Professional Documents
Culture Documents
Stunnel Guide
Uploaded by
Corey LaliberteCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Stunnel Guide
Uploaded by
Corey LaliberteCopyright:
Available Formats
Using Stunnel with TestCaddy
Contents
Introduction ............................................................................................................................................... 1
Configuring Stunnel to use with TestCaddy
Server configuration.................................................................................................................................. 2
Client configuration ................................................................................................................................. 3
Creating self-signed certificate ............................................................................................................. 4
Running Stunnel ...................................................................................................................................... 5
Configuring Firewall for TestCaddy/Stunnel Access ...................................................................... 6
Setting a static TCP/IP port for SQL Server .................................................................................... 7
Running TestCaddy with Stunnel ....................................................................................................... 8
References ................................................................................................................................................ 9
2009 Tamihai Ltd
Introduction
The following is an extract from the Stunnel official website: (www.stunnel.org)
Stunnel is a program that allows you to encrypt arbitrary TCP connections inside SSL (Secure Sockets
Layer) available on both Unix and Windows. Stunnel can allow you to secure non-SSL aware daemons
and protocols (like POP, IMAP, LDAP, etc) by having Stunnel provide the encryption, requiring no
changes to the daemon's code.
Using Stunnel in conjunction with TestCaddy enables a secure point-to-point connection to a remote SQL
Server over the internet. To do this, the following are required:
1. An instance of Stunnel must be installed on the server machine (where SQL Server is located)
2. An instance of Stunnel must be installed on the client machine (where TestCaddy is located or going
to be installed once Stunnel is installed)
3. An SSL certificate for Stunnel to use, to ensure a secure connection
4. SQL Server must have a static port set.
To download Stunnel, please go to http://www.stunnel.org/download/
A simplified diagram of using Stunnel with TestCaddy
2009 Tamihai Ltd 1
Configuring Stunnel to use with TestCaddy
Server configuration
Download and install Stunnel on the machine where SQL Server is located.
Before running Stunnel, it must be configured to enable a secure connection. This can be done by
editing the stunnel.conf file located in the Stunnel installation folder.
To modify, open stunnel.conf using Notepad, or your favourite text editor. If the lines mentioned below
do not exist, add them, or otherwise change the existing lines.
Note: If any of the lines mentioned below begin with the ; character in the stunnel.conf file then they are
comments which will not take effect, so the ; character at the beginning of the line must be removed.
1. Specify the certificate and files for Stunnel to use.
cert = host.pem
key = host.key
Where host.pem and host.key are certificate files (see below for details)
2. Specify authentication level. Setting it to 3 enforces the highest level of security.
; Authentication stuff
verify = 3
3. Specify certificate file
; It's often easier to use CAfile
CAfile = host.cert
4. Add the following. This is telling Stunnel to listen on the local port 1956, and forward to the local
port 1955.
[sql]
;listen on port 1956
accept = 1956
; forward to port 1955 (this is the static port of the SQL Server)
connect = localhost:1955
5. Save and Exit.
Note: If you are only using Stunnel with TestCaddy, please make sure all the other lines begin with ;
with the exception of the following two lines:
socket = l:TCP_NODELAY=1
socket = r:TCP_NODELAY=1
2009 Tamihai Ltd 2
Client configuration
Download and install Stunnel on the machine where TestCaddy is located.
Before running Stunnel, it must be configured to enable a secure connection. This can be done by
editing the stunnel.conf file located in the Stunnel installation folder.
To modify, open stunnel.conf using Notepad, or your favourite text editor. If the lines mentioned below
do not exist, add them, or otherwise change the existing lines.
Note: If any of the lines mentioned below begin with the ; character in the stunnel.conf file then they are
comments which will not take effect, so the ; character at the beginning of the line must be removed.
1. Specify the certificate and files for Stunnel to use.
cert = host.pem
key = host.key
Where host.pem and host.key are certificate files (see below for details)
2. Specify authentication level. Setting it to 3 enforces the highest level of security.
; Authentication stuff
verify = 3
3. Specify certificate file
; It's often easier to use CAfile
CAfile = host.cert
4. Tell Stunnel that you are the client
; Use it for client mode
client = yes
5. Add the following. This is telling Stunnel to listen on the local port 1956, and forward to the specified
IP address at the specified port. NOTE: You should specify the external IP address of the network
where your SQL server is located.
[sql]
;listen on port 1956
accept = 1956
; forward to ip:port (this is the address of the Stunnel at the server machine)
connect = 1.2.3.4:1956
6. Save and Exit.
Note: If you are only using Stunnel with TestCaddy, please make sure all the other lines begin with ;
with the exception of the following two lines:
socket = l:TCP_NODELAY=1
socket = r:TCP_NODELAY=1
2009 Tamihai Ltd 3
SSL Certificate
A SSL certificate must be used with Stunnel to ensure a secure connection between TestCaddy and SQL
Server. In addition to identification, your certificate is also used for encrypting the information travelling
over the internet.
You can use your own certificate if you have one; alternatively you can create a self-signed certificate.
Creating self-signed certificate
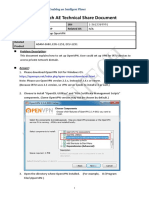
To start with, you'll need OpenSSL. Download the recommended version from the OpenSSL site
(http://www.openssl.org/), and extract it to a desired location (here we use C:\OpenSSL as an example).
Note: We are not recommending an OpenSSL version as they change frequently. The process should be
the same regardless of the version you use.
1. Open command prompt.
Start > Programs > Accessories > Command Prompt
2. Navigate to the OpenSSL folder. For our example, we would type
cd c:\openssl
The dos prompt (beginning of the line) should now read C:\ OpenSSL>
3. Next, were going to generate the key.
openssl genrsa 1024 > host.key
4. Next, were going to generate the certificate.
openssl req -new -x509 -nodes -sha1 -days 365 -key host.key > host.cert
Note: Here, we are making the certificate expire in 365 days. The shorter you make the expiry time,
the safer it is, though this process must be repeated every time a certificate expires.
5. At this stage, you will be asked to fill out the certificates X.509 attributes. The answers should be
adjusted for the location. Note: When the certificate is going to be used in a peer to peer situation
(as in this case), it does not really matter what information is in the certificate. Some minimal
information should be supplied as in the following example.
Country Name (2 letter code) [AU]:NZ
State or Province Name (full name) [Some-State]:Auckland
Locality Name (eg, city) []:Auckland
Organization Name (eg, company) [Internet Widgits Pty Ltd]:TamihaiLtd
Organizational Unit Name (eg, section) []:
Common Name (eg, YOUR name) []:mail.yourdomain.org
Email Address []:postmaster@yourdomain.org
6. Next, were going to combine Key and Certificate files into host.pem.
copy host.cert+host.key host.pem
2009 Tamihai Ltd 4
You should now have three files (host.cert, host.key, host.pem) in C:\OpenSSL. These files need to be
placed in the Stunnel folder on both the client and server machine, as earlier they were specified in the
client and server config files.
Important notes about key and pem files
The data in the host.key and key.pem file must be protected, as anyone possessing the private key can read
any data encrypted with this key! Do not give these files to anyone, except to clients that need to
connect to the remote SQL Server.
Running Stunnel
Once Stunnel has been configured, the Stunnel service needs to be installed, and then Stunnel run. This
needs to be done on both the Client and Server machines.
1. To install Stunnel service:
Start > Programs > Stunnel > Service install
2. To run Stunnel service:
Start > Programs > Stunnel > Service Start
2009 Tamihai Ltd 5
Configuring Firewall for TestCaddy/Stunnel Access
A firewall can be used to restrict access to your network by forwarding only requests targeted at specific
TCP/IP addresses in the local network. Requests for all other network addresses are blocked by the
firewall.
Your IT administrator must configure the firewall which protects the network/office. A pinhole
(port forwarding) must be added to the firewall, to forward incoming requests to the server box. For our
example, open incoming port 1956, and forward to the server box on port 1956.
If you are running Windows Firewall on the SQL Server box itself, then you must also pinhole through
the Windows Firewall.
Configuring Windows Firewall
To open a port in the Windows Firewall for TestCaddy to access the remote SQL Server
1. In Control Panel, open Windows Firewall.
2. In Windows Firewall dialog box, click the Exceptions tab, and then click Add Port.
3. In the Add a Port dialog box, in the Name text box, type Stunnel/SQL
4. In the Port number text box, type the port number that Stunnel is listening on
E.g. 1965 for our example
5. Verify that TCP is selected, and then click OK.
2009 Tamihai Ltd 6
Setting a static TCP/IP port for SQL Server
You need to configure SQL server to listen on a static TCP/IP port, i.e. one which does not change when
the server restarts.
Note: Here, we mention SQL Server 2005; however the same steps apply for SQL Server 2008
To assign a TCP/IP port number to the SQL Server Database Engine
1. Open SQL Server Configuration Manager, located in Start > Programs > Microsoft SQL Server 2005 >
Configuration Tools > SQL Server Configuration Manager
2. In SQL Server Configuration Manager, in the console pane, expand SQL Server 2005 Network
Configuration, expand Protocols for <instance name>, and then double-click TCP/IP.
3. In the TCP/IP Properties dialog box, on the IP Addresses tab, several IP addresses appear, in the
format IP1, IP2, up to IPAll. E.g. one of these is for the IP address of the loopback adapter, 127.0.0.1.
4. In the IPAll Properties area box, in the TCP Port box, type the port number you wish this IP address
to listen on (e.g. 1955 for our example), and then click OK.
5. In the console pane, click SQL Server 2005 Services.
6. In the details pane, right-click SQL Server (<instance name>) and then click restart, to stop and
restart SQL Server.
NOTE: After the SQL Server has restarted, any client applications which connect to this SQL server
should specify the server using the port number after a comma rather than specifying the instance name,
e.g.
127.0.0.1\TestCaddy
Becomes
127.0.0.1,1955
2009 Tamihai Ltd 7
Running TestCaddy with Stunnel
To connect TestCaddy to the remote SQL Server using Stunnel, you must point TestCaddy to the
specified local port.
Firstly, Stunnel must be running both on client and server machines (see previous section).
If you have not yet installed TestCaddy or you have installed it but not yet run the Configuration Wizard,
then go ahead and install TestCaddy on the client machine and run it from the Start menu, which will start
the Configuration Wizard:
1. During the TestCaddy Configuration Wizard, at the SQL Instance Details screen, set:
SQL Server: localhost,1956
Else, if you want to setup TestCaddy with Stunnel after you have installed TestCaddy:
1. Run TestCaddy
2. Go to TestCaddy Database Manager
File > Database Manager
3. At the TestCaddy Database Manager screen, change the database details
Click Change
4. At the SQL Database Connection Details screen, set:
SQL Server: localhost,1956
5. Save.
6. The list of TestCaddy databases on the SQL Server should show in the Database Manager list of
databases.
7. Close the TestCaddy Database Manager screen, and then you will be prompted to select a product
database.
8. Select the product database that you want to use, click OK, and continue to use TestCaddy as usual.
2009 Tamihai Ltd 8
References
Please read legal considerations for Stunnel as presented at
http://www.stunnel.org/about/legalese.html
We would like to recognise all those that have contributed to Stunnel as displayed at
www.stunnel.org/about/credits.html
Please read legal considerations for OpenSSL as presented at http://www.openssl.org/about/
We would like to recognise all those that have contributed to the OpenSSL Project, as displayed at
http://www.openssl.org/about/
2009 Tamihai Ltd 9
You might also like
- Hiding Web Traffic with SSH: How to Protect Your Internet Privacy against Corporate Firewall or Insecure WirelessFrom EverandHiding Web Traffic with SSH: How to Protect Your Internet Privacy against Corporate Firewall or Insecure WirelessNo ratings yet
- Connect SSL Guide PDFDocument17 pagesConnect SSL Guide PDFshaahin13631363No ratings yet
- 6.9. How To Send SSL-Encrypted EmailDocument3 pages6.9. How To Send SSL-Encrypted EmailJoxNo ratings yet
- MailCleaner InstallationDocument14 pagesMailCleaner InstallationcolregNo ratings yet
- A Guide On How To Setup An Apache Virtual-Host Using A Self-Signed CertificateDocument7 pagesA Guide On How To Setup An Apache Virtual-Host Using A Self-Signed CertificateΟρεστης ΝαλμπαντηςNo ratings yet
- Splunk Enterprise Security - Advanced SplunkDocument8 pagesSplunk Enterprise Security - Advanced SplunkRajeev GhoshNo ratings yet
- Secure Splunk Enterprise DeploymentDocument8 pagesSecure Splunk Enterprise DeploymentRajeev Ghosh100% (1)
- Konfigurasi OpenVPN Pada MikrotikDocument51 pagesKonfigurasi OpenVPN Pada MikrotiknuNo ratings yet
- Basic Configuration OPENVPNDocument33 pagesBasic Configuration OPENVPNFabricio FerreiraNo ratings yet
- Setting Up OpenVPN Server On Centos 7Document13 pagesSetting Up OpenVPN Server On Centos 7Abu FadilahNo ratings yet
- Faq Tomcat Soap SSLDocument9 pagesFaq Tomcat Soap SSLhelixneuNo ratings yet
- SMU Online Exams Aug 2011 Delivery ProcessDocument28 pagesSMU Online Exams Aug 2011 Delivery ProcessAbid HussainNo ratings yet
- Intact Technology Definitive SSL Tso GuideDocument20 pagesIntact Technology Definitive SSL Tso GuideHoly Wayne 'Trinity' ChuaNo ratings yet
- ESP8266 AT Command Examples: Espressif Systems IOT TeamDocument14 pagesESP8266 AT Command Examples: Espressif Systems IOT TeamMikeViveNo ratings yet
- Plesk 10 Pci Compliance GuideDocument10 pagesPlesk 10 Pci Compliance GuideJack JillNo ratings yet
- Creating Hbase Cluster and Replication On AwsDocument30 pagesCreating Hbase Cluster and Replication On AwspinkpantherpremNo ratings yet
- Quick Start Install Guide For Hyperstore Aws-Mms v6.0.4Document14 pagesQuick Start Install Guide For Hyperstore Aws-Mms v6.0.4EL MELHANo ratings yet
- Veritas Install AdminDocument28 pagesVeritas Install AdminsanjayNo ratings yet
- Siemonster v4 Demo Build Guide v12Document14 pagesSiemonster v4 Demo Build Guide v12Amine NedjadiNo ratings yet
- Install SSL Certificate on CentOS ApacheDocument11 pagesInstall SSL Certificate on CentOS ApacheMawonsosungueNo ratings yet
- How To Configure Tls With Sip Proxy: Barracuda Cloudgen FirewallDocument10 pagesHow To Configure Tls With Sip Proxy: Barracuda Cloudgen FirewallHari NarayananNo ratings yet
- ESA Wildcard CA Usage TemplateDocument3 pagesESA Wildcard CA Usage TemplateAnonymous cs4BLczENo ratings yet
- SSL Apache HowtoDocument10 pagesSSL Apache HowtonmlgomesNo ratings yet
- Test Lab Guide: Deploying An AD CS Two-Tier PKI HierarchyDocument22 pagesTest Lab Guide: Deploying An AD CS Two-Tier PKI HierarchyAkram AlqadasiNo ratings yet
- Nw4install DHCPDocument10 pagesNw4install DHCPnitrorubyNo ratings yet
- SW 6 10 Creating and Installing SSL Certificates DV 1 0Document11 pagesSW 6 10 Creating and Installing SSL Certificates DV 1 0Dzmitry KuzmiankouNo ratings yet
- Itnsa Pra WSMB2023Document10 pagesItnsa Pra WSMB2023hazwanNo ratings yet
- How To Set Up Nginx Reverse Proxy With Let's EncryptDocument12 pagesHow To Set Up Nginx Reverse Proxy With Let's EncryptJosé Arturo García100% (1)
- Installing Virl On Vmware Player Workstation FusionDocument4 pagesInstalling Virl On Vmware Player Workstation FusionEric ZhangNo ratings yet
- How to set up OpenVPN in 15 stepsDocument7 pagesHow to set up OpenVPN in 15 stepsNguyễn Văn TânNo ratings yet
- SM9.30 TSO LWSSO Configuring Guide PDFDocument14 pagesSM9.30 TSO LWSSO Configuring Guide PDFhanspaulNo ratings yet
- Nginx Web Server Security Hardening GuideDocument12 pagesNginx Web Server Security Hardening Guidescrib_nokNo ratings yet
- Quickstart 0.10.2Document6 pagesQuickstart 0.10.2Nenad MileticNo ratings yet
- 0620-Configure Secure Communication To Oracle From PowerCenter-H2LDocument5 pages0620-Configure Secure Communication To Oracle From PowerCenter-H2Lrsreddy434No ratings yet
- NetSentinel Security ServerDocument9 pagesNetSentinel Security ServerKiran DasNo ratings yet
- Everything You Should Know About SQUID Proxy On RHEL5/CentOS - Part 1Document5 pagesEverything You Should Know About SQUID Proxy On RHEL5/CentOS - Part 1Hale BweetyNo ratings yet
- How to Set Up an OpenVPN Server on MikroTik Router for Secure VPN ConnectionsDocument12 pagesHow to Set Up an OpenVPN Server on MikroTik Router for Secure VPN Connectionshhhhh123450% (1)
- Checklist Installation ServicesDocument8 pagesChecklist Installation ServicesMinhNo ratings yet
- Kepware Plus Uag GuideDocument9 pagesKepware Plus Uag GuideElbari OmarNo ratings yet
- An Introduction To Openssl Programming (Par T I)Document13 pagesAn Introduction To Openssl Programming (Par T I)Marvin LopezNo ratings yet
- Generating A Certificate Signing Request (CSR) : CertificatesDocument4 pagesGenerating A Certificate Signing Request (CSR) : CertificatesmohamedNo ratings yet
- How To Set Up Free SSL Certificates From Let's Encrypt Using Docker and Nginx PDFDocument38 pagesHow To Set Up Free SSL Certificates From Let's Encrypt Using Docker and Nginx PDFJosé Arturo García100% (1)
- Generating SSL CertificateDocument8 pagesGenerating SSL Certificatelrc3No ratings yet
- Centos 6 Easy OpenVPN 1.2 Install GuideDocument11 pagesCentos 6 Easy OpenVPN 1.2 Install Guideworld1capitalNo ratings yet
- Pki OpensslDocument11 pagesPki OpensslgdeepthiNo ratings yet
- Installing Signalware 9Document56 pagesInstalling Signalware 9nshivegowdaNo ratings yet
- Instructions: Set Up The Firewall For Future SuccessDocument5 pagesInstructions: Set Up The Firewall For Future SuccessdoctorinsaneNo ratings yet
- Configuring The Basic System Environment: Huawei Quidway S5700 How-ToDocument8 pagesConfiguring The Basic System Environment: Huawei Quidway S5700 How-ToRajkumar LodhNo ratings yet
- Oracle Audit Vault Installation ManualDocument14 pagesOracle Audit Vault Installation ManualKagiso MojalemothoNo ratings yet
- Checklist Installation ServicesDocument8 pagesChecklist Installation Servicesx008No ratings yet
- Upgrading Dell Networking N1100-ON Series Switches To Version 6.8.1.2Document11 pagesUpgrading Dell Networking N1100-ON Series Switches To Version 6.8.1.2rudiansyah.ar313No ratings yet
- Installing An SSL Certificate On AlmaLinux9 Running NginxDocument10 pagesInstalling An SSL Certificate On AlmaLinux9 Running NginxPanem NagabhushanamNo ratings yet
- CBIS OverCloud Deploy MOPDocument37 pagesCBIS OverCloud Deploy MOPBABA ROSHAN0% (1)
- Installing An SSL Certificate On AlmaLinux9 Running NginxDocument10 pagesInstalling An SSL Certificate On AlmaLinux9 Running NginxStereNo ratings yet
- Install Squid WindowsDocument19 pagesInstall Squid WindowsNguyễn Quốc HuyNo ratings yet
- Troubleshoot Security Intelligence Feed Update Failures On The FireSIGHT Management CenterDocument5 pagesTroubleshoot Security Intelligence Feed Update Failures On The FireSIGHT Management CenterWafikNo ratings yet
- How to Set Up a Multi-Node Hadoop Cluster on AWS EC2Document42 pagesHow to Set Up a Multi-Node Hadoop Cluster on AWS EC2Sampath Kumar PolisettyNo ratings yet
- Guide - Part1 - Apache Hadoop Installation and Cluster Setup On AWS EC2 (Ubuntu) PDFDocument23 pagesGuide - Part1 - Apache Hadoop Installation and Cluster Setup On AWS EC2 (Ubuntu) PDFjosephNo ratings yet
- Supply and Installation of SSL Certificate For Central Statistics Agency (Csa) As-Built DocumentDocument14 pagesSupply and Installation of SSL Certificate For Central Statistics Agency (Csa) As-Built DocumentAhmedin abukiaNo ratings yet
- Performance Tuning Network Stack Mac OS XDocument14 pagesPerformance Tuning Network Stack Mac OS XCorey LaliberteNo ratings yet
- Designing An IBM Storage Area Network PDFDocument310 pagesDesigning An IBM Storage Area Network PDFCorey LaliberteNo ratings yet
- The Guerrilla and How To Fight HimDocument320 pagesThe Guerrilla and How To Fight HimCorey LaliberteNo ratings yet
- The Psychopaths BibleDocument210 pagesThe Psychopaths BibleKenya Coviak90% (20)
- To The Honorable Brother MahmudDocument4 pagesTo The Honorable Brother MahmudCorey LaliberteNo ratings yet
- UAMS Cassidy Maximizing Brain PerformanceDocument41 pagesUAMS Cassidy Maximizing Brain PerformanceCorey LaliberteNo ratings yet
- What Is CIDR?Document2 pagesWhat Is CIDR?Akhilesh KumarNo ratings yet
- Fortigate 7000 60 PDFDocument116 pagesFortigate 7000 60 PDFSuryo AjieNo ratings yet
- Subscriber Data Usage-2018!04!12Document6 pagesSubscriber Data Usage-2018!04!12Andrew NkhuwaNo ratings yet
- S10 Interface Config Mme 00Document9 pagesS10 Interface Config Mme 00Prakul AsthanaNo ratings yet
- Unit 1. Lesson 5. Static Vs Dynamic Routing, ProtocolsDocument9 pagesUnit 1. Lesson 5. Static Vs Dynamic Routing, ProtocolsМакс КальмусNo ratings yet
- Module1 - Scalable Network DesignDocument26 pagesModule1 - Scalable Network DesignGerryNo ratings yet
- PRON NA60-MB0 Modbus User GuideDocument59 pagesPRON NA60-MB0 Modbus User GuidePrje AccNo ratings yet
- CCNA Service Provider 1 Course OutlineDocument3 pagesCCNA Service Provider 1 Course OutlineneonetwirelessNo ratings yet
- SIP Trunking Turnup GuideDocument8 pagesSIP Trunking Turnup Guideashok7No ratings yet
- Chapter3 IP ConnectivityDocument6 pagesChapter3 IP ConnectivityGilgamesh berserkerNo ratings yet
- Chapter 6-State ManagementDocument79 pagesChapter 6-State ManagementHeng PhinNo ratings yet
- 1Document33 pages1Gargee HandiqueNo ratings yet
- Customer Presentation AZFW and AZFM NDADocument27 pagesCustomer Presentation AZFW and AZFM NDAtarunsood2009No ratings yet
- DS 2CD2620F IsDocument3 pagesDS 2CD2620F IsMarceloPerezCarrascoNo ratings yet
- Stream Control Transmission Protocol (SCTP) : Robust and Efficient For Data Centre ApplicationsDocument5 pagesStream Control Transmission Protocol (SCTP) : Robust and Efficient For Data Centre ApplicationsIJEECSNo ratings yet
- Broadworks IMS Solution Guide R-190Document77 pagesBroadworks IMS Solution Guide R-190Shriraj07No ratings yet
- Ethical Hacking Guide - Why Conduct Ethical Hacking TestsDocument21 pagesEthical Hacking Guide - Why Conduct Ethical Hacking TestsAnil Kumar50% (2)
- Alcatel Lucent Configuration GuideDocument30 pagesAlcatel Lucent Configuration Guidejh100% (14)
- Configurar VPN ASA PIX CiscoDocument23 pagesConfigurar VPN ASA PIX CiscoMauro GuañoNo ratings yet
- Latihan Chek MTP3 Link HuaweiDocument8 pagesLatihan Chek MTP3 Link HuaweiIfank NeutronNo ratings yet
- Huawei AirEngine 5762-12 Access Point DatasheetDocument12 pagesHuawei AirEngine 5762-12 Access Point DatasheetFABIO VICTORINONo ratings yet
- Net StatDocument47 pagesNet StatVeerareddy SabbellsNo ratings yet
- Mobile IP: Discovery, Registration and TunnelingDocument9 pagesMobile IP: Discovery, Registration and TunnelingshaNo ratings yet
- Huawei ICT Competition 2019-2020 Examination Outline - Network TrackDocument4 pagesHuawei ICT Competition 2019-2020 Examination Outline - Network Trackwannes hela100% (1)
- 9.1.1.8 Lab - Examining Telnet and SSH in WiresharkDocument4 pages9.1.1.8 Lab - Examining Telnet and SSH in Wiresharkc583706No ratings yet
- Bulletcat12: Bulletcat12 - Lte Advanced Carrier Aggregation 600 Mbps Cat12 GatewayDocument2 pagesBulletcat12: Bulletcat12 - Lte Advanced Carrier Aggregation 600 Mbps Cat12 GatewayJo AnorienNo ratings yet
- 3.2.4.6 Packet Tracer - Investigating The TCP-IP and OSI Models in Action KIMDocument5 pages3.2.4.6 Packet Tracer - Investigating The TCP-IP and OSI Models in Action KIMKimCanillasVincereNo ratings yet
- Dump-Networking-2022 1008 142341 StopDocument971 pagesDump-Networking-2022 1008 142341 StopobedNo ratings yet
- Seminar ReportDocument20 pagesSeminar ReportthamburuNo ratings yet
- Java Socket Programming Basics PDFDocument11 pagesJava Socket Programming Basics PDFvgrynyukNo ratings yet
- Computer Networking: The Complete Beginner's Guide to Learning the Basics of Network Security, Computer Architecture, Wireless Technology and Communications Systems (Including Cisco, CCENT, and CCNA)From EverandComputer Networking: The Complete Beginner's Guide to Learning the Basics of Network Security, Computer Architecture, Wireless Technology and Communications Systems (Including Cisco, CCENT, and CCNA)Rating: 4 out of 5 stars4/5 (4)
- The Compete Ccna 200-301 Study Guide: Network Engineering EditionFrom EverandThe Compete Ccna 200-301 Study Guide: Network Engineering EditionRating: 5 out of 5 stars5/5 (4)
- Evaluation of Some Websites that Offer Virtual Phone Numbers for SMS Reception and Websites to Obtain Virtual Debit/Credit Cards for Online Accounts VerificationsFrom EverandEvaluation of Some Websites that Offer Virtual Phone Numbers for SMS Reception and Websites to Obtain Virtual Debit/Credit Cards for Online Accounts VerificationsNo ratings yet
- Hacking: A Beginners Guide To Your First Computer Hack; Learn To Crack A Wireless Network, Basic Security Penetration Made Easy and Step By Step Kali LinuxFrom EverandHacking: A Beginners Guide To Your First Computer Hack; Learn To Crack A Wireless Network, Basic Security Penetration Made Easy and Step By Step Kali LinuxRating: 4.5 out of 5 stars4.5/5 (67)
- AWS Certified Solutions Architect Study Guide: Associate SAA-C02 ExamFrom EverandAWS Certified Solutions Architect Study Guide: Associate SAA-C02 ExamNo ratings yet
- AWS Certified Cloud Practitioner Study Guide: CLF-C01 ExamFrom EverandAWS Certified Cloud Practitioner Study Guide: CLF-C01 ExamRating: 5 out of 5 stars5/5 (1)
- CCNA: 3 in 1- Beginner's Guide+ Tips on Taking the Exam+ Simple and Effective Strategies to Learn About CCNA (Cisco Certified Network Associate) Routing And Switching CertificationFrom EverandCCNA: 3 in 1- Beginner's Guide+ Tips on Taking the Exam+ Simple and Effective Strategies to Learn About CCNA (Cisco Certified Network Associate) Routing And Switching CertificationNo ratings yet
- The Ultimate Kali Linux Book - Second Edition: Perform advanced penetration testing using Nmap, Metasploit, Aircrack-ng, and EmpireFrom EverandThe Ultimate Kali Linux Book - Second Edition: Perform advanced penetration testing using Nmap, Metasploit, Aircrack-ng, and EmpireNo ratings yet
- Cybersecurity: A Simple Beginner’s Guide to Cybersecurity, Computer Networks and Protecting Oneself from Hacking in the Form of Phishing, Malware, Ransomware, and Social EngineeringFrom EverandCybersecurity: A Simple Beginner’s Guide to Cybersecurity, Computer Networks and Protecting Oneself from Hacking in the Form of Phishing, Malware, Ransomware, and Social EngineeringRating: 5 out of 5 stars5/5 (40)
- Computer Networking: The Complete Guide to Understanding Wireless Technology, Network Security, Computer Architecture and Communications Systems (Including Cisco, CCNA and CCENT)From EverandComputer Networking: The Complete Guide to Understanding Wireless Technology, Network Security, Computer Architecture and Communications Systems (Including Cisco, CCNA and CCENT)No ratings yet
- Mastering Linux Security and Hardening - Second Edition: Protect your Linux systems from intruders, malware attacks, and other cyber threats, 2nd EditionFrom EverandMastering Linux Security and Hardening - Second Edition: Protect your Linux systems from intruders, malware attacks, and other cyber threats, 2nd EditionNo ratings yet
- Advanced Antenna Systems for 5G Network Deployments: Bridging the Gap Between Theory and PracticeFrom EverandAdvanced Antenna Systems for 5G Network Deployments: Bridging the Gap Between Theory and PracticeRating: 5 out of 5 stars5/5 (1)
- CCST Cisco Certified Support Technician Study Guide: Networking ExamFrom EverandCCST Cisco Certified Support Technician Study Guide: Networking ExamNo ratings yet
- IP Routing Protocols All-in-one: OSPF EIGRP IS-IS BGP Hands-on LabsFrom EverandIP Routing Protocols All-in-one: OSPF EIGRP IS-IS BGP Hands-on LabsNo ratings yet
- The E-Commerce Book: Building the E-EmpireFrom EverandThe E-Commerce Book: Building the E-EmpireRating: 5 out of 5 stars5/5 (1)
- Computer Systems and Networking Guide: A Complete Guide to the Basic Concepts in Computer Systems, Networking, IP Subnetting and Network SecurityFrom EverandComputer Systems and Networking Guide: A Complete Guide to the Basic Concepts in Computer Systems, Networking, IP Subnetting and Network SecurityRating: 4.5 out of 5 stars4.5/5 (13)
- ITIL® 4 Direct, Plan and Improve (DPI): Your companion to the ITIL 4 Managing Professional and Strategic Leader DPI certificationFrom EverandITIL® 4 Direct, Plan and Improve (DPI): Your companion to the ITIL 4 Managing Professional and Strategic Leader DPI certificationNo ratings yet
- Microsoft Azure Infrastructure Services for Architects: Designing Cloud SolutionsFrom EverandMicrosoft Azure Infrastructure Services for Architects: Designing Cloud SolutionsNo ratings yet
- Networking Fundamentals: Develop the networking skills required to pass the Microsoft MTA Networking Fundamentals Exam 98-366From EverandNetworking Fundamentals: Develop the networking skills required to pass the Microsoft MTA Networking Fundamentals Exam 98-366No ratings yet
- FTTx Networks: Technology Implementation and OperationFrom EverandFTTx Networks: Technology Implementation and OperationRating: 5 out of 5 stars5/5 (1)
- Introduction to Cyber-Warfare: A Multidisciplinary ApproachFrom EverandIntroduction to Cyber-Warfare: A Multidisciplinary ApproachRating: 4.5 out of 5 stars4.5/5 (3)