the ro&terH
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
Step 0: 1eri"y the AAA username and pro"ie "or consoe ogin/
a. E3it to the initial ro&ter screen that displaysB
&3 con0 is now a"ailable/ (ress &)*$&+ to get started.
b. ?og in to the console as Admin:) 2ith a pass2ord of Admin:)pass. 8ere yo& able to loginH 8hy or
2hy notH GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
c. E3it to the initial ro&ter screen that displaysB
&3 con0 is now a"ailable/ (ress &)*$&+ to get started.
d. Atte#pt to log in to the console as baduser. 8ere yo& able to loginH 8hy or 2hy notH
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
If no &ser acco&nts are config&red in the local database$ 2hich &sers are per#itted to access the
deviceH GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
e. ?og in to the console as Admin:) 2ith a pass2ord of Admin:)pass. Access privileged E6EC #ode
&sing the enable secret pass2ord cisco)+3,0 and then sho2 the r&nning config. 8hat co##ands
are associated 2ith the CC' sessionH
___________________________________________________________________________
_________________________________________________________________________
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 12 of 2(
CCNA Security
Tas$ ,: 'bserve AAA Authentication Using Cisco I'S Debug
In this tas:$ yo& &se the debug co##and to observe s&ccessf&l and &ns&ccessf&l a&thentication atte#pts.
Step ): 1eri"y that the system coc$ and debug time stamps are con"igured correcty/
a. Fro# the R0 &ser or privileged E6EC #ode pro#pt$ &se the show clock co##and to deter#ine
2hat the c&rrent ti#e is for the ro&ter. If the ti#e and date are incorrect$ set the ti#e fro# privileged
E6EC #ode 2ith the co##and clock set 334554SS 66 month 7777. An e3a#ple is provided
here for R0.
R3# clock set 1441400 26 6ecember 200-
b. Cerify that detailed ti#e1sta#p infor#ation is available for yo&r deb&g o&tp&t &sing the show run
co##and. %his co##and displays all lines in the r&nning config that incl&de the te3t Kti#esta#psL.
R3# show run 8 include timestamps
er!ice "i#e"$#p %e&'g %$"e"i#e #ec
er!ice "i#e"$#p log %$"e"i#e #ec
c. If the ser"ice timestamps debug co##and is not present$ enter it in global config #ode.
R3(config)# ser"ice timestamps debug datetime msec
R3(config)# e!it
d. Save the r&nning config&ration to the start&p config&ration fro# the privileged E6EC pro#pt.
R3# copy running-config startup-config
Step +: Use debug to veri"y user access/
a. Activate deb&gging for AAA a&thentication.
R3# debug aaa authentication
AAA A'"(en"ic$"ion %e&'gging i on
b. Start a %elnet session fro# 'C1C to R0.
c. ?og in 2ith &serna#e Admin:) and pass2ord Admin:)pass. 4bserve the AAA a&thentication
events in the console session 2indo2. .eb&g #essages si#ilar to the follo2ing sho&ld be displayed.
R3#
)ec 26 1*+36+*2.323+ AAA,-./)(000000A1)+ -in% i,f
)ec 26 1*+36+*2.323+ AAA,A2T34/,5O6./ (000000A1)+ Pic7 #e"(o% li"
8%ef$'l"8
d. Fro# the %elnet 2indo2$ enter privileged E6EC #ode. 5se the enable secret pass2ord of
cisco)+3,0. .eb&g #essages si#ilar to the follo2ing sho&ld be displayed. In the third entry$ note the
&serna#e -Ad#in"1/$ virt&al port n&#ber -tty1@/$ and re#ote %elnet client address -12.1*+.0.0/.
Also note that the last stat&s entry is K'ASS.L
R3#
)ec 26 1*+*0+1*.*31+ AAA+ p$re n$#e9""y19* i%& "ype9-1 ""y9-1
)ec 26 1*+*0+1*.*31+ AAA+ n$#e9""y19* fl$g90:11 "ype91 (elf90 lo"90
$%$p"er90 por"919* c($nnel90
)ec 26 1*+*0+1*.*31+ AAA,;4;OR<+ cre$"e_'er (0:6*--1110) user9:.dmin01:
ruser9: +$00: ds090 port9:tty1,4: rem1addr9:1,2'16-'3'3:
$'"(en_"ype9A=C.. er!ice94/A-54 pri!911 ini"i$l_"$7_i%9808> !rf9
(i%90)
)ec 26 1*+*0+1*.*31+ AAA,A2T34/,=TART (2*6?62*222)+ por"98""y19*8
li"988 $c"ion95O6./ er!ice94/A-54
)ec 26 1*+*0+1*.*31+ AAA,A2T34/,=TART (2*6?62*222)+ non-conole en$&le @
%ef$'l" "o en$&le p$Aor%
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 10 of 2(
CCNA Security
)ec 26 1*+*0+1*.*31+ AAA,A2T34/,=TART (2*6?62*222)+ ;e"(o%94/A-54
R3#
)ec 26 1*+*0+1*.*31+ AAA,A2T34/(2*6?62*222)+ ="$"'964TPA==
R3#
)ec 26 1*+*0+19.2?1+ AAA,A2T34/,CO/T (2*6?62*222)+ con"in'e_login
('er98('n%ef)8)
)ec 26 1*+*0+19.2?1+ AAA,A2T34/(2*6?62*222)+ ="$"'964TPA==
)ec 26 1*+*0+19.2?1+ AAA,A2T34/,CO/T (2*6?62*222)+ ;e"(o%94/A-54
6ec 26 144404,'2-;4 .../.$*3)+<246;624222=4 Status9(.SS
)ec 26 1*+*0+19.28?+ AAA,;4;OR<+ free_'er (0:6*--1110) 'er98/2558
r'er98/2558 por"98""y19*8 re#_$%%r98192.168.3.38 $'"(en_"ype9A=C..
er!ice94/A-54 pri!911 !
rf9 (i%90)
e. Fro# the %elnet 2indo2$ e3it privileged E6EC #ode &sing the disable co##and. %ry to enter
privileged E6EC #ode again$ b&t &se a bad pass2ord this ti#e. 4bserve the deb&g o&tp&t on
R0$ noting that the stat&s is KFAI?L this ti#e.
)ec 26 11+*6+1*.02?+ AAA,A2T34/(21?1919868)+ ="$"'964TPA==
)ec 26 11+*6+1*.02?+ AAA,A2T34/,CO/T (21?1919868)+ ;e"(o%94/A-54
)ec 26 11+*6+1*.039+ AAA,A2T34/(21?1919868)+ p$Aor% incorrec"
6ec 26 144644'03,4 .../.$*3)+<21;,1,-6-=4 Status9>.20
)ec 26 11+*6+1*.039+ AAA,;4;OR<+ free_'er (0:6611-B4*) 'er98/2558
r'er98/2558
por"98""y19*8 re#_$%%r98192.168.3.38 $'"(en_"ype9A=C.. er!ice94/A-54
pri!911 !
rf9 (i%90)
f. Fro# the %elnet 2indo2$ e3it the %elnet session to the ro&ter. %hen try to open a %elnet session to
the ro&ter again$ b&t this ti#e try to log in 2ith the &serna#e Admin:) and a bad pass2ord.
Fro# the console 2indo2$ the deb&g o&tp&t sho&ld loo: si#ilar to the follo2ing.
)ec 26 11+*9+32.339+ AAA,A2T34/,5O6./ (000000AA)+ Pic7 #e"(o% li"
8%ef$'l"8
8hat #essage 2as displayed on the %elnet client screenH GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
%&rn off all deb&gging &sing the undebug all co##and at the privileged E6EC pro#pt.
!art ,: Con"igure Centrai-ed Authentication Using AAA and RADIUS/
In 'art @ of the lab$ yo& install RA.I5S server soft2are on 'C1A. >o& then config&re ro&ter R1 to access the
e3ternal RA.I5S server for &ser a&thentication. %he free2are server 8inRadi&s is &sed for this section of the
lab.
Tas$ ): Restore Router R) to Its *asic Settings
%o avoid conf&sion as to 2hat 2as already entered and the AAA RA.I5S config&ration$ start by restoring
ro&ter R1 to its basic config&ration as perfor#ed in 'arts 1 and 2 of this lab.
Step ): 8rase and reoad the router/
a. Connect to the R1 console$ and log in 2ith the &serna#e Admin:) and pass2ord Admin:)pass.
b. Enter privileged E6EC #ode 2ith the pass2ord cisco)+3,0.
c. Erase the start&p config and then iss&e the reload co##and to restart the ro&ter.
Step +: Restore the basic con"iguration/
a. 8hen the ro&ter restarts$ enter privileged E6EC #ode 2ith the enable co##and$ and then enter
global config #ode. 5se the ;yper%er#inal Trans"er 4 Send Aie f&nction$ c&t and paste or &se
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 1@ of 2(
CCNA Security
another #ethod to load the basic start&p config for R1 that 2as created and saved in 'art 2 of this
lab.
b. %est connectivity by pinging fro# host 'C1A to 'C1C. If the pings are not s&ccessf&l$ tro&bleshoot the
ro&ter and 'C config&rations &ntil they are.
c. If yo& are logged o&t of the console$ log in again as user:) 2ith pass2ord user:)pass$ and access
privileged E6EC #ode 2ith the pass2ord cisco)+3,0.
d. Save the r&nning config to the start&p config &sing the copy run start co##and.
Tas$ +: Do&noad and Insta a RADIUS Server on !C2A
%here are a n&#ber of RA.I5S servers available$ both free2are and for cost. %his lab &ses 8inRadi&s$ a
free2are standards1based RA.I5S server that r&ns on 8indo2s 6' and #ost other 8indo2s operating
syste#s. %he free version of the soft2are can s&pport only five &serna#es.
Step ): Do&noad the BinRadius so"t&are/
a. Create a folder na#ed 8inRadi&s on yo&r des:top or other location in 2hich to store the files.
b. .o2nload the latest version fro# httpB))222.s&ggestsoft.co#)soft)itcons<2""")2inradi&s)$
httpB))2inradi&s.soft02.co#$ httpB))222.brothersoft.co#)2inradi&s12"1@.ht#l.
c. Save the do2nloaded 9ip file in the folder yo& created in Step 1a$ and e3tract the 9ipped files to the
sa#e folder. %here is no installation set&p. %he e3tracted 8inRadi&s.e3e file is e3ec&table.
d. >o& #ay create a shortc&t on yo&r des:top for 8inRadi&s.e3e.
Note: If 8inRadi&s is &sed on a 'C that &ses the Aicrosoft 8indo2s Cista operating syste# or the
Aicrosoft 8indo2s D operating syste#$ 4.MC #ay fail to create s&ccessf&lly beca&se it cannot 2rite to
the registry.
!ossibe soutions:
1. Co#patibility settingsB
a. Right clic: on the 8inRadi&s.e3e icon and select !roperties.
b. 8hile in the !roperties dialog bo3$ select the Compatibiity tab. In this tab$ select the
chec:bo3 for Run this program in compatibiity mode "or. %hen in the drop do2n #en&
belo2$ choose Bindo&s C! <Service !ac$ 3= for e3a#ple$ if it is appropriate for yo&r
syste#.
c. Clic: '@.
2. Run as Administrator settingsB
a. Right clic: on the 8inRadi&s.e3e icon and select !roperties.
b. 8hile in the !roperties dialog bo3$ select the Compatibiity tab. In this tab$ select the
chec:bo3 for Run this program as administrator in the 'rivilege ?evel section.
c. Clic: '@.
0. Run as Administration for each la&nchB
a. Right clic: on the 8inRadi&s.e3e icon and select Run as Administrator.
b. 8hen 8inRadi&s la&nches$ clic: Des in the 5ser Acco&nt Control dialog bo3.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 1( of 2(
CCNA Security
Step +: Con"igure the BinRadius server database/
a. Start the 8inRadi&s.e3e application. 8inRadi&s &ses a local database in 2hich it stores &ser
infor#ation. 8hen the application is started for the first ti#e$ the follo2ing #essages are displayedB
Ple$e go "o C=e""ing,)$"$&$e $n% cre$"e "(e O)-C for yo'r RA).2=
%$"$&$e.
5$'nc( O)-C f$ile%.
b. Choose Settings 4 Database fro# the #ain #en&. %he follo2ing screen is displayed. Clic: the
Con"igure 'D*C Automaticay b&tton and then clic: '@. >o& sho&ld see a #essage that the
4.MC 2as created s&ccessf&lly. E3it 8inRadi&s and restart the application for the changes to ta:e
effect.
c. 8hen 8inRadi&s starts again$ yo& sho&ld see #essages si#ilar to the follo2ing displayed.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 1* of 2(
CCNA Security
d. 4n 2hich ports is 8inRadi&s listening for a&thentication and acco&ntingH
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
Step 3: Con"igure users and pass&ords on the BinRadius server/
Note: %he free version of 8inRadi&s can s&pport only five &serna#es. %he &serna#es are lost if yo& e3it
the application and restart it. Any &serna#es created in previo&s sessions #&st be re1created. ,ote that
the first #essage in the previo&s screen sho2s that 9ero &sers 2ere loaded. ,o &sers had been created
prior to this$ b&t this #essage is displayed each ti#e 8inRadi&s is started$ regardless of 2hether &sers
2ere created or not.
a. Fro# the #ain #en&$ select 'peration 4 Add User.
b. Enter the &serna#e RadUser 2ith a pass2ord of RadUserpass. Re#e#ber that pass2ords are
case1sensitive.
c. Clic: '@. >o& sho&ld see a #essage on the log screen that the &ser 2as added s&ccessf&lly.
Step ,: Cear the og dispay/
Fro# the #ain #en&$ choose Log 4 Cear.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 1D of 2(
CCNA Security
Step 0: Test the ne& user added using the BinRadius test utiity/
a. A 8inRadi&s testing &tility is incl&ded in the do2nloaded 9ip file. ,avigate to the folder 2here yo&
&n9ipped the 8inRadi&s.9ip file and locate the file na#ed Radi&s%est.e3e.
b. Start the Radi&s%est application$ and enter the I' address of this RA.I5S server -12.1*+.1.0/$
&serna#e RadUser$ and pass2ord RadUserpass as sho2n. .o not change the defa< RA.I5S port
n&#ber of 1+10 and the RA.I5S pass2ord of 8inRadi&s.
c. Clic: Send and yo& sho&ld see a Send AccessGRe7&est #essage indicating the server at
12.1*+.1.0$ port n&#ber 1+10$ received @@ he3adeci#al characters. 4n the 8inRadi&s log display$
yo& sho&ld also see a #essage indicating that &ser Rad5ser 2as a&thenticated s&ccessf&lly.
d. Close the Radi&s%est application.
Tas$ 3: Con"igure R) AAA Services and Access the RADIUS Server Using Cisco
I'S
Note: %o config&re AAA &sing CC'$ proceed to %as: (.
Step ): 8nabe AAA on R)/
5se the aaa new-model co##and in global config&ration #ode to enable AAA.
R1(config)# aaa new-model
Step +: Con"igure the de"aut ogin authentication ist/
a. Config&re the list to first &se RA.I5S for the a&thentication service$ and then none. If no RA.I5S
server can be reached and a&thentication cannot be perfor#ed$ the ro&ter globally allo2s access
2itho&t a&thentication. %his is a safeg&ard #eas&re in case the ro&ter starts &p 2itho&t connectivity to
an active RA.I5S server.
R1(config)# aaa authentication login default group radius none
b. >o& co&ld alternatively config&re local a&thentication as the bac:&p a&thentication #ethod instead.
Note: If yo& do not set &p a defa< login a&thentication list$ yo& co&ld get loc:ed o&t of the ro&ter and need to
&se the pass2ord recovery proced&re for yo&r specific ro&ter.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 1+ of 2(
CCNA Security
Step 3: Speci"y a RADIUS server/
5se the radius-ser"er host hostname key key co##and to point to the RA.I5S server. %he
hostname arg&#ent accepts either a host na#e or an I' address. 5se the I' address of the RA.I5S
server$ 'C1A -12.1*+.1.0/. %he :ey is a secret pass2ord shared bet2een the RA.I5S server and the
RA.I5S client -R1 in this case/ and &sed to a&thenticate the connection bet2een the ro&ter and the
server before the &ser a&thentication process ta:es place. %he RA.I5S client #ay be a ,et2or: Access
Server -,AS/$ b&t ro&ter R1 plays that role in this lab. 5se the defa< ,AS secret pass2ord of 8inRadi&s
specified on the RA.I5S server -see %as: 2$ Step (/. Re#e#ber that pass2ords are case1sensitive.
R1(config)# radius-ser"er host 1,2'16-'1'3 key ?in&adius
Tas$ ,: Test the AAA RADIUS Con"iguration
Step ): 1eri"y connectivity bet&een R) and the computer running the RADIUS server/
'ing fro# R1 to 'C1A.
R1# ping 192.168.1.3
If the pings 2ere not s&ccessf&l$ tro&bleshoot the 'C and ro&ter config&ration before contin&ing.
Step +: Test your con"iguration/
a. If yo& restarted the 8inRadi&s server$ yo& #&st re1create the &ser RadUser 2ith a pass2ord of
RadUserpass by choosing 'peration 4 Add User.
b. Clear the log on the 8inRadi&s server by choosing Log 4 Cear fro# the #ain #en&.
c. 4n R1$ e3it to the initial ro&ter screen that displaysB
&1 con0 is now a"ailable/ (ress &)*$&+ to get started.
d. %est yo&r config&ration by logging in to the console on R1 &sing the &serna#e RadUser and the
pass2ord of RadUserpass. 8ere yo& able to gain access to the &ser E6EC pro#pt and$ if so$ 2as
there any delayH GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
e. E3it to the initial ro&ter screen that displaysB
&1 con0 is now a"ailable/ (ress &)*$&+ to get started'
f. %est yo&r config&ration again by logging in to the console on R1 &sing the none3istent &serna#e of
User555 and the pass2ord of User555pass. 8ere yo& able to gain access to the &ser E6EC
pro#ptH 8hy or 2hy notH GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
g. 8ere any #essages displayed on the RA.I5S server log for either loginH GGGGGGG
h. 8hy 2as a none3istent &serna#e able to access the ro&ter and no #essages are displayed on the
RA.I5S server log screenH GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
i. 8hen the RA.I5S server is &navailable$ #essages si#ilar to the follo2ing are typically displayed
after atte#pted logins.
D)ec 26 16+*6+1*.039+ ERA).2=-*-RA).2=_)4A)+ RA).2= er!er
192.168.1.3+16*1>16*6 i no" repon%ing.
D)ec 26 11+*6+1*.039+ ERA).2=-*-RA).2=_A5.F4+ RA).2= er!er
192.168.1.3+16*1>16*6 i &eing #$r7e% $li!e.
Step 3: Troubeshoot router2to2RADIUS server communication/
a. Chec: the defa< Cisco I4S RA.I5S 5.' port n&#bers &sed on R1 2ith the radius-ser"er
host co##and and the Cisco I4S ;elp f&nction.
R1(config)# radius-ser"er host 1,2'16-'1'3 @
acct-port $6( port for &.62$S accounting ser"er <default is 1646=
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 1 of 2(
CCNA Security
$li$ 1-8 $li$e for "(i er!er (#$:. 8)
auth-port $6( port for &.62$S authentication ser"er <default is 164=
O 4&tp&t o#itted P
b. Chec: the R1 r&nning config&ration for lines containing the co##and radius. %he follo2ing
co##and displays all r&nning config lines that incl&de the te3t Kradi&sL.
R1# show run 8 incl radius
$$$ $'"(en"ic$"ion login %ef$'l" gro'p r$%i' none
r$%i'-er!er (o" 192.168.1.3 $'"(-por" 16*1 $cc"-por" 16*6 7ey ?
09?-*?0?2-0*131-141B
O 4&tp&t o#itted P
c. 8hat are the defa< R1 Cisco I4S 5.' port n&#bers for the RA.I5S serverH GGGGGGGGGGGGGGGG
Step ,: Chec$ the de"aut port numbers on the BinRadius server on !C2A/
a. Fro# the 8inRadi&s #ain #en& choose Settings 4 System.
b. 8hat are the defa< 8inRadi&s 5.' port n&#bersH GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
Note: %he early deploy#ent of RA.I5S 2as done &sing 5.' port n&#ber 1*@( for a&thentication and 1*@*
for acco&nting$ 2hich conflicts 2ith the data#etrics service. Meca&se of this conflict$ RFC 2+*( officially
assigned port n&#bers 1+12 and 1+10 for RA.I5S.
Step 0: Change the RADIUS port numbers on R) to match the BinRadius server/
5nless specified other2ise$ the Cisco I4S RA.I5S config&ration defa<s to 5.' port n&#bers 1*@( and
1*@*. Either the ro&ter Cisco I4S port n&#bers #&st be changed to #atch the port n&#ber of the RA.I5S
server or the RA.I5S server port n&#bers #&st be changed to #atch the port n&#bers of the Cisco I4S
ro&ter. In this step$ yo& #odify the I4S port n&#bers to those of the RA.I5S server$ 2hich are specified in
RFC 2+*(.
a. Re#ove the previo&s config&ration &sing the follo2ing co##and.
R1(config)# no radius-ser"er host 1,2'16-'1'3 auth-port 164 acct-port
1646
b. Iss&e the radius-ser"er host co##and again and this ti#e specify port n&#bers 1+12 and
1+10$ along 2ith the I' address and secret :ey for the RA.I5S server.
R1(config)# radius-ser"er host 1,2'16-'1'3 auth-port 1-12 acct-port 1-13
key ?in&adius
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 2" of 2(
CCNA Security
Step 3: Test your con"iguration by ogging into the consoe on R)/
a. E3it to the initial ro&ter screen that displaysB &1 con0 is now a"ailable/ (ress &)*$&+ to
get started.
b. ?og in again 2ith the &serna#e of RadUser and pass2ord of RadUserpass. 8ere yo& able to loginH
8as there any delay this ti#eH
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
c. %he follo2ing #essage sho&ld display on the RA.I5S server log.
2er (R$%2er) $'"(en"ic$"e OG.
d. E3it to the initial ro&ter screen that displaysB &1 con0 is now a"ailable/ (ress &)*$&+ to
get started.
e. ?og in again &sing an invalid &serna#e of User555 and the pass2ord of User555pass. 8ere yo&
able to loginH GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
8hat #essage 2as displayed on the ro&terH _________________________________________
%he follo2ing #essages sho&ld display on the RA.I5S server log.
&eason4 $nknown username
$ser <$ser!!!= authenticate failed
Step 6: Create an authentication method ist "or Tenet and test it/
a. Create a &ni7&e a&thentication #ethod list for %elnet access to the ro&ter. %his does not have the
fallbac: of no a&thentication$ so if there is no access to the RA.I5S server$ %elnet access is disabled.
,a#e the a&thentication #ethod list %E?,E%G?I,ES.
R1(config)# aaa authentication login *)0+)*102+)S group radius
Apply the list to the vty lines on the ro&ter &sing the login a&thentication co##and.
R1(config)# line "ty 0 4
R1(config-line)# login authentication *)0+)*102+)S
%elnet fro# 'C1A to R1$ and log in 2ith the &serna#e RadUser and the pass2ord of RadUserpass.
8ere yo& able to gain access to log inH
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
E3it the %elnet session$ and telnet fro# 'C1A to R1 again. ?og in 2ith the &serna#e User555 and the
pass2ord of User555pass. 8ere yo& able to log inH
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
Tas$ 0: <'ptiona= Con"igure R) AAA Services and Access the RADIUS Server
Using CC!
>o& can also &se CC' to config&re the ro&ter to access the e3ternal RA.I5S server.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 21 of 2(
CCNA Security
Note: If yo& config&red R1 to access the e3ternal RA.I5S server &sing Cisco I4S in %as: 0$ yo& can s:ip this
tas:. If yo& perfor#ed %as: 0 and yo& 2ant to perfor# this tas:$ restore the ro&ter to its basic config&ration as
described %as: 1 of this part$ e3cept log in initially as Rad5ser 2ith the pass2ord Rad5serpass/ If the
RA.I5S server is &navailable at this ti#e$ yo& 2ill still be able to log in to the console.
If yo& do not perfor# this tas:$ read thro&gh the steps to beco#e fa#iliar 2ith the CC' process.
Step ): Impement AAA services and >TT! router access prior to starting CC!/
a. Fro# the C?I global config #ode$ enable a ne2 AAA #odel.
R1(config)# aaa new-model
b. Enable the ;%%' server on R1.
R1(config)# ip http ser"er
c. Add a &ser na#ed admin to the local database.
R1(config)# username admin pri"ilege 1 secret cisco1234
d. ;ave CC' &se the local database to a&thenticate 2eb sessions.
R1(config)# ip http authentication local
Step +: Access CC! and discover R)/
a. Start CC' on 'C1C. In the Aanage .evices 2indo2$ add R1 I' address 12.1*+.1.1 in the first I'
address field. Enter admin in the 5serna#e field$ and cisco)+3,0 in the 'ass2ord field.
b. At the CC' .ashboard$ clic: the Discover b&tton to discover and connect to R0. If discovery fails$
clic: the Discovery Detais b&tton to deter#ine the proble#.
Step 3: Con"igure R) AAA to access the BinRADIUS server/
a. Clic: the Con"igure b&tton at the top of the screen.
b. Choose Router 4 AAA 4 AAA Servers and %roups 4 Servers.
c. In the AAA Servers 2indo2$ clic: Add.
d. In the Add AAA Server 2indo2$ verify that RADIUS is in the Server %ype field.
e. In the Server I' or ;ost field$ enter the I' address of 'C1A$ )9+/)37/)/3.
f. Change the Authori-ation !ort fro# 1*@( to 1+12$ and change the Accounting !ort fro# 1*@* to
1+10 to #atch the RA.I5S server port n&#ber settings.
g. Chec: the Con"igure @ey chec: bo3.
h. Enter BinRadius in both the ,e2 Qey and Confir# Qey fields.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 22 of 2(
CCNA Security
i. In the .eliver Config&ration to Ro&ter 2indo2$ clic: Deiver$ and in the Co##ands .elivery Stat&s
2indo2$ clic: '@.
<. 8hat co##and 2as delivered to the ro&terH
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
Step ,: Con"igure the R) AAA ogin method ist "or RADIUS/
a. Clic: the Con"igure b&tton at the top of the screen.
b. Choose Router 4 AAA 4 Authentication !oicies 4 Login.
c. In the A&thentication ?ogin 2indo2$ clic: Add.
d. In the Select Aethod ?ist-s/ for A&thentication ?ogin 2indo2$ choose group radius and clic: '@.
e. In the Select Aethod ?ist-s/ for A&thentication ?ogin 2indo2$ choose oca as a second #ethod and
clic: '@.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 20 of 2(
CCNA Security
f. In the .eliver Config&ration to Ro&ter 2indo2$ clic: Deiver and in the Co##ands .elivery Stat&s
2indo2$ clic: '@.
g. 8hat co##and-s/ 2ere delivered to the ro&terH
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
Step 0: Test your con"iguration/
a. If yo& restarted the RA.I5S server$ yo& #&st re1create the &ser RadUser 2ith a pass2ord of
RadUserpass by choosing 'peration 4 Add User.
b. Clear the log on the 8inRadi&s server by choosing Log 4 Cear.
c. %est yo&r config&ration by opening a %elnet session fro# 'C1A to R1.
C+> telnet 1,2'16-'1'1
d. At the login pro#pt$ enter the &serna#e RadUser defined on the RA.I5S server and a pass2ord of
RadUserpass.
8ere yo& able to login to R1H GGGGG
Re"ection
1. 8hy 2o&ld an organi9ation 2ant to &se a centrali9ed a&thentication server rather than config&ring
&sers and pass2ords on each individ&al ro&terH
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 2@ of 2(
CCNA Security
2. Contrast local a&thentication and local a&thentication 2ith AAA.
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
0. Mased on the Acade#y online co&rse content$ 2eb research$ and the &se of RA.I5S in this lab$
co#pare and contrast RA.I5S 2ith %ACACS=.
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
GGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGGG
Router Inter"ace Summary Tabe
Router Inter"ace Summary
Ro&ter Aodel Ethernet Interface
R1
Ethernet Interface
R2
Serial Interface
R1
Serial Interface
R2
1+""
Fast Ethernet ")"
-Fa")"/
Fast Ethernet ")1
-Fa")1/
Serial ")")"
-S")")"/
Serial ")")1
-S")")1/
1""
Gigabit Ethernet ")"
-G")"/
Gigabit Ethernet ")1
-G")1/
Serial ")")"
-S")")"/
Serial ")")1
-S")")1/
2+""
Fast Ethernet ")"
-Fa")"/
Fast Ethernet ")1
-Fa")1/
Serial ")")"
-S")")"/
Serial ")")1
-S")")1/
2""
Gigabit Ethernet ")"
-G")"/
Gigabit Ethernet ")1
-G")1/
Serial ")")"
-S")")"/
Serial ")")1
-S")")1/
Note: %o find o&t ho2 the ro&ter is config&red$ loo: at the interfaces to identify the type of ro&ter and
ho2 #any interfaces the ro&ter has. %here is no 2ay to effectively list all the co#binations of
config&rations for each ro&ter class. %his table incl&des identifiers for the possible co#binations of
Ethernet and Serial interfaces in the device. %he table does not incl&de any other type of interface$
even tho&gh a specific ro&ter #ay contain one. An e3a#ple of this #ight be an IS., MRI interface.
%he string in parenthesis is the legal abbreviation that can be &sed in Cisco I4S co##ands to
represent the interface.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 2( of 2(
You might also like
- CompTIA A+ Complete Review Guide: Core 1 Exam 220-1101 and Core 2 Exam 220-1102From EverandCompTIA A+ Complete Review Guide: Core 1 Exam 220-1101 and Core 2 Exam 220-1102Rating: 5 out of 5 stars5/5 (2)
- Cisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3From EverandCisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3No ratings yet
- The Complete Guide to Getting Certified Cisco CCNA 200-301: Complete Your CCNA Exam Training and Preparation with 400 Exam Level Practice QuestionFrom EverandThe Complete Guide to Getting Certified Cisco CCNA 200-301: Complete Your CCNA Exam Training and Preparation with 400 Exam Level Practice QuestionNo ratings yet
- Beginning Arduino Nano 33 IoT: Step-By-Step Internet of Things ProjectsFrom EverandBeginning Arduino Nano 33 IoT: Step-By-Step Internet of Things ProjectsNo ratings yet
- Network with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationFrom EverandNetwork with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationNo ratings yet
- CCNASv1.1 Chp08 Lab A Site2Site VPN InstructorDocument40 pagesCCNASv1.1 Chp08 Lab A Site2Site VPN Instructordotheanhdotramy0% (1)
- Cisco Certified Network AssociateDocument96 pagesCisco Certified Network AssociateMohamed YagoubNo ratings yet
- 1 1 4 6 Lab ConfiguringBasicRouterSettings PDFDocument17 pages1 1 4 6 Lab ConfiguringBasicRouterSettings PDFbi hekNo ratings yet
- Iot Workshop: HF5111B Serial Server Device User ManualDocument58 pagesIot Workshop: HF5111B Serial Server Device User ManualBudhi HermawanNo ratings yet
- 4.4.1.2 Lab - Configuring Zone-Based Policy FirewallsDocument13 pages4.4.1.2 Lab - Configuring Zone-Based Policy FirewallsADEL ANo ratings yet
- 3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUS - InstructorDocument35 pages3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUS - InstructorSalem TrabelsiNo ratings yet
- IP Addressing and Subnetting Workbook - Instructors Version 1.5Document106 pagesIP Addressing and Subnetting Workbook - Instructors Version 1.5Josephat Mutama83% (6)
- Lab - Configuring A Site-to-Site VPN Using Cisco IOS and CCPDocument30 pagesLab - Configuring A Site-to-Site VPN Using Cisco IOS and CCPVasan Suryaßoyzz100% (1)
- CCNASv1 1 Chp08 Lab B RMT Acc VPN Instructor PDFDocument33 pagesCCNASv1 1 Chp08 Lab B RMT Acc VPN Instructor PDFAhmadHijaziNo ratings yet
- DGTL BRKDCN 3040Document103 pagesDGTL BRKDCN 3040cool dude911No ratings yet
- How To Access An AXEDocument20 pagesHow To Access An AXEhuuquan100% (1)
- Ccnasv1.1 Chp03 Lab-A Aaa-Radius StudentDocument25 pagesCcnasv1.1 Chp03 Lab-A Aaa-Radius StudentAngel MendozaNo ratings yet
- CCNASv1.1 Chp10 Lab-A ASA-FW-CLI StudentDocument24 pagesCCNASv1.1 Chp10 Lab-A ASA-FW-CLI StudentLan WanNo ratings yet
- CCNASv1.1 Chp09 Lab-A Sec-Pol StudentDocument32 pagesCCNASv1.1 Chp09 Lab-A Sec-Pol Studentluisdg93No ratings yet
- Ccnasv1.1 Chp10 Lab-F Asa5510-Fw-Asdm InstructorDocument54 pagesCcnasv1.1 Chp10 Lab-F Asa5510-Fw-Asdm Instructormyropie100% (1)
- CCNA Guide To Networking - Ch6 - Quiz SolutionsDocument5 pagesCCNA Guide To Networking - Ch6 - Quiz SolutionsNickHenryNo ratings yet
- Lab 5.3.7 Configuring DHCP With SDM and The Cisco IOS CLIDocument15 pagesLab 5.3.7 Configuring DHCP With SDM and The Cisco IOS CLIArba SudiatmikaNo ratings yet
- Lab 1 Configuring Basic Routing and SwitchingDocument12 pagesLab 1 Configuring Basic Routing and SwitchingratihwidyastutiNo ratings yet
- CCNA Security: Configuring Devices For Use With Cisco Configuration Professional (CCP) 2.5Document8 pagesCCNA Security: Configuring Devices For Use With Cisco Configuration Professional (CCP) 2.5vmtm7No ratings yet
- Semester 1 Linux Server 7.1 Installation ManualDocument5 pagesSemester 1 Linux Server 7.1 Installation ManualanimationeasyNo ratings yet
- EWAN Lab 3 5 2 InstructorDocument5 pagesEWAN Lab 3 5 2 InstructorDario PazNo ratings yet
- Configuring Zone Based Policy FirewallsDocument13 pagesConfiguring Zone Based Policy FirewallsNorman Pal-og Madongit17% (6)
- EWAN Lab 2 5 3 InstructorDocument10 pagesEWAN Lab 2 5 3 InstructorshouldofduckedNo ratings yet
- 3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUSDocument21 pages3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUSOsman SepulvedaNo ratings yet
- Chapter 4 Lab 4-2, Mixed Layer 2-3 Connectivity Chapter 4 Lab 4-2, Mixed Layer 2-3 ConnectivityDocument13 pagesChapter 4 Lab 4-2, Mixed Layer 2-3 Connectivity Chapter 4 Lab 4-2, Mixed Layer 2-3 ConnectivityKarina Herrera YzaguirreNo ratings yet
- Take Assessment - ENetwork Final Exam - CCNA Exploration: Network Fundamentals (Version 4.0Document20 pagesTake Assessment - ENetwork Final Exam - CCNA Exploration: Network Fundamentals (Version 4.0Raphael AlmeidaNo ratings yet
- 3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUSDocument21 pages3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUSPauloNo ratings yet
- Cisco ISO and Boot Process PDFDocument10 pagesCisco ISO and Boot Process PDFsystems_sgNo ratings yet
- AUG-035-0-EN - (Remote Access For Allen Bradley PLCS)Document45 pagesAUG-035-0-EN - (Remote Access For Allen Bradley PLCS)QuantumAutomationNo ratings yet
- Install Windows MSI packages for MariaDB databaseDocument7 pagesInstall Windows MSI packages for MariaDB databaseJDNo ratings yet
- Idoc - Tips Soal MikrotikDocument10 pagesIdoc - Tips Soal MikrotikBack HeheNo ratings yet
- 3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUS - InstructorDocument27 pages3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUS - InstructorAlexander Lapo Cordova0% (1)
- 3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUS PDFDocument20 pages3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUS PDFLizSocaZevallos100% (1)
- Connecting Networks Chapter 9 v5.0 Exam Answers 2014Document6 pagesConnecting Networks Chapter 9 v5.0 Exam Answers 2014adrian743842No ratings yet
- CCNA 4 Chapter 9 v5 Exam Answers 2013Document6 pagesCCNA 4 Chapter 9 v5 Exam Answers 2013adrian743842No ratings yet
- DRSEnt PT Practice SBA OSPF PDFDocument5 pagesDRSEnt PT Practice SBA OSPF PDFHarol Matias RamosNo ratings yet
- Lab A, Securing Administrative Access Using AAA and RADIUS: TopologyDocument13 pagesLab A, Securing Administrative Access Using AAA and RADIUS: TopologyGary Giovanni Cabezas GutierrezNo ratings yet
- HACMP 6 Clustering Configuration Step by StepDocument18 pagesHACMP 6 Clustering Configuration Step by StepdarkmountaincloudNo ratings yet
- Ewan Ptact 5 2 8Document6 pagesEwan Ptact 5 2 8Muhammad HudzaifahNo ratings yet
- Aircrack Wpa EncwapDocument10 pagesAircrack Wpa EncwapLuis Felipe Figueroa MoraNo ratings yet
- 4.4.1.2 Lab - Configuring Zone-Based Policy FirewallsDocument15 pages4.4.1.2 Lab - Configuring Zone-Based Policy FirewallselizaNo ratings yet
- Lab 10.6.1: Creating A Small Lab TopologyDocument9 pagesLab 10.6.1: Creating A Small Lab TopologyAnnysa FirdausNo ratings yet
- Configure IPv4 Static and Default Routes - ILMDocument7 pagesConfigure IPv4 Static and Default Routes - ILMAbdullahNo ratings yet
- D09IntrodToSerComs 28augDocument5 pagesD09IntrodToSerComs 28augP_leeNo ratings yet
- 1.1.4.6 Lab - Configuring Basic Router Settings With IOS CLIDocument15 pages1.1.4.6 Lab - Configuring Basic Router Settings With IOS CLIJuan S. MorejónNo ratings yet
- 1-1-4-6-Lab-Configuring-Basic-Router-Settings-With-Ios-Cli - PDF EditedDocument10 pages1-1-4-6-Lab-Configuring-Basic-Router-Settings-With-Ios-Cli - PDF EditedYeab SraNo ratings yet
- 4.4.1.2 Lab - Configuring Zone-Based Policy Firewalls-ALDO PUGLIESEDocument21 pages4.4.1.2 Lab - Configuring Zone-Based Policy Firewalls-ALDO PUGLIESEsheckie jarabaNo ratings yet
- Net Flow TechDocument245 pagesNet Flow TechAbhishek GhoshNo ratings yet
- Accessing The WAN Student Skills Based Assessment Lab Answer KeyDocument9 pagesAccessing The WAN Student Skills Based Assessment Lab Answer KeyRadmilo Milojković75% (4)
- Configure Basic Router Settings LabDocument11 pagesConfigure Basic Router Settings Labumang patnaikNo ratings yet
- La causa más probable es que el host 1 y el host 2 se encuentran en redes diferentes (opción b). Para que dos hosts en una LAN puedan comunicarse, deben estar en la misma subredDocument139 pagesLa causa más probable es que el host 1 y el host 2 se encuentran en redes diferentes (opción b). Para que dos hosts en una LAN puedan comunicarse, deben estar en la misma subredMauricio SalazarNo ratings yet
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkFrom EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNo ratings yet
- WAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksFrom EverandWAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksNo ratings yet
- Introducing .NET for Apache Spark: Distributed Processing for Massive DatasetsFrom EverandIntroducing .NET for Apache Spark: Distributed Processing for Massive DatasetsNo ratings yet
- Cisco Packet Tracer Implementation: Building and Configuring Networks: 1, #1From EverandCisco Packet Tracer Implementation: Building and Configuring Networks: 1, #1No ratings yet
- Wisenet - SPE110 Video Network EncoderDocument3 pagesWisenet - SPE110 Video Network Encoderforat 64079No ratings yet
- Distance Vector Routing ExampleDocument24 pagesDistance Vector Routing ExampleAbhiram SayaniNo ratings yet
- CCNA QuestionsDocument29 pagesCCNA QuestionsfelipemunozmoraNo ratings yet
- A10 Points To Remember Before Operating The Load BalancerDocument13 pagesA10 Points To Remember Before Operating The Load Balancersanju_81No ratings yet
- IJERT Paper TemplateDocument4 pagesIJERT Paper TemplateNikhil PSNo ratings yet
- Traffic Engineering in Software Defined Networking SDNDocument4 pagesTraffic Engineering in Software Defined Networking SDNEditor IJTSRDNo ratings yet
- AL100 - Embedded Blue®: Industrial Gigabit Ethernet SwitchDocument14 pagesAL100 - Embedded Blue®: Industrial Gigabit Ethernet SwitchMihail AvramovNo ratings yet
- Chillnz CCNA CheatsheetDocument2 pagesChillnz CCNA CheatsheetSpeed ConnectNo ratings yet
- CSSE280: Introduction to Web Programming</titleDocument30 pagesCSSE280: Introduction to Web Programming</titleGamal BohoutaNo ratings yet
- What Is CSFB and SRVCC in LteDocument40 pagesWhat Is CSFB and SRVCC in LteRenugopal NarayananNo ratings yet
- BSCI Lecture 3Document38 pagesBSCI Lecture 3Vishal AvhadNo ratings yet
- Csen 503 Application Layer I: Amr El Mougy Rania Said Lamia AlbadrawyDocument35 pagesCsen 503 Application Layer I: Amr El Mougy Rania Said Lamia Albadrawybb2323bNo ratings yet
- NSX 64 AdminDocument456 pagesNSX 64 AdminBarnabás JanovszkiNo ratings yet
- 5 - ITN - Module - 5Document33 pages5 - ITN - Module - 5farkhanterakhirNo ratings yet
- Useful FirewallD Rules to Configure and Manage Linux FirewallDocument10 pagesUseful FirewallD Rules to Configure and Manage Linux Firewalldanxl007No ratings yet
- 8.1.1.8 Packet Tracer - Troubleshooting Challenge - Documenting The Network InstructionsDocument5 pages8.1.1.8 Packet Tracer - Troubleshooting Challenge - Documenting The Network Instructionsiqbal pandu0% (1)
- Fusion Payment and Positive Pay File Transmission Using SFTP PUT ProtocolDocument10 pagesFusion Payment and Positive Pay File Transmission Using SFTP PUT Protocolsudhirpatil15No ratings yet
- OS9000 DatasheetDocument8 pagesOS9000 Datasheetpepa bemeNo ratings yet
- (English (Auto-Generated) ) Azure Master Class Part 6 - Networking (DownSub - Com)Document18 pages(English (Auto-Generated) ) Azure Master Class Part 6 - Networking (DownSub - Com)amirNo ratings yet
- PT Activity 1.3.1: Review of Concepts From Exploration 1: Topology DiagramDocument4 pagesPT Activity 1.3.1: Review of Concepts From Exploration 1: Topology Diagrammagma871385No ratings yet
- Customer Presentation AZFW and AZFM NDADocument27 pagesCustomer Presentation AZFW and AZFM NDAtarunsood2009No ratings yet
- YugugDocument2 pagesYugugperea torresNo ratings yet
- IP-SM-GW Transport - How SMS is Sent over IP in VoLTE NetworksDocument12 pagesIP-SM-GW Transport - How SMS is Sent over IP in VoLTE Networksabhijit010379No ratings yet
- VRRP for redundant network servicesDocument11 pagesVRRP for redundant network servicesLuis Gonzalez AlarconNo ratings yet
- Sybex CCNA 640-802 Chapter 02Document21 pagesSybex CCNA 640-802 Chapter 02xkerberosxNo ratings yet
- Segment Routing Basic Igp (Ospf) : Lab TopologyDocument10 pagesSegment Routing Basic Igp (Ospf) : Lab TopologyapammmmmNo ratings yet